Mobile Application Security: The Ultimate Checklist
Last updated:27 December 2024
Mobile security is a constant issue among many enterprises. As companies continue to go digital and offer online and mobile platforms to their consumers, the rate of mobile security threats multiplies by the day.
Having a mobile application is another means of ensuring that the product and services your company offers are readily available for your customers to consume. Connectivity, accessibility, and convenience are among the many factors entrepreneurs must prioritize to deliver to establish a good relationship with their market.
However, if you fail to properly secure your mobile application and your company, the risk of having sensitive and vital information compromised will significantly damage your reputation and trust in your brand among consumers.
To help you avoid this, we prepare a comprehensive and in-depth checklist of ways to ensure the utmost security for your mobile application and reduce the probability of encountering external cyber threats penetrating your application.
What Is Mobile Application Security?
Mobile app security is a comprehensive mobile security solution for applications on mobile devices such as smartphones, tablets, smartwatches, and the like.
It is like a practice where you ensure that your product is safe from various cyber attacks, such as malware, reverse engineering, keyloggers, data theft, and other forms of manipulation or interference, by implementing the best mobile application security practices available in the market.
Moreover, it involves examining the structures of mobile applications and how they work. It also involves checking the major areas of the application and analyzing what hackers or any external threats want to accomplish by penetrating your application.
The Investment Landscape of Mobile Application Security
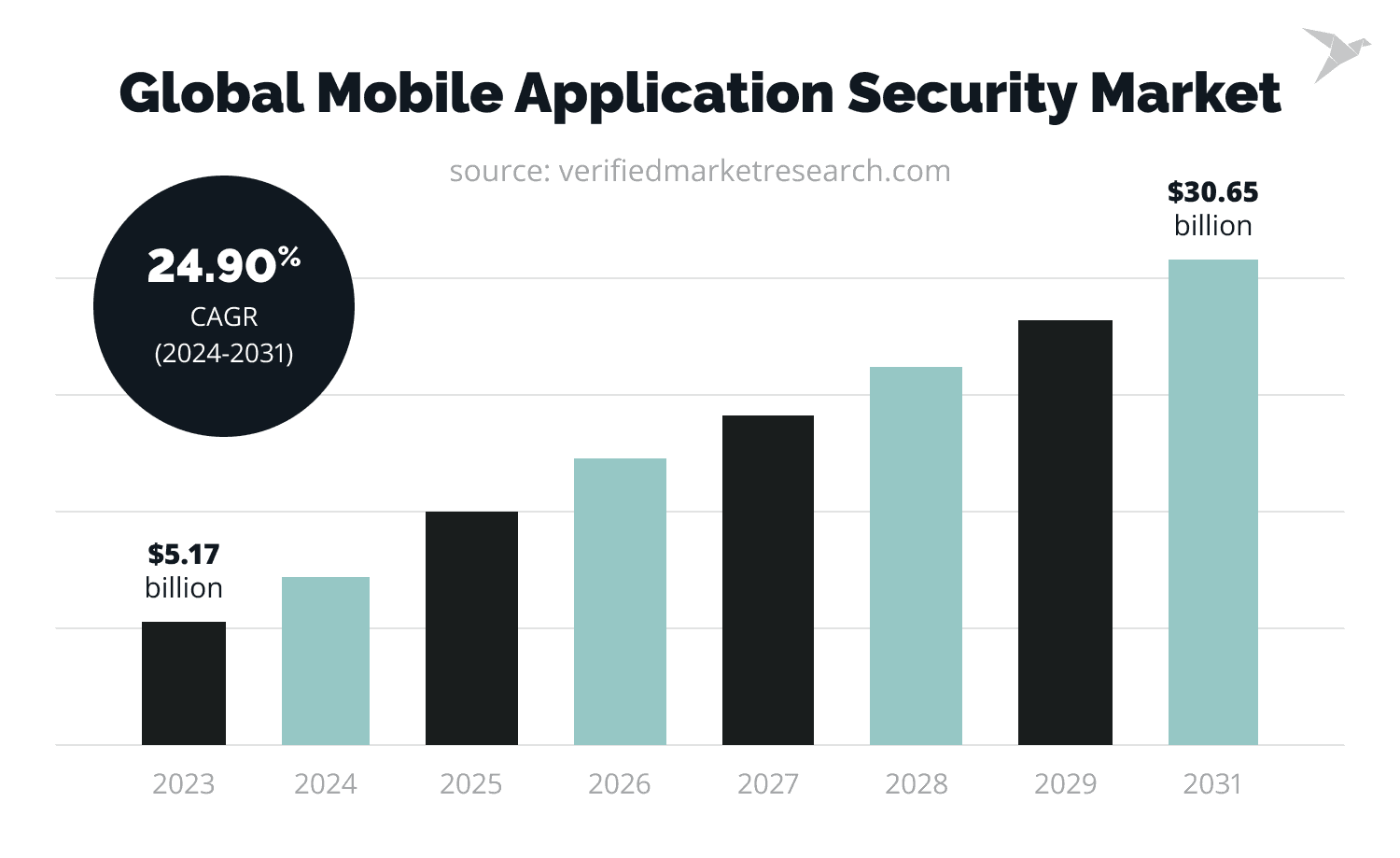
The growing need for companies to establish a secure mobile platform for their users enabled the mobile application security industry to flourish. The rapid shift to digitization worldwide – especially since the onslaught of the COVID-19 pandemic – expedited the industry's growth.
According to Verified Market Research, the mobile application security market is expected to garner $30.65 billion by 2031 with a compound annual growth rate (CAGR) of 24.9%. For comparison, in 2023, the industry stood at 5.17 billion.
Why Is Mobile Application Security Important?
In 2025, there are over 4.88 billion people who own smartphones. This means that approximately 60.42% of the population uses their smartphones and is likely to utilize two or more mobile applications and have incorporated them into their daily functions. Some users own more than one smartphone, which means there are around 7.21 billion active smartphones in the world now.
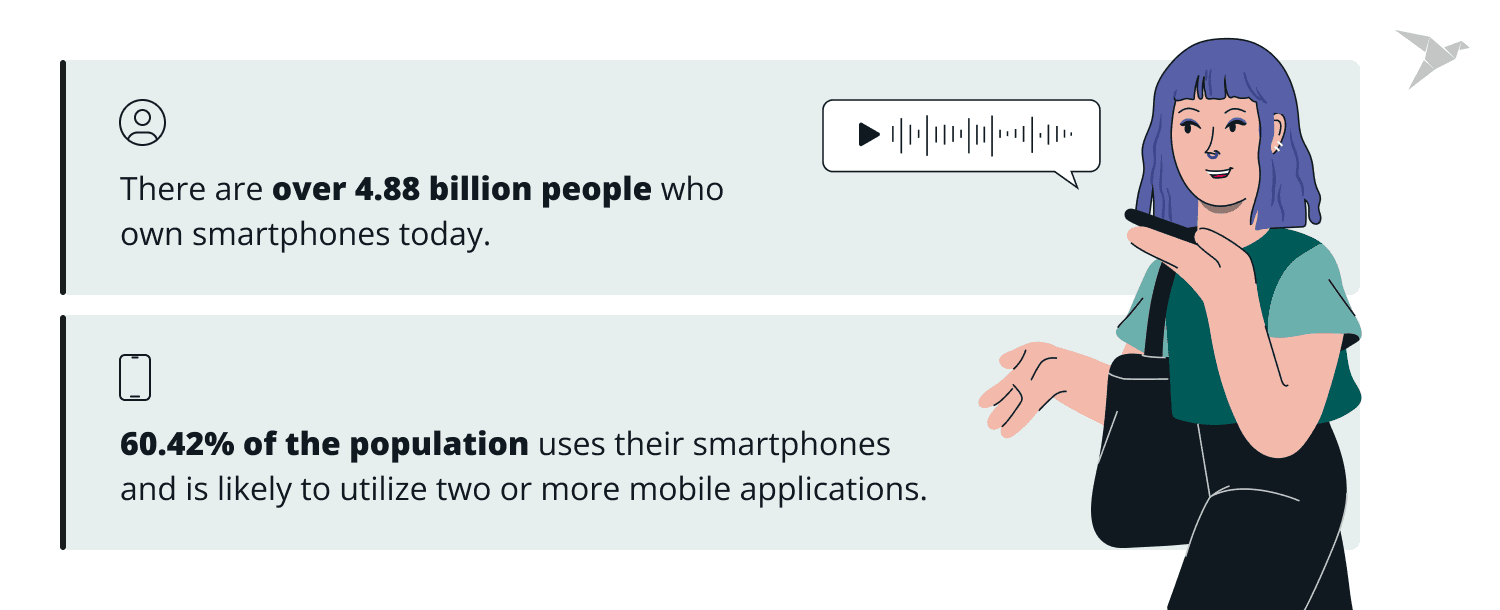
These substantial numbers showcase the potential and importance of implementing application security on active mobile apps worldwide. The lack thereof can compromise your company’s sensitive data and the important data and digital properties your consumers own.
The primary reason for its importance concerns the safety and security of digital properties, such as identities, finances, and sensitive data, to name a few. Ensuring that your business’s mobile application is fully equipped with the right security protocols can help you prevent security breaches that can place you and your consumers at risk.

Global Trends on Cyberattacks and Cyber Threats in Mobile Apps
Cyberattacks and threats are mostly connected to data breaches among mobile devices connected to the internet. Hackers and viruses target domains linked to mobile applications due to their low resilience against cyber threats or attacks.
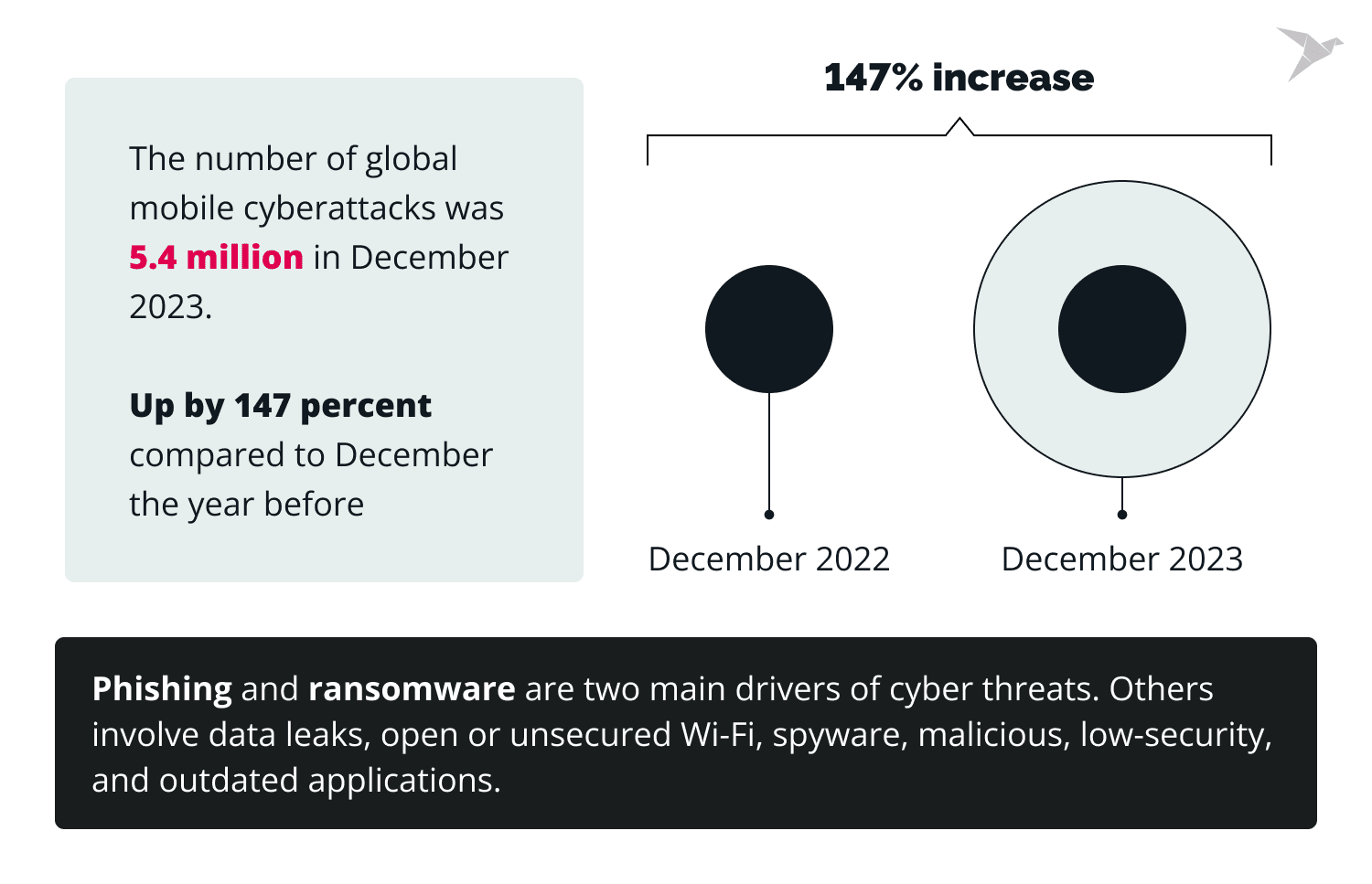
In December 2023, the number of global mobile cyberattacks was approximately 5.4 million, up by 147 percent compared to December the year before. The two main drivers of cyber threats are phishing and ransomware. Other cyber threats toward mobile apps involve data leaks, open or unsecured Wi-Fi, spyware, malicious apps, low-security apps, and outdated applications.
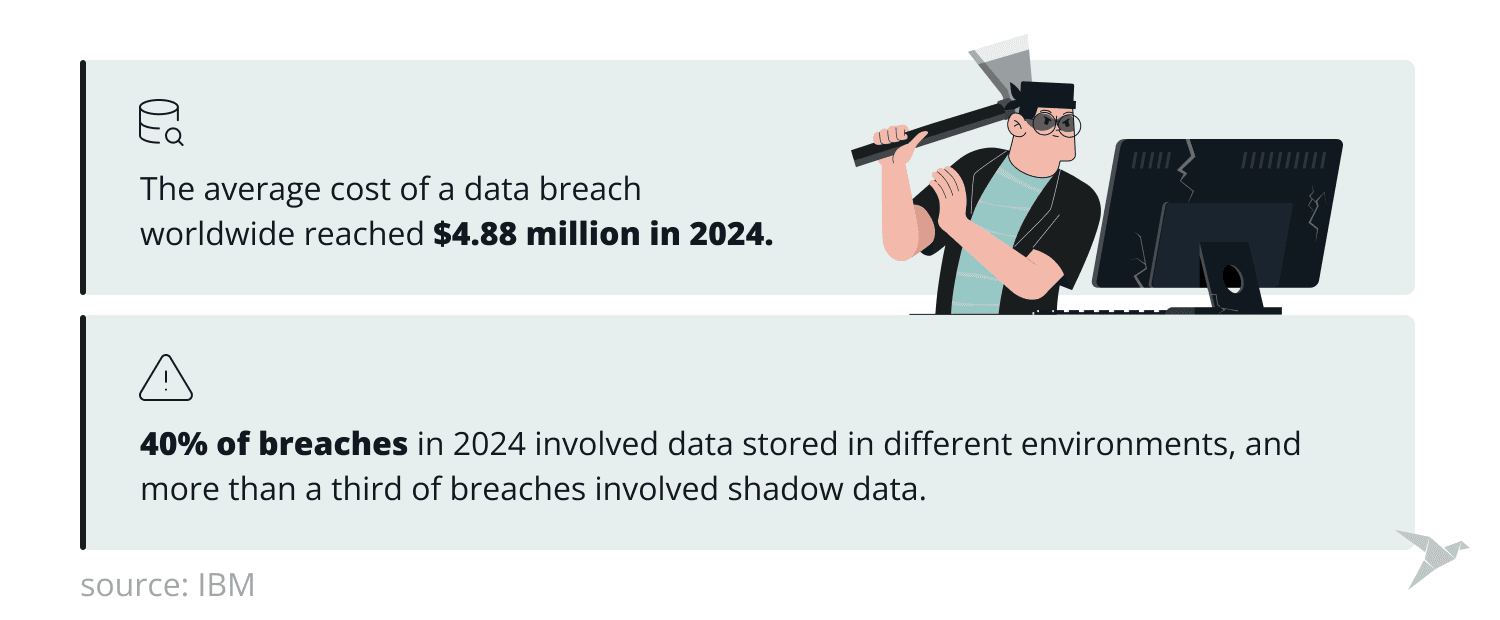
According to IBM, the global average cost of a data breach reached $4.88 million in 2025. Interestingly, 40% of breaches in 2025 involved data stored in different environments, and more than a third of breaches involved shadow data (data stored in unmanaged data sources), which highlights the increasing challenge of monitoring and protecting data.
More than 50% of the organizations that took part in IBM's survey faced severe or high-level security staffing shortages last year and experienced significantly higher breach costs as a result. Namely, the costs reached $5.74 million for high levels and $3.98 million for low levels or none. This happens because organizations are rushing to adopt generative AI technologies, which are expected to create new risks for security teams.
At the same time, IBM's report revealed that 67% of organizations have deployed AI and security automation, an increase of almost 10% from the previous year. 20% said they used some form of AI-based security tools.

Organizations that use AI and automation in security identify and remediate incidents 98 days faster on average than organizations that do not use these technologies. Companies implementing security AI and automation to prevent breaches can significantly cut breach costs. The average cost savings reaches $2.22 million.

The Common Mobile App Security Threats
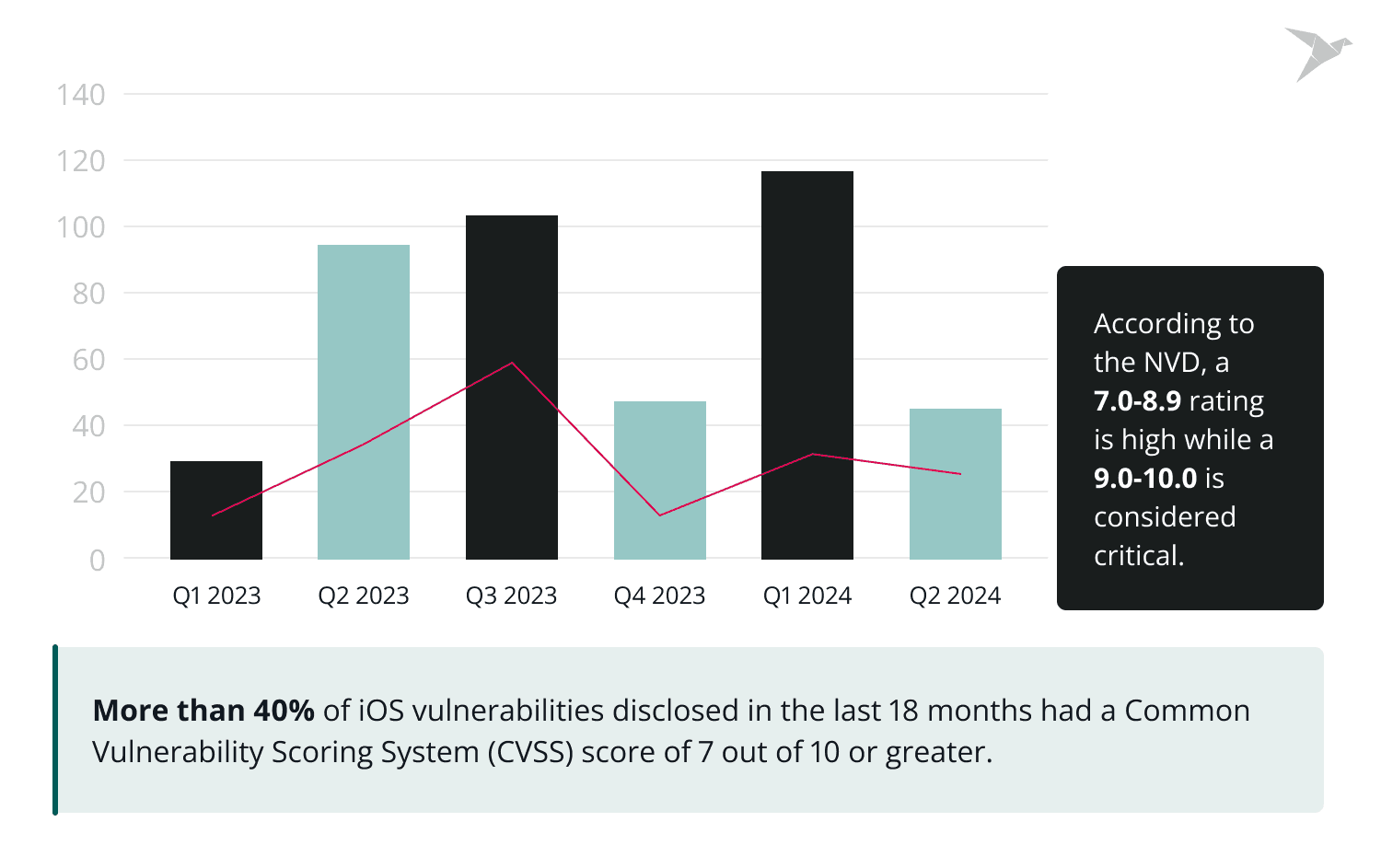
As of August 2024, internet users worldwide detected 52,000 new common security vulnerabilities and exposures (CVEs). To help you better understand security threats towards mobile apps, we listed the most common mobile app security issues and threats and how you can avoid or prevent them from happening to your organization.
Malware
Malware is one of the most common cyber threats that mobile apps face daily. This intrusive software is designed to damage and destroy the internal systems of the user's device or computer. Moreover, it can explore, steal, and conduct various behaviors controlled by an attacker.
In a report conducted by Verizon, approximately 86% of users were worried about malware, while 20% were unprepared to defend their devices against it. There are about 2,244 malware attacks online every day, with a new attack occurring every 39 seconds. Every day, 30,000 websites are hacked globally, and 300,000 new malware programs are created.
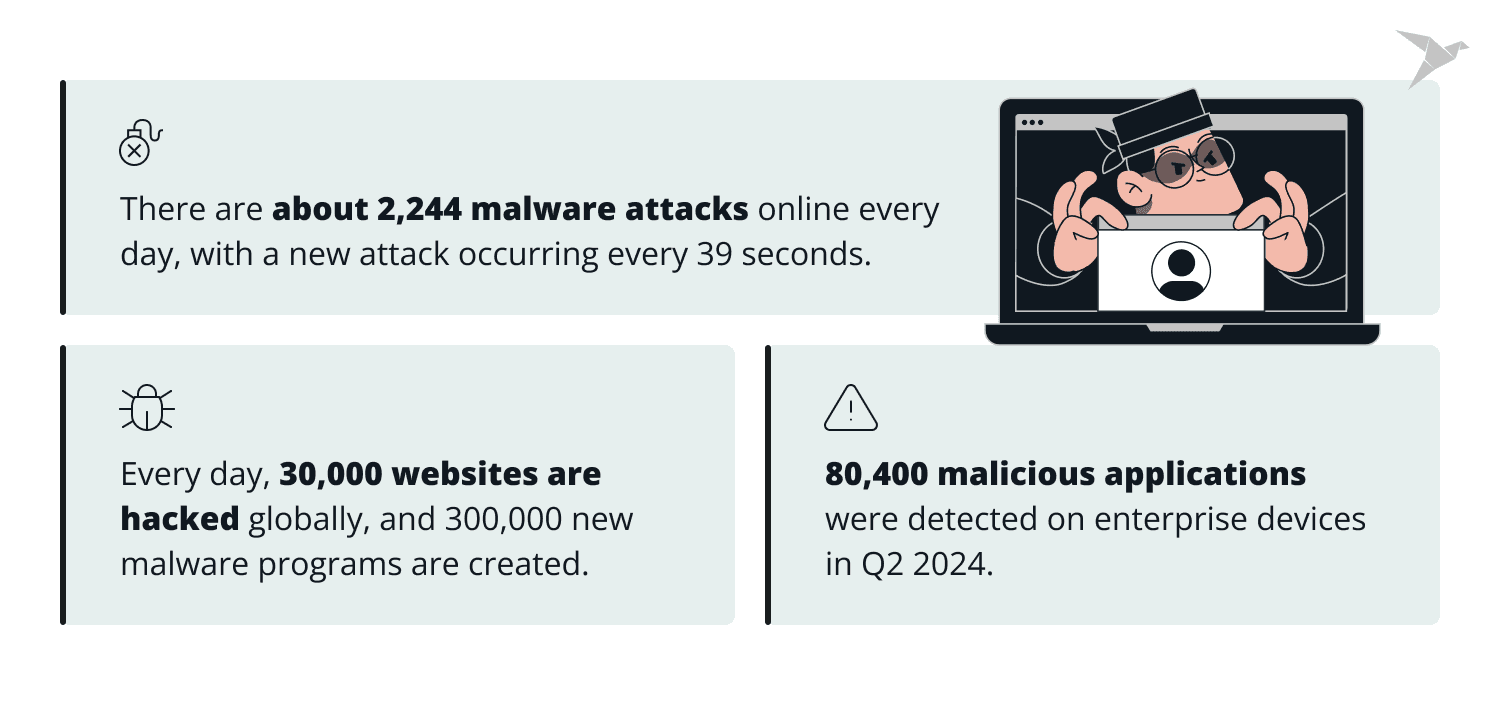
As technology and digital spaces evolve, malware grows more sophisticated and complex. According to the 2024 Mobile Threat Report, 80,400 malicious applications were detected on enterprise devices in Q2 2024.
Join our upcoming webinar to get practical guidance before your next audit
Ransomware
Another common threat in the mobile app industry is ransomware. A more specific type of malware, ransomware, is a set of malicious programs that penetrates your device and disables access until you pay a certain amount to the hacker.
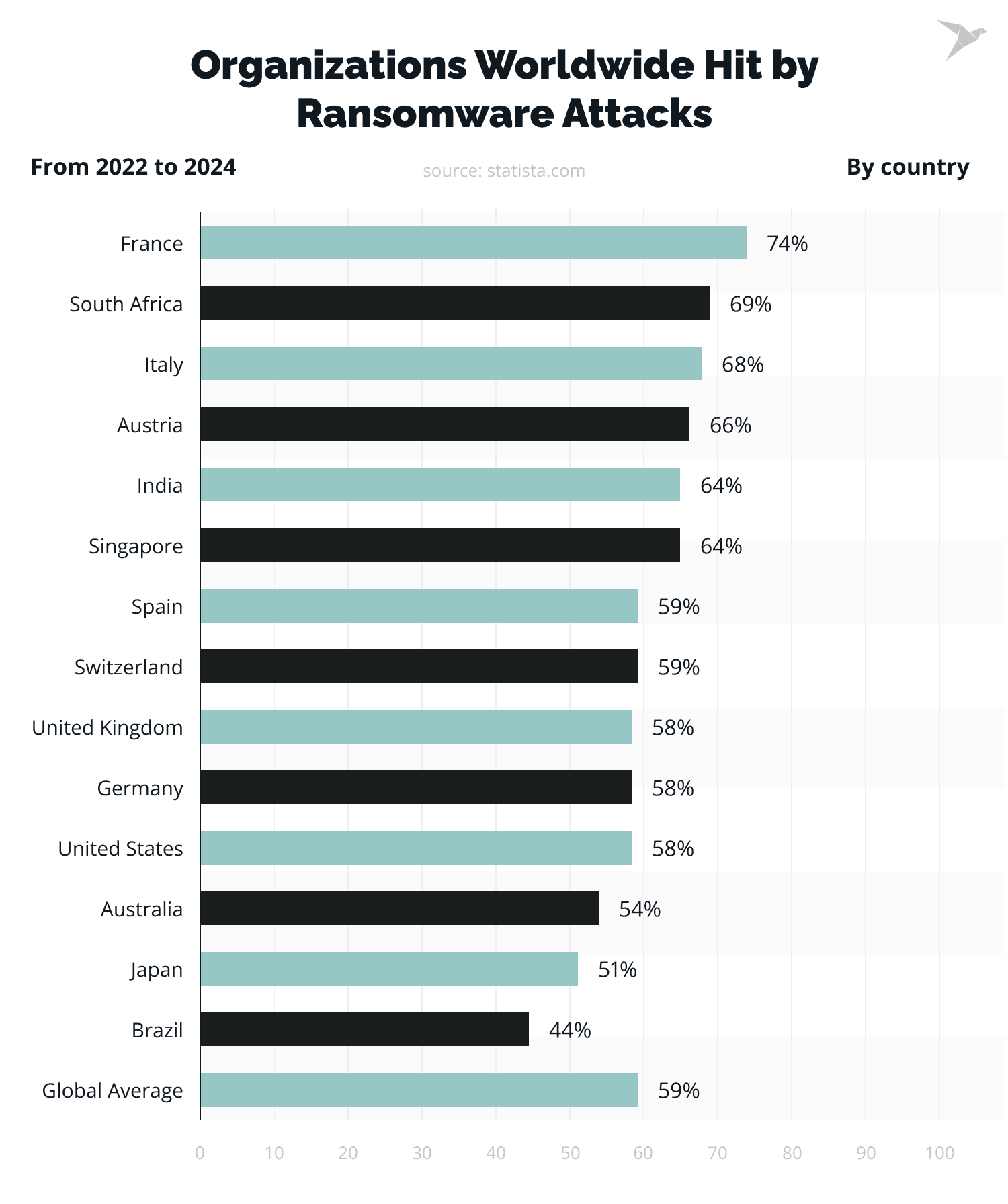
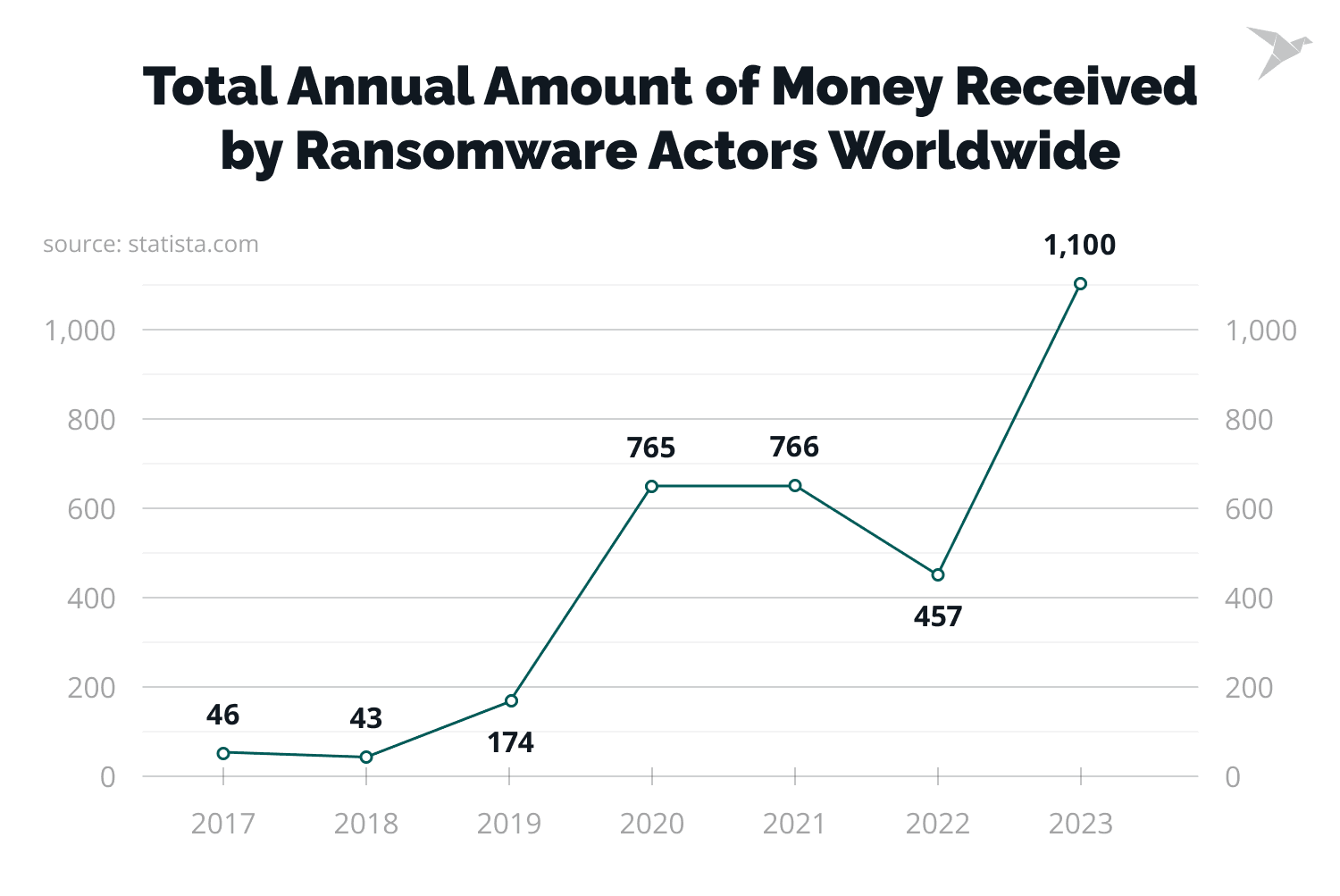
In short, ransomware is similar to real-life ransoms, but instead of a person, it is your device that is held hostage by external captors. Such cyber threats are complicated and expensive to remove. Ransomware is the most preferred method of cyberattacks. In 2023, companies worldwide reported 317.59 million ransomware attempts.
Ransomware is the most preferred method of cyberattacks. In 2021, around 37% of global organizations have been ransomware victims. In the US, the FBI's Internet Crime Complaint Center reported 2,084 ransomware complaints on mobile apps from January to July 31, 2021, representing a 62% year-over-year increase.
Cryptojacking
Crypto mining and cryptocurrencies are gaining steady popularity worldwide. Businesses, financial institutions, and the like are slowly adopting crypto and its principles. Cryptojacking is another cyber threat that attacks your devices and uses their computing power to mine cryptocurrency.
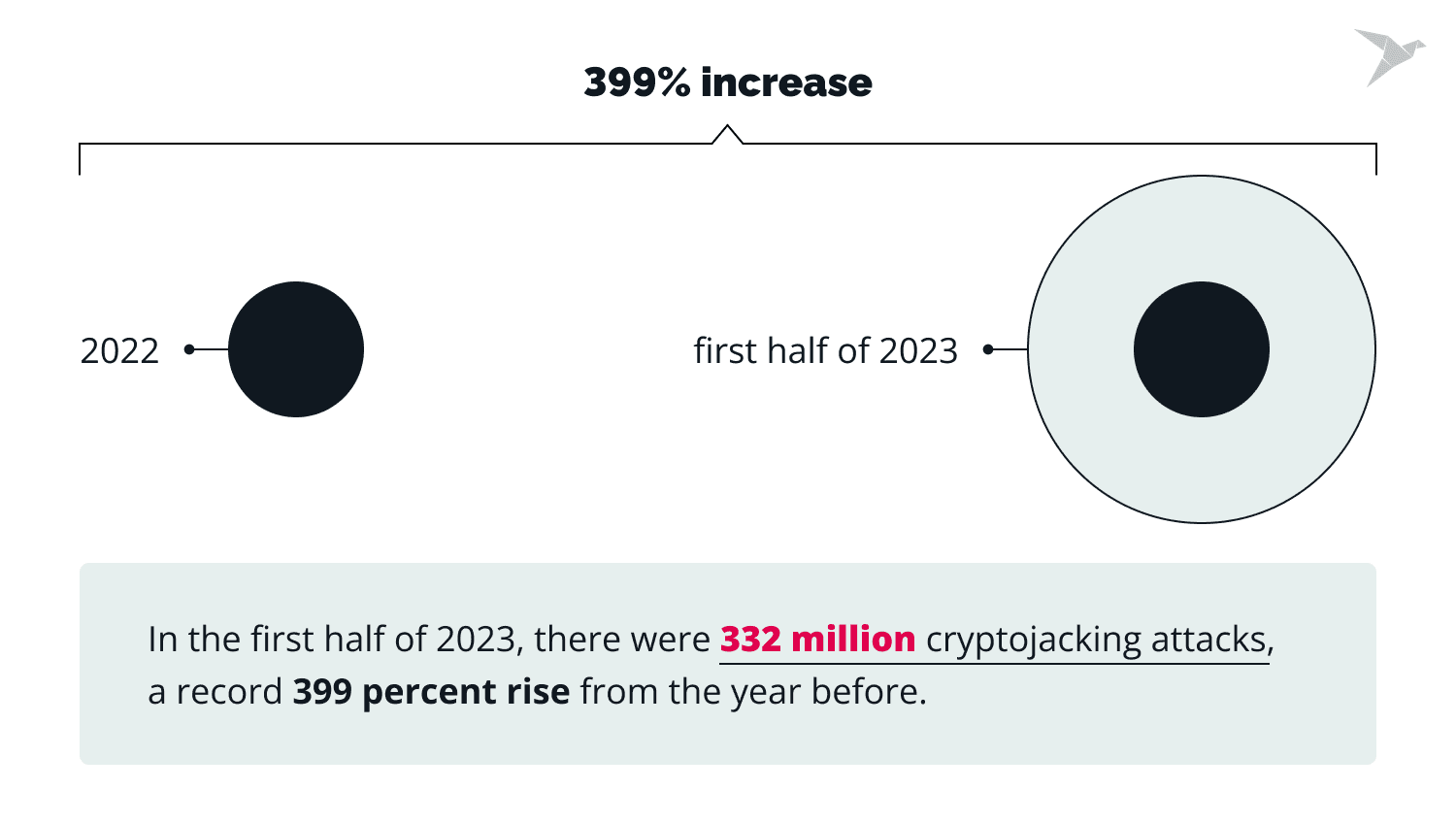
Victims who are attacked by cryptojacking experience rapid battery drain, device downtime, and operational disruption. Around 73% of organizations report concerns about cryptojacking and have experiences with such issues. In the first half of 2023, there were 332 million cryptojacking attacks, a record 399 percent rise from the year before.
Insecure coding
Failure to apply the best practices of mobile app development. Doing so can leave gaps within your code that can be easily infiltrated by hackers and other cyber threats that want to penetrate your app.
How Mobile Applications Are Penetrated by Cyber Threats
Cyber threats can be mitigated if addressed correctly. That is why it is imperative to deeply understand mobile app security and how hackers and other cyber attacks work to infiltrate your application. Here are some ways hackers can exploit when hacking your mobile app.
#1: Weak server-side controls
A majority of mobile applications operate on client-server architecture. It is a computing model that allows multiple components to communicate in strictly defined roles. Here, the servers host, deliver and manage various client resources and services. Application stores like the Google Play store operate in a client-server architecture to deliver various mobile applications to users.
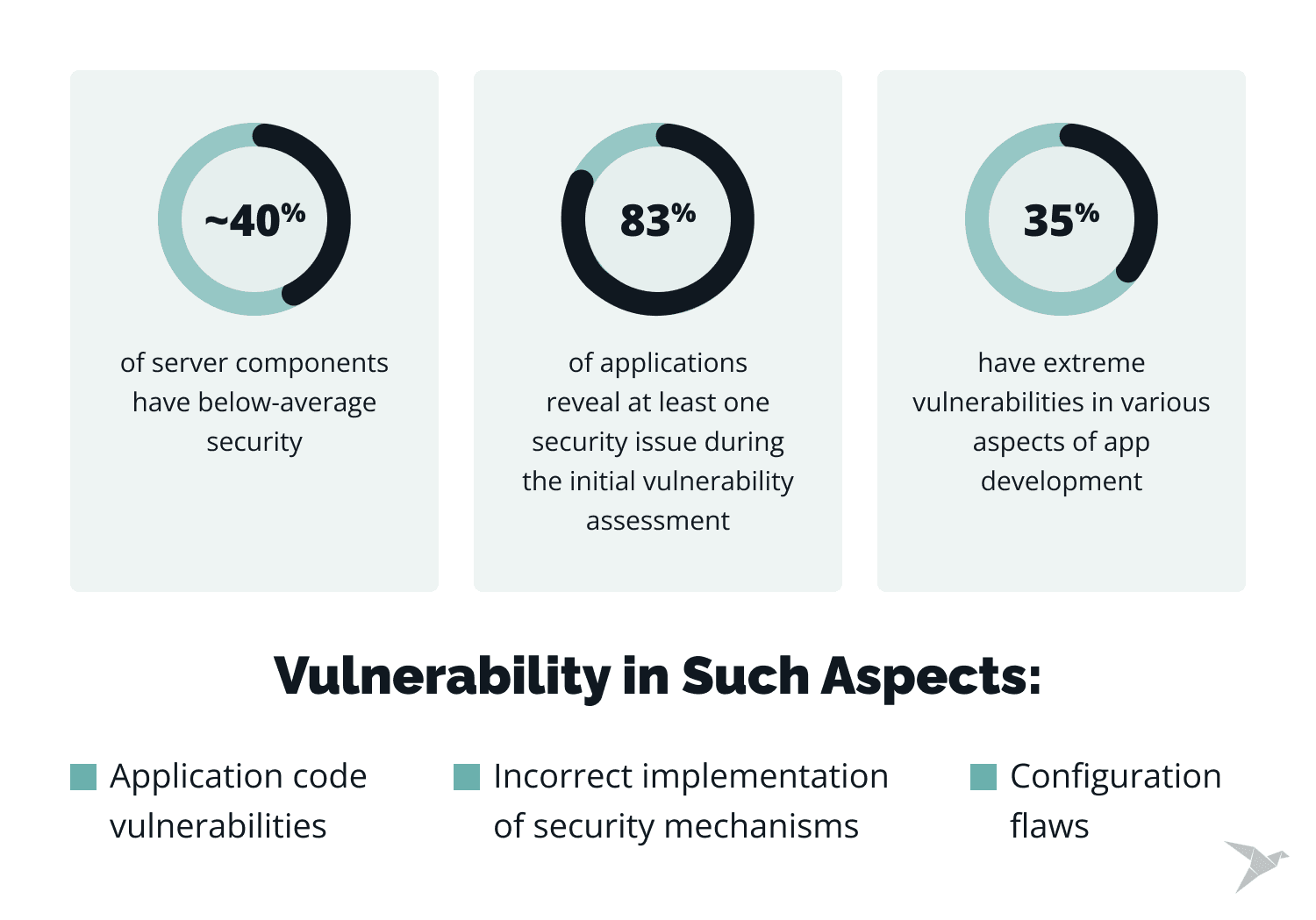
Mobile app developers are in charge of handling the servers. They interact with the mobile device through APIs, which are responsible for the correct execution of app functions. According to the report, 83% of applications reveal at least one security issue during the initial vulnerability assessment. The common vulnerabilities are:
- Configuration flaws
- Application code vulnerabilities
- Incorrect implementation of security mechanisms
#2: Insecure data storage
A factor of digitization includes the need to explore various storage spaces to expand the capabilities of products for their users. Today, both traditional storage and cloud-based storage in local file systems are maximized.
A cloud-based storage system is more efficient, convenient, and accessible to people who need specific data at any time. That said, cloud-based storage systems can have inefficient and flawed security methods, placing vital company and consumer data at risk.
Around 43% of organizations overlook mobile app security to achieve a quicker time-to-market for their products. Although bringing your product sooner to your market may be beneficial, it may be counterproductive if your application becomes untrustworthy to your target audience.
Insecure data storage also affects local databases. These are usually used by the application's local databases (SQLite), which are stored on the device after installation. Data storage with low-quality security measures can place the data stored in an application's local database at risk, allowing attackers to obtain access or control the device through mobile malware or spyware. Attackers can also obtain all of the available intellectual property stored by the application on the device.

#3: Insufficient Transport Layer Protection (TLS)
Insufficient Transport Layer Protection (TLS) is a security weakness caused by applications lacking measures to safeguard network traffic. While mobile app data is exchanged through a client-server architecture, the data is transferred through an end user’s carrier network or the Internet.
Mobile apps that lack security can be vulnerable to threat agents that exploit and misuse the data while it traverses across the network. Here, hackers and other cyber threats can expose confidential information stored over WiFi or local networks.
This can expose a user’s confidential information, leading to account or identity theft, site exposure, phishing, or man-in-the-middle attacks. Your business could be subject to privacy violations, fraud, and reputational damage when this occurs.
How Mobile App Security Works
Although users are the primary suspects of cyber crimes, they are not the only ones greatly affected by such acts. Numerous companies and organizations suffered tremendous damage from cyber attacks that led to data leaks, infrastructure exposure, scams, and issues with regulations and guidelines.
Prevent leakage of sensitive information
Applications that lack firewalls and the necessary security measures to keep their IOS or Android apps safe tend to suffer from information, data breaches, and leakage.
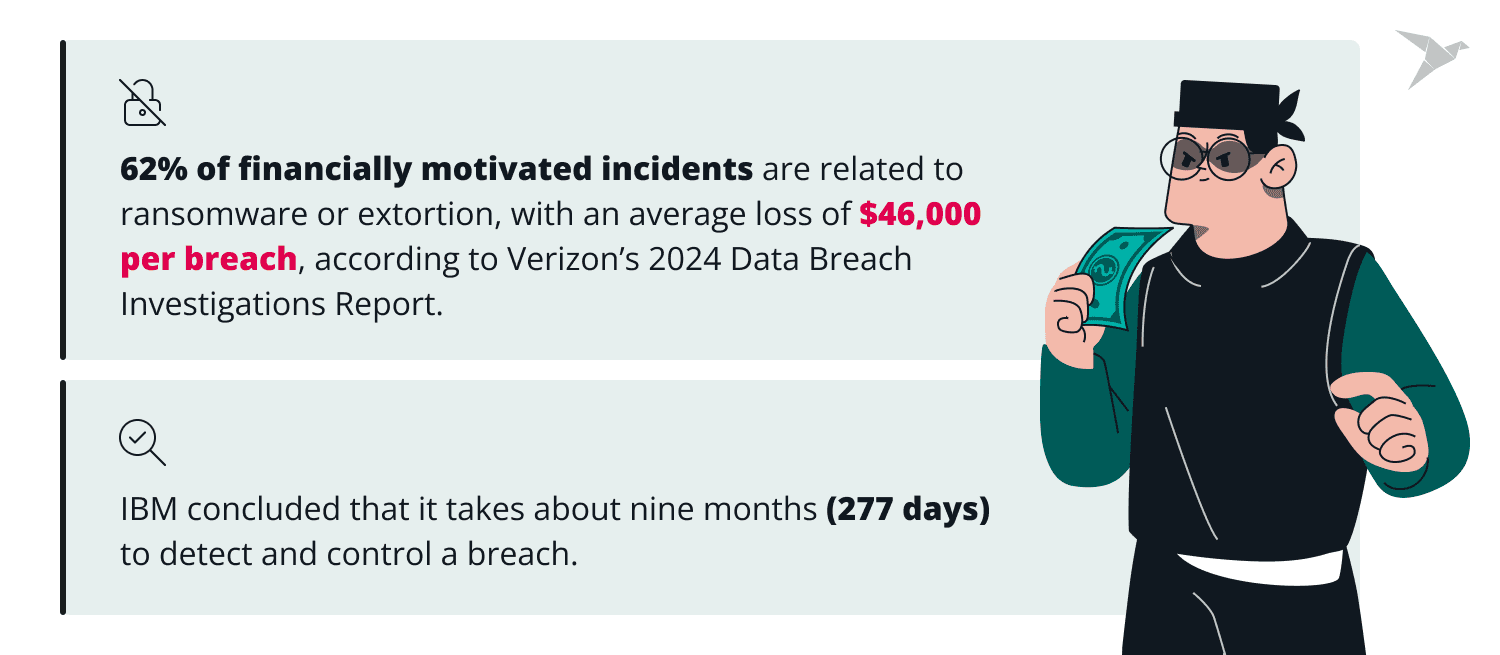
According to Verizon’s 2024 Data Breach Investigations Report, 62% of financially motivated incidents are related to ransomware or extortion, with an average loss of $46,000 per breach. IBM concluded that it takes about nine months (277 days) to detect and control a breach.
By implementing a robust security system, conducting regular penetration testing, and overall security checks across your mobile applications, you can avoid incurring the same issue and save from having unwanted charges over legal malpractice on data safety and security.
Safeguard company software infrastructure on mobile devices
Infrastructure exposure could become an immense threat to your company as hackers and other external threats can use this information to manipulate and threaten data storage and server-level security.
Prevent phishing or scamming crimes
Fraudulent mobile app security test acts such as scamming or phishing are evident among applications that deal with financial or monetary transactions. Implementing well-rounded, secure mobile apps can identify vulnerabilities and prevent hackers from hijacking your application and placing your user’s digital and financial properties at risk.
Compliance with data regulations and guidelines
Ensuring your company fully complies with relevant data laws, guidelines, and regulations is essential. With proper mobile security, you can ensure data protection standards are met.
The Different Types of Mobile Security
Let's explore the four types of mobile app security models and how vendors can combine cloud-based threat defense with an on-device mobile security framework.
#1: Traditional signature file antivirus approach
Traditional antivirus software is a program designed to prevent, detect, and mitigate malware threats and functions. IOS and Android devices are generally void of the need to implement antivirus software, given that their operating system already has one. That said, to exploit vulnerabilities and protect mobile apps, incorporating a traditional signature file antivirus is one of the ways vendors prevent malware and other cyber attacks from reaching their mobile apps.
The traditional signature file antivirus model creates a signature file on the device where all apps and documents are compared. However, as mobile IOS and Android apps and devices evolve, the approach's effectiveness has diminished over time.
To ensure that the Traditional Signature File Antivirus approach is fully maximized, it must deliver the following security features:
- High Performance and Intended Function
- Inherent Persistence
- Flexibility
#2: Hybrid-AI cloud security
Hybrid-AI Cloud Security involves software-defined networking (SDN), virtualization, and application support across all layers of the product or service. This method protects app security data, applications, user devices, and infrastructure associated with IT architecture. It also incorporates workload portability, orchestration, and management across multiple IT environments with at least one private or public cloud.
Implementing hybrid AI cloud security can significantly reduce your data's exposure to cyber threats. An app developer can keep sensitive and vital data away from the public space while taking advantage of the cloud for data with little to no risks.
#3: Intermediary cloud approach
Through this model, any files users receive, download, and store within their devices are automatically uploaded to a cloud service where the files will be tested and compared. This determines if the files contain – or the file itself – malware or security threats.
This approach is ideal for mobile devices consistently connected to the internet or mobile data. On the other hand, devices with weak and slow networks can suffer or lag in performance. This method has the potential to run fast and extensive processes on high-powered cloud servers, which can eliminate the restrictions of on-device resources.
#4: Mobile behavioral analysis
The mobile behavioral analysis approach is an AI-based preloaded application that prevents malicious activity within a mobile device by flagging suspicious behavior and intellectual property theft. Although most of its functions happen locally within the device, a part of this approach uses a cloud-based component where the agent occasionally downloads new suspicious behaviors to flag on the device.
This process is one of the best ways to find zero-day exploits, using crowd-sourcing to obtain and test files. However, its process is closer to a behavior-based approach than a simple penetration testing associated with the traditional signature file antivirus approach.
The OWASP Mobile Security Testing Standards
To avoid compliance issues, enterprises and development teams venturing into securing mobile applications with the highest security level must acknowledge standards when conducting tests and security implementations. As a mobile application security professional team, we know that it is best to follow Open Web Application Security Project (OWASP) standards when conducting mobile penetration testing.
OWASP is a nonprofit organization that works to improve the security of software. It takes advantage of community-led open-source software projects to implement improved security across software and technology.
When implementing a security system for your mobile application, following the OWASP Mobile Security Testing Guide, a comprehensive manual for mobile app security testing and reverse engineering, is best. It describes technical processes for verifying the controls listed in the OWASP Mobile Application Verification Standard (MASVS).
What Is Mobile Application Security Testing?
The rise of mobile devices has increased in recent years. It has become a critical part or function that significantly contributes to our everyday lives. According to Statista, the mobile app market reached $522.67 billion in 2024.
However, despite the growing need for secure mobile applications and their relevance in the current way we do business and work, many developers consider mobile app security testing at the end of the software development lifecycle.
For robust and effective mobile app security testing, it is ideal to conduct it early to quickly identify the weaknesses, vulnerabilities, and threats that impact an app. There are several ways to test your mobile application’s security. Here are the most common ways to go about it:
Penetration testing
Penetration testing, also known as pentesting, is one of the most common ways to test the security and functions of a mobile application during its development. It is one of the quickest ways to get valuable initial outside assessments of your mobile application.
Here, security professionals perform intentional attacks and threat simulations to test mobile applications' security and seek exploitable vulnerabilities in systems, networks, websites, and applications.
Automated mobile application testing
Automated mobile application security testing is another way to test your mobile security. This method detects an app's security, privacy, and code quality issues on third-party app stores such as Android and iOS applications. Numerous automated tools like runtime application self-protection (RASP) available today can analyze your application's source code while performing dynamic analysis on the application's behavior. This method is also known as white-box testing.
It also takes advantage of the support of automated tools, which can be integrated into the software development life cycle as part of its continuous integration and delivery process.
Alternatives for mobile security testing
There are many other ways to conduct mobile app security testing. Other alternatives vary from Bug Bounties to crowd-sourced app security testing. Using third-party programs to find vulnerabilities must complement internal security practices like threat modeling, code reviews, and automated security testing.
The Techniques of Mobile Application Security Testing
Static analysis
This testing approach focuses on the code-based representation of an application. This can be done by directly inspecting the source code or compiling the application and its resources to inspect security controls thoroughly.
Usually, the static analysis approach uses a hybrid automatic/manual approach. Through this, testers can analyze and determine the “low-hanging fruit,” while the manual approach explores the code base with specific usage contexts.
Dynamic analysis
The dynamic analysis security testing approach tests and evaluates applications during their real-time executions. This approach aims to spot potential vulnerabilities as the program runs or executes its functions.
Security teams identify behavioral differences for different target platforms or runtime. Moreover, it is generally used to test security mechanisms that protect against different types of attacks, such as disclosure of data in transit, injections, biometric authentication and authorization issues, and server configuration errors.
The Legal Aspects of Mobile Security
A part to keep in mind when developing your mobile application is the data privacy and security regulations on various industries that may apply to your mobile application. This can be an exhaustive process as it takes a lot of effort to ensure that your application fully complies with industry regulations.
Check out four main industries that host various compliance regulations on mobile applications, along with the regulations that companies must comply with.
MarTech
Marketing technology is the software and tools that allow businesses to achieve marketing goals. This includes conducting campaigns, collecting information about prospects, and tracking results. According to the Chief Marketing Technologist, the marketing technology landscape hosts around 7,000 products in the industry. Mobile applications created with MarTech in mind should ensure that their mobile application complies with the following regulations:
- GDPR Regulation
- CCPA Regulation
Penetration testing for Coach Solutions web application

FinTech
The fintech industry is new tech that includes web and mobile applications and other technological solutions that modernize traditional financial services. Various regulations for mobile applications dive into the Fintech landscape. Such regulations are as follows:
- The GDPR Regulation
- The ePrivacy Regulation
- The New Payment Services Directive (PSD2)
- Cybersecurity Regulations
HealthTech
Since the emergence of the COVID-19 pandemic, health professionals and entrepreneurs have provided new ways to deliver health and wellness services online. Telemedicine is one of the biggest examples of the health industry jumping into the digitization bandwagon.
In Europe, before mobile applications qualify and are required to comply with regulations, one must ensure that their product identifies as a Medical Device Software (MDSW). Once you meet such requirements, it is best to keep these regulations in mind:
- EU Regulation 2017/745 (MDR)
- EU Regulation 2017/746 (IVDR)
- HIPPA Regulation
Moreover, they provide different standards and criteria for medical software products:
- Medical Devices
- ISO 13485
- IEC 62366
- Health Informatics
- ISO TS 25238
- ISO 14971
- Medical Device Software
- IEC 62304
HRTech
Tech companies have been innovating HR technology and strategies and carried them over into the digital scene. This enables recruiters, HR managers, and entrepreneurs to streamline, take advantage of current recruitment strategies, and maximize their talent pool.
Generally, these are the regulations you should look out for when making an HR-driven mobile application:
- EEOC
- Fair Labor Standards Act
- Family and Medical Leave Act (FMLA)
- Health Insurance Portability and Accountability Act (HIPAA)
A Full Mobile Application Security Checklist
Keep reading, and learn a comprehensive checklist on conducting successful mobile app security testing.
#1: Enforcing a robust authentication process
Most organizations suffer from data compromise due to unauthorized access and passcode guessing attacks. The ideal way to counter this is to provide a robust authentication system, such as multi-factor authentication, to protect data and reduce the risk of data compromise within your organization.
Multi-factor authentications combine your usual pin or password authentication process with another set of authentication that is usually more complex such as fingerprint or biometrics authentication or one-time passcodes. Implementing time-of-day and location-based restrictions to prevent fraud.
#2: Encrypt mobile communications
At present, numerous threats have become more complex in penetrating and analyzing the content of sensitive data of your company and your consumers. Threats such as snooping and man-in-the-middle attacks over Wi-Fi make it difficult for enterprises to fully secure their apps without proper mobile app security operating systems.
To avoid this, it is ideal to encrypt your mobile communication channels to avoid cyber threats. Strong encryption that leverages 4096-bit SSL keys and session-based key exchanges can prevent even the most determined hackers and complex malicious software from decrypting communications.
You can also take advantage of SSL Certificate Pinning to encrypt communications. It is a technique to prevent applications' dangerous and complex security attacks. This method pins the identity of trustworthy certificates on mobile apps and blocks unknown documents from suspicious servers.
#3: Implement comprehensive logging and monitoring
Insider abuse is inevitable in the digital age. Sometimes, you encounter legitimate users who try to infiltrate and abuse your system to compromise and expose the company's sensitive data.
Enforcing and maintaining a detailed audit trail across all transactions made by your consumers. It is an ideal method to detect accidental data leaks and malicious functionality attacks. Moreover, data compliance regulations require companies to maintain a user monitoring system to track access and changes to private data.
#4: Provide frequent patches for app and operating system vulnerabilities
Keeping your operating system or application updated is crucial to keep your platform safe from cyber attacks. As mentioned before, cyber attackers have become increasingly more complex. Ensuring that your systems are regularly updated and compliant with current industry security trends.
Although it is the customer’s responsibility to ensure that their application or device operating system (OS) is up-to-date, providing the option to update them can help push your consumers to update their device’s OS to the latest version.
To further ensure that your consumers use the latest and safest version of their OS or application, you can set your requirements to specified OS versions. This allows you to ensure that your application only runs on a specified OS void of critical vulnerabilities.
#5: Regularly scan your mobile app for malware
Regularly scanning your mobile app for any malicious software that may have been lingering inside can help you prevent incurring any damaging attacks or data breaches within your application. Malware analysis can be detected using virtual sandboxing or signature-based scanning tools. Moreover, AI-powered behavior-based AV solutions do not rely on the signature itself. You can easily change the signature of the malicious app by applying encoding and obfuscation.
These scans can help you spot and identify potential attacks or any suspicious activity within your mobile app. Scanning your server for potential threats is also ideal for preventing malware or similar threats.
Final Thoughts
As the world becomes more reliant on technology and mobile applications, take the time to assess and ensure that your mobile application is fully secured from security vulnerabilities and compliant with relevant regulations.
Moreover, having a threat-resistant mobile application against malware, cyber attacks, hackers, and similar can help you ensure that your company data (as well as consumer data) is safe from those who want to exploit and compromise your organization.
At present, numerous commercial mobile application security tools are readily available. If you find it challenging and are unsure which tools best fit your needs when developing secure applications, you can reach out to us at TechMagic.
FAQ

What is mobile app security?
Mobile app security is where you safeguard high-value mobile applications, digital properties, and identities from fraudulent acts and cyber attacks.
How does mobile app security work?
Mobile app security employs various techniques such as encryption, authentication, secure coding practices, and regular updates. These measures prevent unauthorized access, data breaches, malware, and other security risks.
Why is mobile app security important?
Ensuring that your mobile application is fully equipped with a robust security system helps avoid damaging issues that can place your organization at risk. Moreover, it keeps sensitive data, app infrastructure, and similar safe from exploitation and exposure.
What is mobile application security testing?
Mobile application security testing is a process of assessing the security of your mobile application through various methods such as penetration testing, automated scanning using industry-recognized tools, etc.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy