Importance of Security in Serverless Technologies

Director of Cloud and Cybersecurity, AWS Expert, big fan of SRE. Helps teams to improve system reliability, optimise testing efforts, speed up release cycles & build confidence in product quality.

Serverless architecture: serverless security market, threats, best practices and enhancements, and biggest trends in 2022.
Serverless architecture allows a company to focus on innovative and creative, leaving the tedious routine work to remote overseas experts. When outsourcing mundane tasks to remote teams, you can channel your energy toward user experience instead of taking care of managed infrastructure. It gives you creative freedom, lowers costs, shortens time to market, saves essential resources, and enables scalable platforms.
However, while serverless architecture has shown to be in high demand, it comes with its risks and disadvantages. Which pitfalls should you avoid, and which serverless risks should you mitigate to build a stable serverless system? In this article, we will discuss the challenges of serverless security.
What is The Model Of Security in Serverless Architecture?
Serverless Architecture enforces a brand-new value system — the shared responsibility model. Within this concept, the cloud vendor and the developer share the responsibility throughout the entire workflow.
The cloud provider is liable for the serverless web application security of cloud components — the vendor stores data, monitors network elements, takes care of the operating system. The developer is responsible for what’s in the cloud — the customer secures application logic and code as well as customer data. This serverless app security model for serverless computing creates a joint responsibility that inevitably complicates the process.
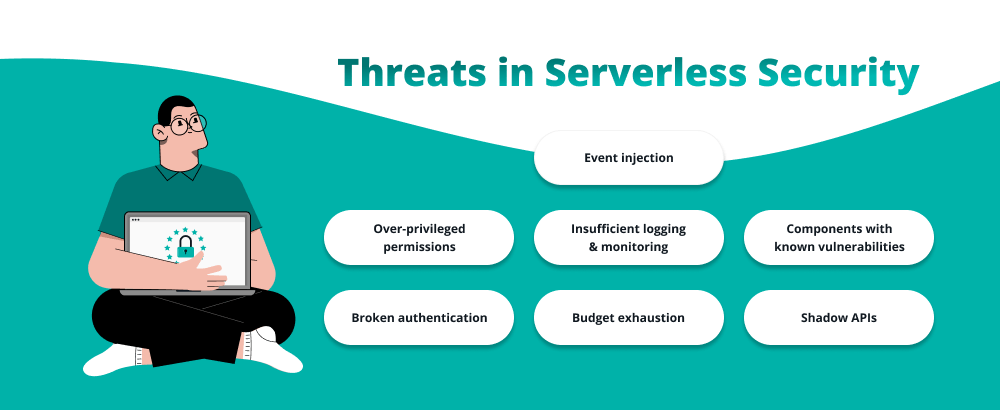
Threats in Serverless Security
Event injection
First, the development team can’t keep all the nuances of serverless architectures in mind as opposed to the common web climates where they are aware which events inputs should not be trusted. Second, SA provides a large scope of event sources that can set off a serverless function. Once a dubious input gets executed, it’ll lead to an event injection.
Over-privileged permissions
Another threat that serverless architecture brings to the web app is the over-privileged functions. When granting permissions for particular serverless functions, be sure to minimize them according to the task assigned. On top of that, constantly monitor the functions for suspicious activities to avoid security breaches.
Insufficient logging & monitoring
Any application has to have a sustainable monitoring and logging mechanism. The lack of such systems might lead to unwanted charges in your AWS check (e.g., for AWS Lambda plugins installed by some employees without disclosing it). Moreover, if your application breaks or any malicious activity is in progress, you will have no clue what went wrong and how to secure serverless implementations in such a case to prevent further incidents from happening.
Components with known vulnerabilities
Being commonly small and closely connected to micro-services, serverless functions employ a myriad of third-party libraries, dependencies, and other minor components to handle needed tasks. This spawns many common risks of serverless security for the web application. They may include third-party dependency updates that may call for extra code testing and editing, supply chain vulnerabilities (hackers may exploit the code of vulnerable libraries to “invade” the application), and risks related to introducing new code components (each increases the rates of possible vulnerabilities further).
Broken authentication
Since an application is available in the cloud, anyone can attempt to access it, regardless of their intentions. Your goal is to provide a good user experience to the customers while also cutting off unwanted guests. Serverless applications are highly accessible, making them an easy target for hackers, unlike traditional server-based platforms.
Budget exhaustion
Autoscaling is one of the best features of serverless architecture, allowing you to pay only for what you actually use through automated scaling. However, it puts the serverless application security functions in jeopardy by triggering the new generation of cyberattacks called Denial of Wallet. It creates the flow of fake requests which invokes automated upscaling and exhausts your budget.
Shadow APIs
Uploaded to the public cloud, APIs become available to hackers, which may lead to cyberattacks against them. Shadow APIs are published outside of a defined process, and because of that security team and different security tools won’t be able to track them. These APIs often do not have authentication and can expose sensitive data.
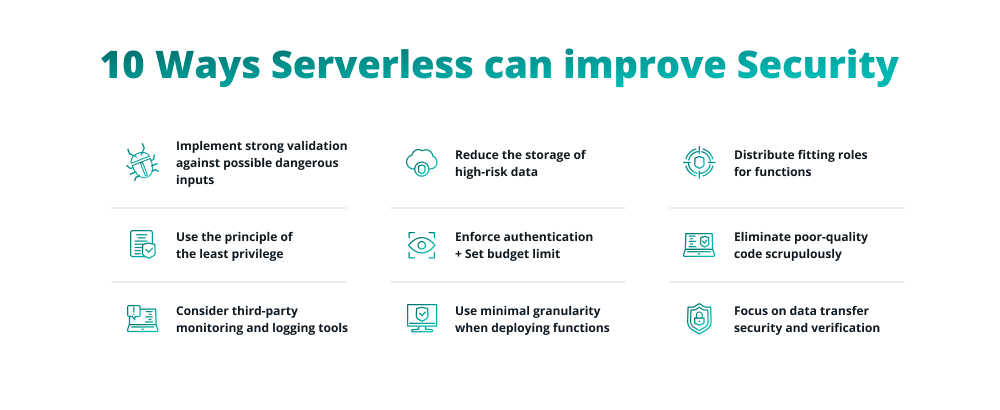
10 Ways Serverless Can Improve Security
Implement strong validation against possible dangerous inputs
Even if you think that you can trust the source, it is essential to be especially careful about checking every piece of data and evaluating them against dangerous inputs. Sometimes, even the best programmers might overlook rare data patterns like local file inclusion attacks, which makes the system vulnerable and leads to security breaches in serverless computing.
Use the principle of the least privilege
The principle of the least privilege will help you avoid imperiling functions in serverless applications. Use the opportunity to grant rights to individual functions and make sure the permissions are restricted to the smallest possible scope. This will mitigate the risk of an attack and make the workflow more manageable and responsibilities more transparent.
Consider third-party monitoring and logging tools
When it comes to AWS and serverless security, it is highly recommended to collect real-time security events. Implement a serverless-native monitoring system, or trust a third-party solution for a better monitoring tool. Take advantage of AWS services like AWS X-Ray, Amazon CloudWatch, and Amazon CloudTrail for quality logging and monitoring systems.
Reduce the storage of high-risk data
Another crucial serverless architecture and security problem is the unwanted display of sensitive data. Conduct a risk assessment of the sensitive data, minimize its storage, and encrypt all the data that will be shared and exchanged frequently or exposed to third-party services.
Enforce authentication
You can save an immense amount of valuable time on creating a complex authentication system on your serverless security platform, by using the convenient access management tools like Microsoft’s Azure AD. In addition to that, you can introduce an extra step in the security check process for altering information that can be potentially hazardous and destroy or modify data.
Set budget limit
Try to avoid the consequences of a Denial of Wallet attack by limiting your budget. Additionally, to increase serverless security, you can implement a restriction on the number of requests a client can make in a given period. Finally, make the internal API gateways private and unavailable for hacker attacks.
Distribute fitting roles for functions
Handling permissions among numerous resources that interact with each other in the system can be cumbersome in serverless architecture management. This is why related policies must be reviewed in order to streamline resource intensity. This is also where you will need to create minimal access roles for each existing function, ensuring that all of those functions can execute the smallest viable list of privileges. It helps conveniently narrow down and expand privileges according to the situation.
Eliminate poor-quality code scrupulously
Extremely extensive scaling opportunities and numerous varying triggers characteristic of serverless deployments may turn even the tiniest, insignificant errors into real performance threats that hinder the system and fail user operations. So code must be regularly inspected and cleaned where necessary, which must be carried out by a well-qualified developer or even a dedicated code reviewer. And it is always a great idea to use various tools for static analysis that help pinpoint problematic code sections early on; SonarQube is a whole open-source platform for finding and improving bad code.
Focus on data transfer security and verification
Regular web communication is crucial to be reliably secured and protected. To achieve reinforced security for the web app, you’d want to verify all your SSL certificates to confirm all communication identities and servers’ authenticity, use signed requests with cloud providers (if they support it), leverage HTTPS internally and externally across all communication mediums, and carefully monitor third-party services classifying them as untrusted user input.
Use minimal granularity when deploying functions
Focusing on the small size of functions and their underlying code, you narrow down the surface for potential attacks and security flaws. It is important to balance the amount and size of both code and related functions, as well as avoid bulk function deployments. Within a serverless project, all functions run on the same dependencies, which opens numerous opportunities for reusing code and employing convenient templates for building sturdier structures with extra functional support.
Serverless Security Trends in 2023
Serverless security concerns motivate people to come up with new technologies, expand the range of modern tools, and seek new cyberattack mitigation methods. Let’s talk about the upcoming serverless and security trends in 2023.
#1 Tools for adopting serverless will become more available
As mentioned before, there are a number of serious security problems that developers are trying to eliminate. That makes big corporations like Google work on secure and transparent technology to ensure safety and usability. Further, applications for the smooth adoption of serverless technologies are being put in place. For example, Dashbird helps you monitor and detect any potential failures and malfunctions in the apps.
#2 Serverless will become standardized
Being a relatively new and unexplored technology, serverless architecture lacks standardization, which Cloud Native Compute Foundation (CNCF) is ready to provide. CNCF offers an opportunity to build sustainable ecosystems and encourages organizations to create scalable applications in the modern environment. There is an urgent need for serverless security best practices, tools, and utilities to build an extensive framework that will drive innovation and put AWS consulting services on the next level.
#3 Hybrid IT landscape
While serverless computing is a drastically increasing model, one shouldn’t overlook the advantage of traditional models. Experts suggest that the future will create more hybrid solutions because apps will run on data centers while others on the public cloud. Due to this integration, the serverless architecture will increase in popularity and provide more useful features.
Conclusion
So, why is serverless security important? Due to its innovative nature and hidden pitfalls, it remains complex and overwhelmingly diverse for many programmers. Implementing the recommendations mentioned above is crucial to stay afloat and avoid economic losses.
If you find serverless architecture too complicated, especially if you are a small business or a startup, it is highly advised to seek professional help from experts. The TechMagic team of professionals has been an official serverless dev partner since 2018 and has years of experience at its disposal.
We’ve excelled in serverless computing and integrated security, Internet of things, and high-availability applications. Check out the AWS and serverless architecture case studies and learn more about the security testing services TechMagic has to offer to make the first step and achieve a totally secure serverless CMS or solution of any other format.



 Software Development
Software Development
 Security Services
Security Services
 Cloud Services
Cloud Services
 Other Services
Other Services
















 TechMagic Academy
TechMagic Academy
 linkedin
linkedin
 facebook
facebook
 twitter
twitter






















