PCI Compliance Checklist: A Step-by-Step Guide to Meeting 12 Requirements
Last updated:23 January 2025
Recently, many customers have experienced frustration of being contacted by their banks or financial institutions with the disheartening news that their credit card information has been compromised. Credit card fraud continues to be a recurring issue, posing significant challenges for businesses
The question is: How can we ensure that the online service providers who accept and store our credit card information take the necessary measures to safeguard it?
To address this pressing issue, Visa, Mastercard, American Express, Discover, and JCB united in 2006 to form the Payment Card Industry Security Standards Council (PCI SSC or PCI Security Standards Council). This council was established to administer and manage security standards for companies dealing with credit card data.
Before the inception of the PCI Data Security Standard, these credit card companies maintained separate security standards programs, sharing similar requirements and objectives. In a remarkable collaboration, they merged their efforts under one standard policy known as the Data Security Standard PCI (PCI DSS).
Understanding and complying with PCI DSS can be a complex and daunting task. For businesses handling card data, adherence to the 300+ security controls in PCI DSS might be mandatory.
The official documentation published by the PCI Council encompasses over 1,800 pages, with over 300 pages solely dedicated to understanding the forms used for validating compliance. Merely reading this documentation would consume more than 72 hours.
However, if not done correctly, achieving compliance can become daunting and costly, consuming substantial time and resources. To ease run businesses through the compliance process, we offer a comprehensive step-by-step guide to validating and maintaining PCI compliance.
What Is PCI Compliance?
Security standard PCI DSS stands as a comprehensive global security benchmark for entities involved in storing, processing, or transmitting cardholder data and sensitive authentication data. Its primary objective is to establish a baseline level of consumer protection, effectively reducing fraud and data breaches across the entire payment ecosystem.
Regardless of the scale, any organization that accepts or processes payment cards falls under the purview of PCI DSS.
Join our upcoming webinar to get practical guidance before your next audit
In essence, PCI compliance entails adhering to technical and operational standards to secure and protect credit card data provided by cardholders during card processing transactions. Preventing fraud and data breaches is a collective effort that requires businesses to stay vigilant, adhere to PCI DSS standards, and adopt consistent data security measures.
The latest iteration of PCI DSS compliance, version 4.0.1, aims to bring more flexibility to the standards, focusing on integrating technology and business processes. While having firewalls and antivirus software is essential, understanding how these security measures align with your overall business operations is equally crucial. Under PCI DSS 4.0.1, various technical areas are being considered for modification to maintain cardholder data security:
- Authentication and password guidance
- Advanced system monitoring
- Multi-Factor Authentication

PCI DSS v4.0.1 vs. PCI DSS v4.0
The PCI Security Standards Council (PCI SSC) released PCI DSS v4.0.1 to address feedback and clarify requirements from v4.0, published in March 2022. This update corrects minor errors and refines guidance without adding or removing any requirements.
To ensure alignment with industry needs, PCI SSC gathered feedback during a December 2023 - January 2024 review period. Participants can access the feedback summary in the PCI SSC portal.
Key changes
- Requirement 3: Updated applicability for issuers and companies using cryptographic hashes.
- Requirement 6: Clarified 30-day patching for critical vulnerabilities and added notes on payment page script management.
- Requirement 8: Specified MFA exceptions for phishing-resistant authentication.
- Requirement 12: Updated guidance on customer and third-party service provider relationships.
Both PCI DSS v4.0 and v4.0.1 will be active until December 31, 2024, after which only v4.0.1 will remain. This update does not change the effective date for new requirements, which remains March 31, 2025, and introduces no new or removed requirements – it simply clarifies existing ones.

How Often Does PCI Compliance Need To Be Updated?
PCI compliance is not a one-time endeavor but an ongoing commitment to maintaining cardholder data security. The frequency of these updates depends on various factors, including the level of compliance required for a particular business and the volume of card transactions processed annually. Let's explore how often PCI compliance needs to be updated for different merchant levels:
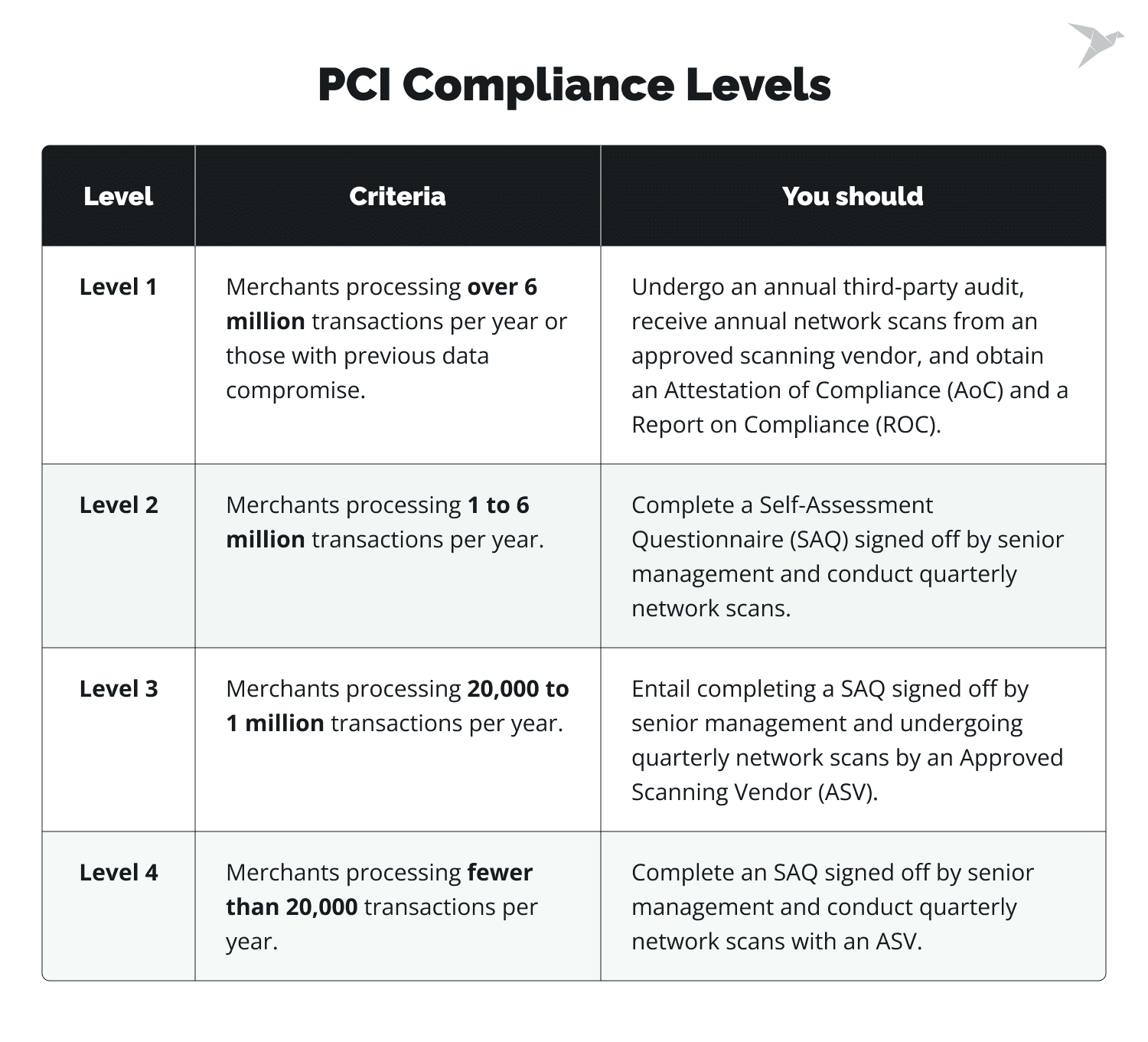
The more transactions a company handles, the more rigorous the compliance requirements (especially regarding security vulnerabilities) become. The four levels ensure that all organizations adhere to specific compliance standards while considering individual risk factors and infrastructure capabilities.
Who Is Obliged to Be PCI Compliant?
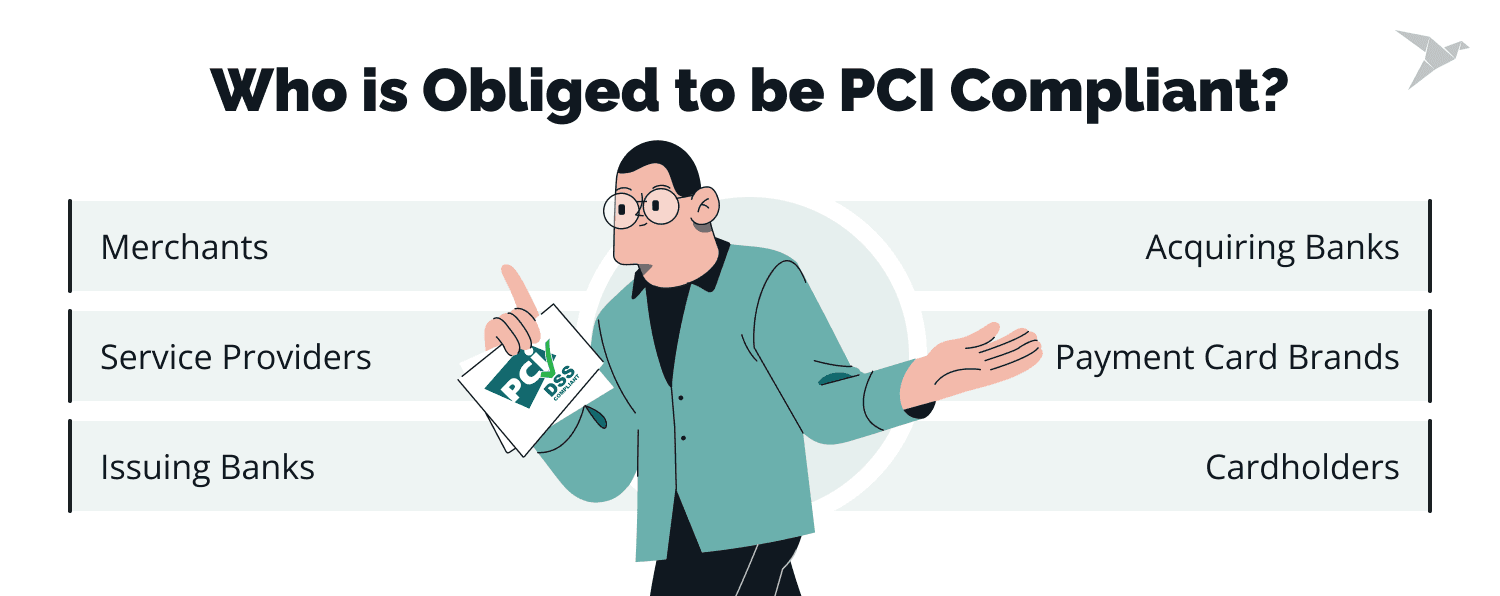
PCI compliance is essential for any organization that handles credit card transactions or processes cardholder data. Several entities are obligated to be PCI compliant:
- Merchants: Merchants are at the forefront of PCI compliance obligations. Any business that accepts credit card payments, regardless of size or industry, must comply with PCI DSS standards. Merchants include retail stores, e-commerce websites, restaurants, hotels, service providers, and other businesses conducting card transactions.
- Service Providers: Service providers are entities that process, store, or transmit cardholder data on behalf of merchants. These may include payment processors, web hosting companies, cloud service providers, and software vendors.
- Issuing Banks: The banks that issue credit cards to customers are also subject to PCI compliance requirements. They are responsible for safeguarding sensitive cardholder information in custom BNPL development and ensuring that merchants who accept their cards meet PCI DSS standards.
- Acquiring Banks: Acquiring banks, also known as acquiring processors or acquirers, are financial institutions that establish and maintain merchant accounts.
- Payment Card Brands: Major payment card brands such as Visa, Mastercard, American Express, Discover, and JCB are crucial in enforcing PCI compliance. They set the standards and guidelines for PCI DSS and require their merchants and service providers to adhere to these rules.
- Cardholders: While not directly obligated to be PCI compliant, cardholders play a role in maintaining security. They are encouraged to protect their credit card information, use secure online payment methods, and promptly report any suspicious activities related to their cards.
Benefits of PCI DSS Compliance
Complying with PCI Security Standards may seem overwhelming, particularly for smaller companies. However, the advantages of compliance are significant, and failure to comply can lead to serious long-term consequences.
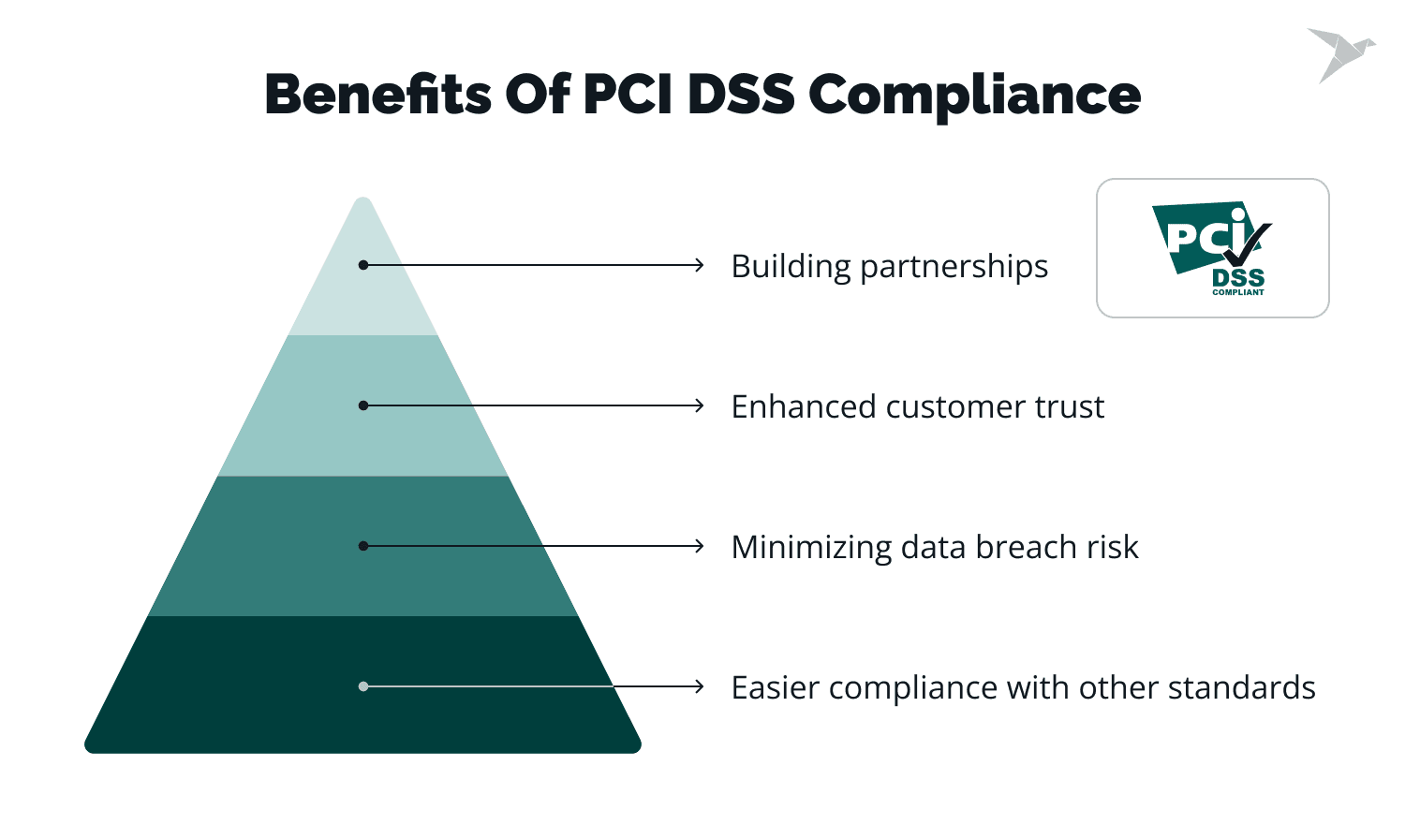
- Building partnerships: Being PCI compliant allows you to collaborate with payment processors, enabling you to establish an online marketplace or launch your payment card. It also improves your reputation with acquirers and payment brands, fostering trust and credibility with essential business partners.
- Easier compliance with other standards: PCI DSS shares similarities with other compliance frameworks like GDPR or HIPAA. By achieving PCI compliance, your business is better prepared to meet the requirements of these other standards, streamlining the overall compliance process.

- Minimizing data breach risk: Complying with PCI security standards ensures that your systems are secure and capable of safeguarding sensitive payment card information. This, in turn, builds trust with customers, leading to increased confidence and loyalty.
- Enhanced customer trust: By adhering to PCI Compliance standards, businesses are committed to securing their systems and protecting customer data.
What Happens If You Are Not Compliant?
Accepting credit cards is a necessity for businesses. However, the rising threat of credit card fraud, identity theft, and data breaches underscores the criticality of maintaining a secure environment for charge card transactions. When a company is found to be non-compliant with PCI-DSS, the penalties and consequences can be severe, ranging from fines to the loss of the ability to accept credit card payments. Some of the penalties include:
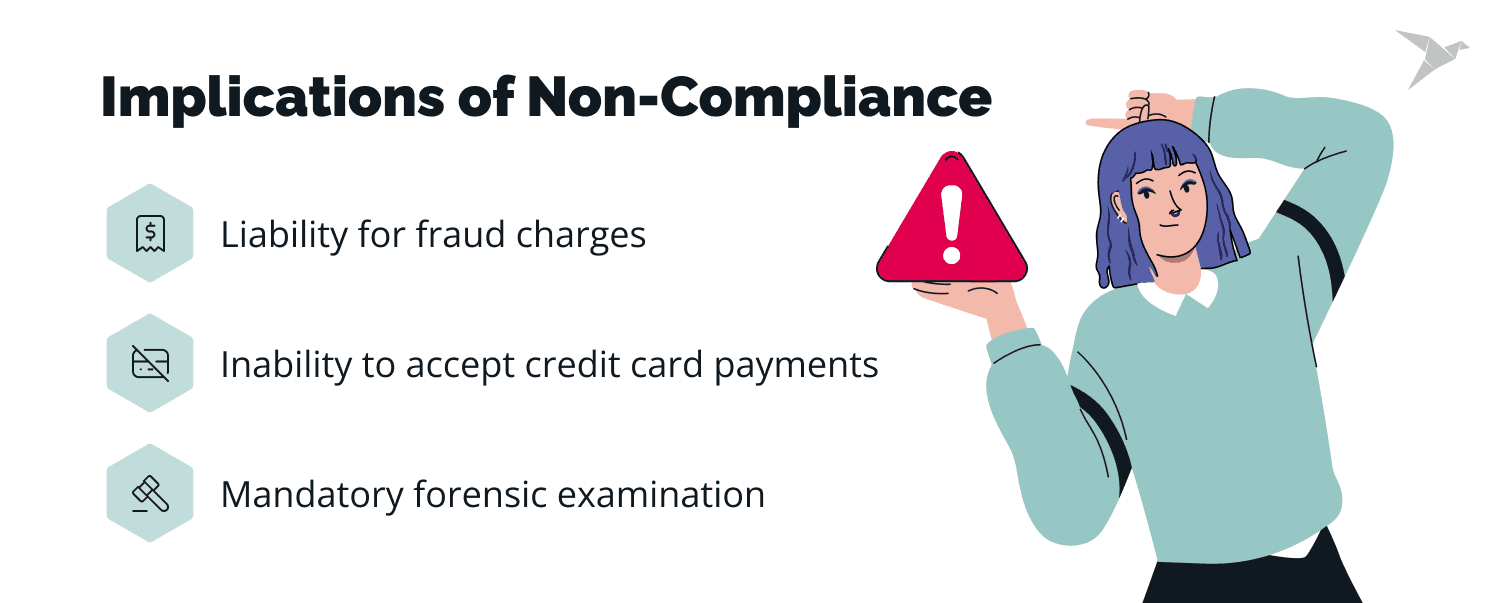
- Inability to accept credit card payments: Losing the ability to accept credit card payments can lead to significant financial losses, a decline in market share, and damage to the company's reputation. To regain permission to process payments, a non-compliant organization must undergo a PCI reassessment by an external Quality Security Assessor (QSA).
- Mandatory forensic examination: When a data breach is suspected, merchants may undergo a costly forensic examination. The cost can vary, with Level 2 merchants (1-6 million annual transactions) facing expenses between $20,000 and $50,000, while Level 1 merchants (6+ million annual transactions) may incur costs upward of $120,000.
- Liability for fraud charges: After a security breach, a company becomes liable for any fraudulent charges, leading to potential lawsuits and financial liabilities.
Examples of data breaches
The staggering number of 36 billion records exposed in data breaches during the first six months of 2020 underscores the severity of the threat.
More recently, in 2021, Next Level Apparel (NLA) fell victim to a phishing scam. The attackers illegally accessed NLA's database, compromising valuable data, including Social Security and credit card numbers. As a response, NLA implemented additional security measures and enhanced email security protocols to safeguard customer information.
Neiman Marcus also experienced a significant data breach in the same year. The breach impacted 4.6 million customer accounts, exposing customer names, contact information, credit card numbers, usernames, passwords, and even virtual gift cards. In response, Neiman Marcus enforced a mandatory password reset to bolster security.
During the 2021 Black Friday Cyber Monday shopping weekend, cybercriminals exploited a known vulnerability in the popular e-commerce platform Magento. Targeting approximately 4,151 self-hosted Magento stores, the hackers gained unauthorized access to personal and payment information.
Fortunately, the UK's National Cyber Security Centre's Active Cyber Defense program identified the security breach and urged merchants to apply stringent security patches to protect their customers.
The question should not be whether PCI DSS compliance is mandatory (it is) but rather why any business would risk the consequences of not implementing it.
How Much Are PCI Non-Compliance Fines?
Non-compliance fines for PCI-DSS can have significant financial ramifications, with penalties ranging from $5,000 to as high as $500,000 per PCI data security incident, especially in the case of massive data breaches.
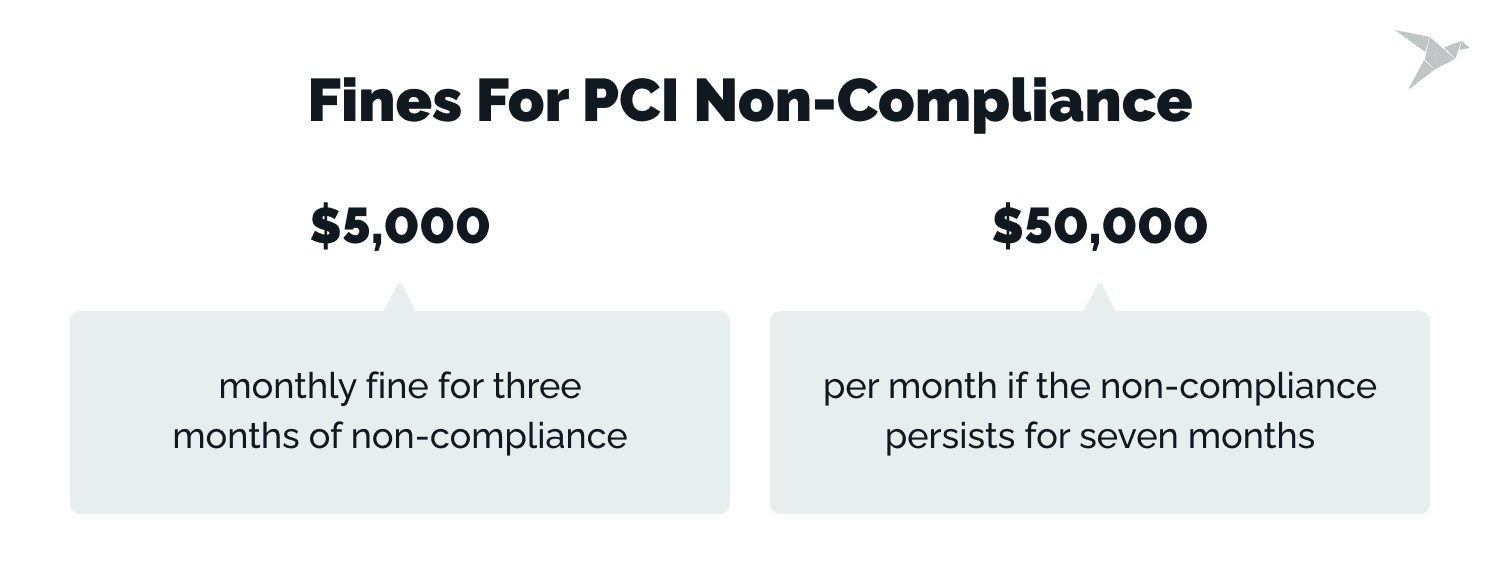
When merchants enter into contracts with payment processors, they agree to be subject to fines for non-compliance with PCI DSS. The fines can vary based on the payment processor and are typically higher for companies with a higher volume of transactions. While pinpointing a typical fine amount is challenging, IS Partners provides some ranges.
Fines are assessed every month for the duration of non-compliance, and the monthly charge increases for more extended periods. For example, a company might face a $5,000 monthly fine for three months of non-compliance, but the fine could escalate to $50,000 per month if the non-compliance persists for seven months. Moreover, individual fines ranging from $50 to $90 can be imposed for each customer affected by a data breach.
These "fines" are not akin to government or traffic violations; rather, they are penalties outlined in contractual agreements between merchants, payment processors, and card brands.
Furthermore, regulations dictate that all individuals whose data has potentially been exposed to a breach must be notified in writing. This ensures they are alert for fraudulent activity on their accounts. There is no possibility of concealing this breach of trust from those affected.
How to Become PCI Compliant
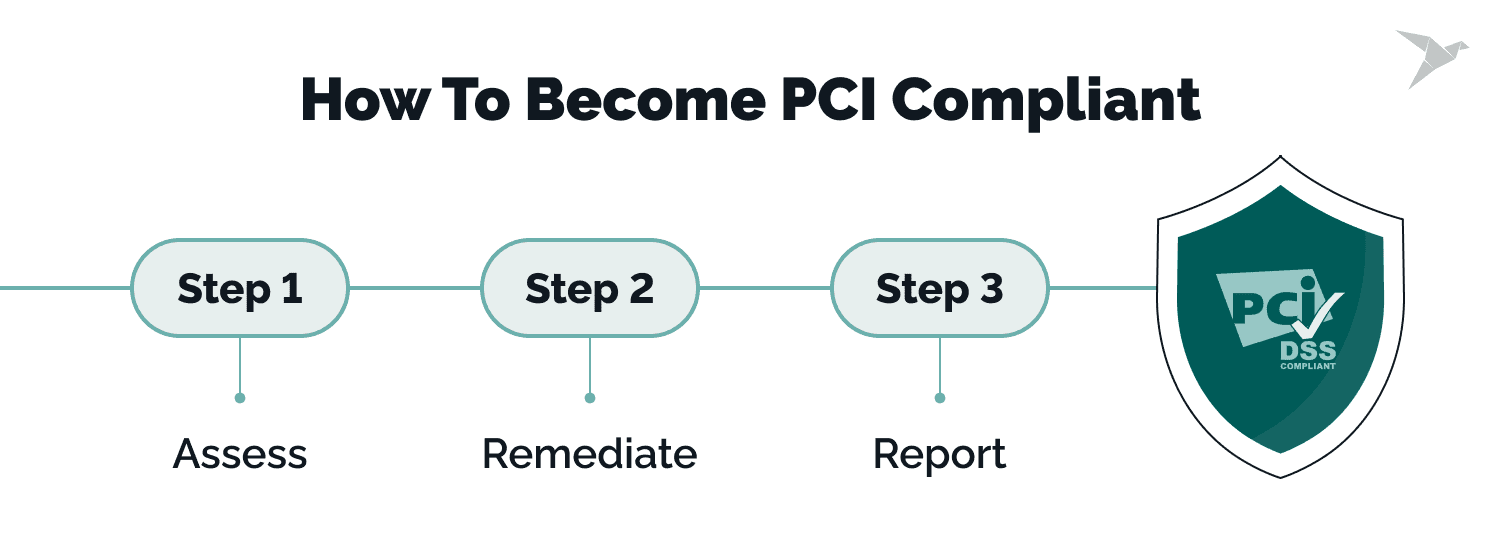
The PCI Standards Council provides a transparent three-step process to ensure PCI compliance:
Step 1: Assess
The initial stage of achieving PCI compliance involves conducting a thorough assessment to identify and understand cardholder data, IT assets, and business processes associated with payment card processing. By doing so, businesses can pinpoint potential vulnerabilities and develop targeted strategies for protection.
To commence the assessment, it is essential to document all systems and processes involved in storing, processing, or transmitting cardholder data. This encompasses not just payment systems but any interconnected systems, as a vulnerability can endanger cardholder data security.
Additionally, performing vulnerability scans and penetration testing both internally and externally becomes indispensable to unveil any security weaknesses within the PCI DSS scope.
Penetration testing for Coach Solutions web application

Step 2: Remediate
During the remediation phase, businesses address the vulnerabilities uncovered in the assessment stage. High-risk vulnerabilities demand immediate attention as they pose the greatest threat to cardholder data security. Once these critical issues are resolved, attention can be turned to lower-risk vulnerabilities.
Remediation efforts may involve various activities, such as patching software, updating firewalls, changing passwords, and even reevaluating business processes. Recognizing that remediation is an ongoing endeavor is crucial since new vulnerabilities can emerge anytime.
Step 3: Report
The final phase revolves around reporting PCI compliance. This entails compiling and submitting a comprehensive report to the acquiring bank and major payment card brands for validation. The type of report required varies based on the size of the business and the number of transactions processed annually.
For smaller businesses, a Self-Assessment Questionnaire (SAQ) typically suffices, while larger enterprises may undergo an onsite audit conducted by a Qualified Security Assessor (QSA) or Internal Security Assessor (ISA). Beyond mere proof of compliance, the reporting process allows businesses to reflect on their security practices and explore avenues for improvement.
PCI Compliance Checklist: 12 Requirements
Let's delve into the step-by-step process to meet all the 12 requirements.
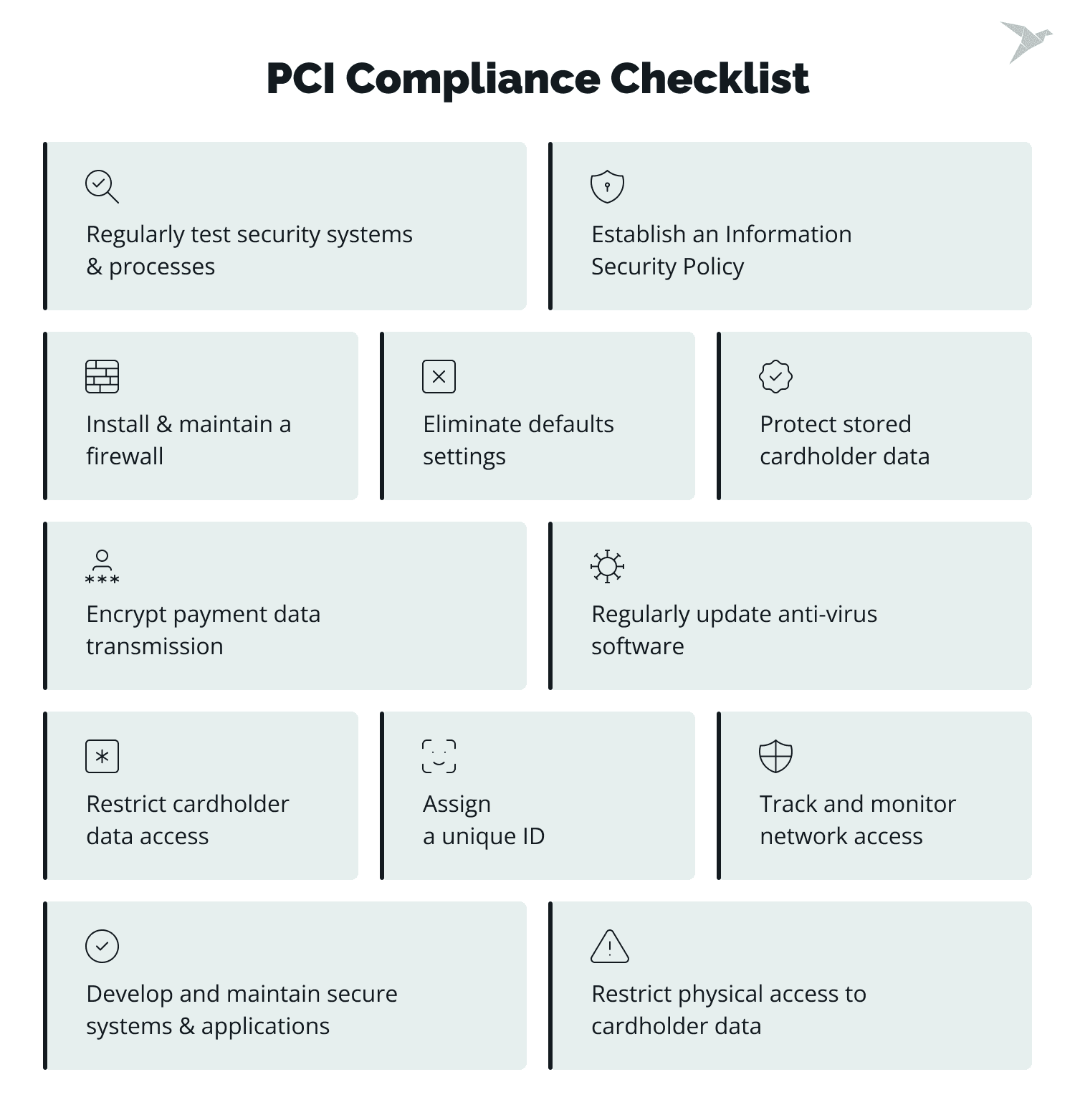
Step 1: Install and maintain a firewall
A firewall serves as the first line of defense for any network, safeguarding cardholder data and preventing unauthorized access. To meet PCI DSS Requirement 1, proper firewall maintenance is essential.
This involves
- configuring rules and criteria to control incoming and outgoing network access,
- documenting processes,
- regularly reviewing configuration rules and flowcharts.
Properly configuring firewalls and routers and establishing strict rules for allowed traffic are essential.
Step 2: Eliminate default settings
Hackers can easily exploit vendor-supplied defaults for devices like firewalls and routers. PCI DSS Requirement 2 hardens the network by changing default passwords, usernames, and administration accounts. This reduces the risk of unauthorized access and strengthens overall network security.
Step 3: Protect stored cardholder data
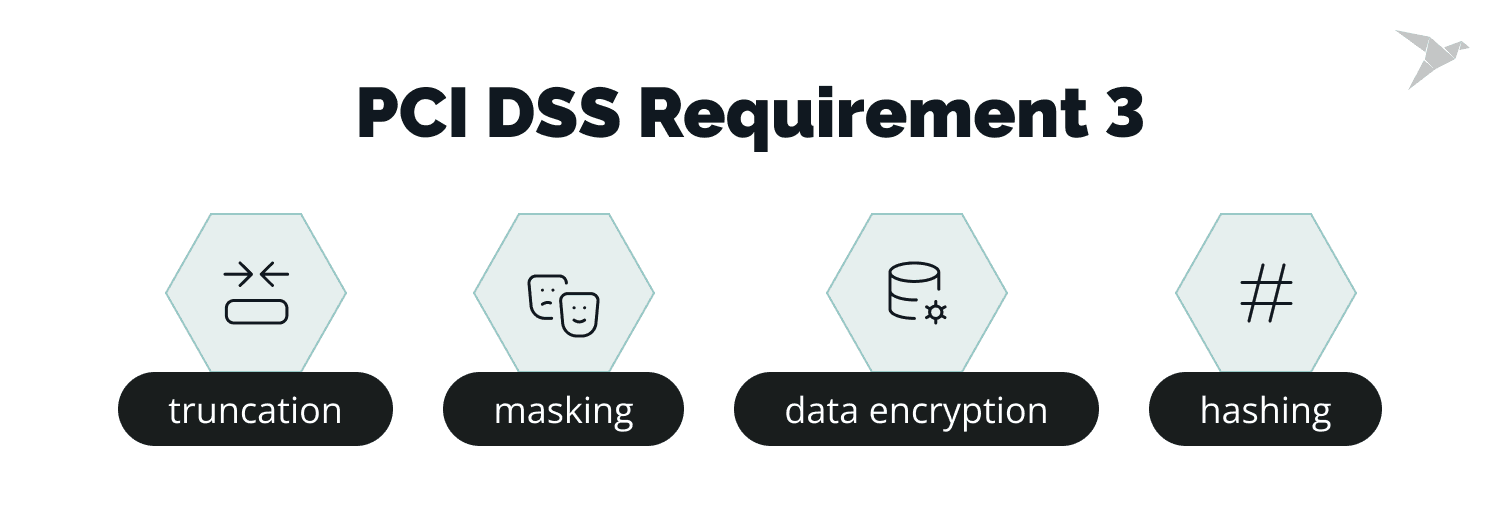
PCI DSS Requirement 3 aims to minimize risks associated with storing sensitive data. Implementing security mechanisms such as encryption, truncation, masking, and hashing ensures that the data remains unreadable and unusable even if hackers gain access. Practices like strong encryption, minimizing unnecessary data storage, and following data retention and destruction policies help protect cardholder data. Utilizing a card data discovery tool helps identify unencrypted primary account numbers (PAN).
Learn how we built macro-investing app with its own token and reward system
Step 4: Encrypt payment data transmission
Data transmitted over open and unencrypted public networks is vulnerable to exploitation by malicious individuals. PCI DSS Requirement 4 stresses the importance of encrypting transmission and preventing unauthorized access to sensitive data.
Disabling weak keys and using strong protocols like TLS 1.1 or higher enhances security. PCI DSS v4.0 and PCI DSS v4.0.1 will provide specific guidance on multi-factor authentication (MFA).
Step 5: Regularly update anti-virus software
Malware poses a significant threat to cardholder data security. PCI DSS Requirement 5 mandates using up-to-date anti-virus solutions capable of detecting and removing various types of malware, including viruses, worms, Trojans, bots, and ransomware. Keeping antivirus software updated, maintaining audit logs, and monitoring malware trends are essential in countering evolving threats.
Step 6: Develop and maintain secure systems and applications
Conducting a comprehensive risk assessment is critical to identify and classify risks related to technology deployment. With the risk assessment completed, secure equipment and software used for processing payment card data can be rolled out.
Timely application of patches for databases, point-of-sale terminals, and operating systems is also essential. Using reputable sources for vulnerability identification, such as Microsoft Security Bulletins and Cisco Security Advisories, is crucial.
Step 7: Restrict cardholder data access
Maintaining PCI compliance requires controlling access to payment card data based on roles and permissions. Organizations must limit access to private cardholder data to only those who truly need it for essential business purposes. Meeting physical security requirements is also vital, involving documented access control policies based on job function, seniority level, and reason for data access.
Step 8: Assign a unique ID
To bolster security, everyone with computer access to cardholder data should have a unique identification and password. PCI DSS Requirement 8 also mandates proper management of authentication credentials, including adding new users and promptly deleting access for terminated employees.
Robust user IDs and passwords must meet specific criteria, such as length and complexity, to minimize the risk of unauthorized access. Implementing multi-factor authentication (MFA) adds an extra layer of protection.
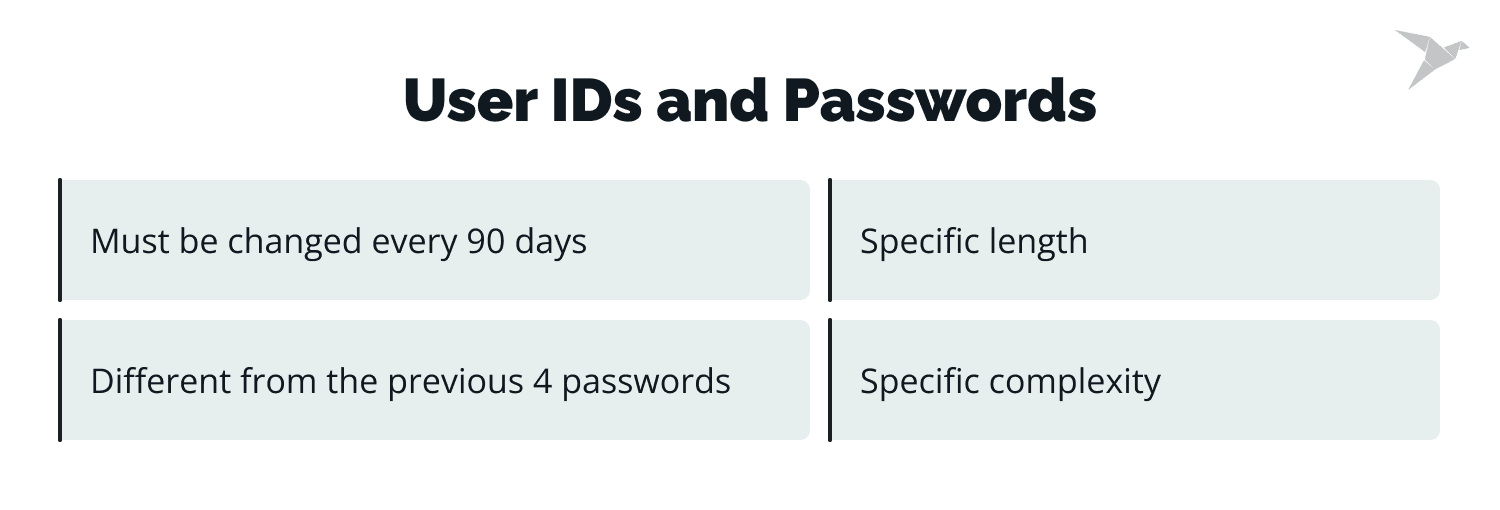
PCI password requirements:
- Passwords must be at least seven characters long.
- They must include a combination of numbers and letters.
- Users must change passwords every 90 days.
- The new password must differ from the previous four passwords.
- For new users or password resets, unique passwords must be generated and changed after first use.
- The lockout duration for a user's account after failed attempts is 30 minutes or until a system administrator resets it.
- Vendor-supplied defaults are prohibited.
- Passwords must be encrypted during transmission and storage.
Step 9: Restrict physical access to cardholder data
Physical security is as crucial as digital security. PCI DSS Requirement 9 addresses protecting cardholder data in physical locations like servers, data centers, and computer rooms.
- Access to these areas must be tightly controlled through badge readers and key-controlled locks.
- Monitoring with security mechanisms, including video cameras, further enhances protection.
- Implementing automatic server locking and timeout systems ensures secure login screens when not in use.
- Access logs and recordings should be retained for at least 90 days, and portable media with cardholder data must be securely stored and disposed of when no longer needed.
Step 10: Track and monitor network access
Organizations must keep detailed logs of network and cardholder data access for effective troubleshooting and forensic investigation in case of a breach. PCI DSS Requirement 10 focuses on maintaining logs to track activities related to cardholder data, including individual access, invalid access attempts, access to audit logs, and other transactions.
Security Information and Event Monitoring (SIEM) tools help track system activity and identify suspicious behavior. Network activity logs must be maintained for at least one year and time-synchronized for proper analysis.
Learn how we built macro-investing app with its own token and reward system

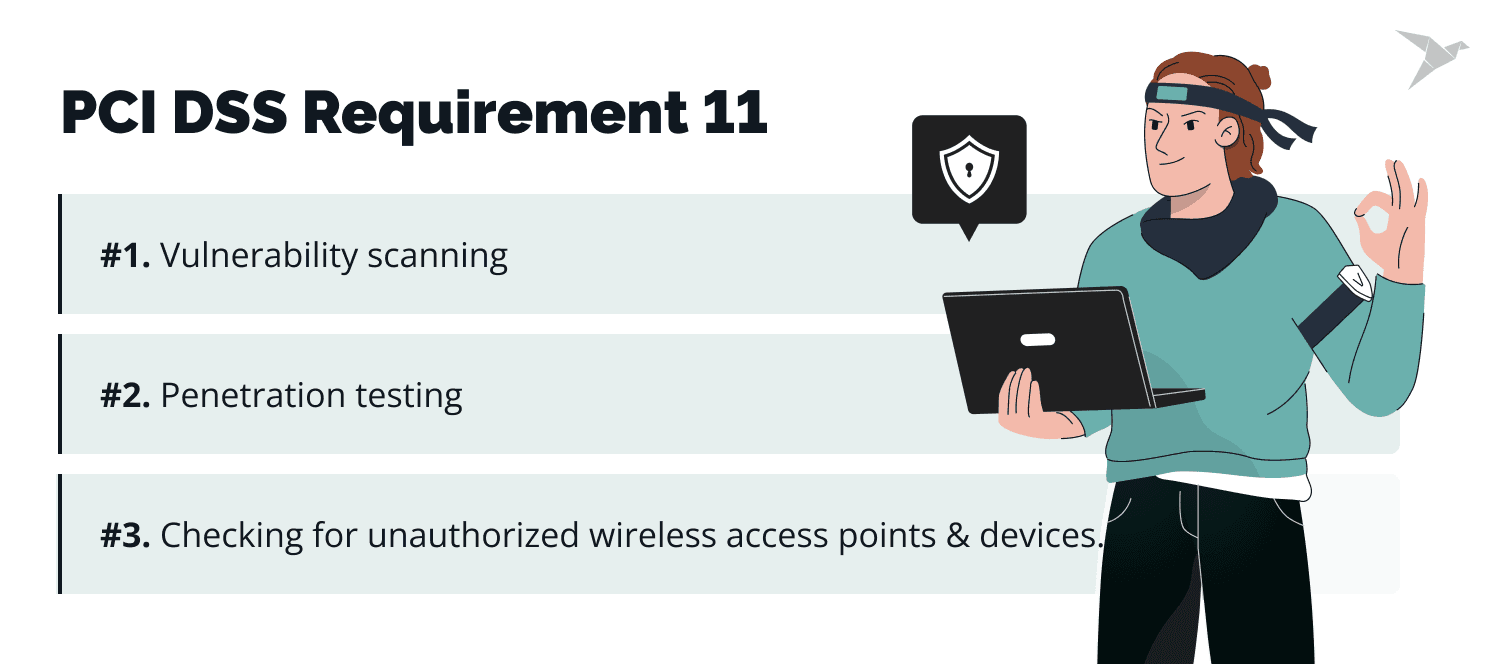
Step 11: Regularly test security systems and processes
Securing the system is just the beginning; it is crucial to identify vulnerabilities and address potential security weaknesses proactively. PCI DSS Requirement 11 encompasses vulnerability scanning, penetration testing, and checking for unauthorized wireless access points and devices.
Quarterly vulnerability scans help identify and resolve vulnerabilities, while annual penetration tests simulate real-world attacks to expose weaknesses in the system after significant changes.
Step 12: Establish an information security policy
The final step towards PCI compliance involves creating and maintaining a comprehensive information security policy across the organization. This policy should
- cover all employees, management, and relevant third parties.
- include security awareness training programs, regular policy reviews, risk assessment processes, incident response programs, and technology usage policies to foster a culture of data security throughout the organization.
Achieving PCI Compliance: Tips and Best Practices
The PCI standard mandates the implementation of both digital and physical barriers to safeguard cardholder data. This may encompass authentication protocols, robust password policies, locked servers, and secured cabinets for physical data. Additionally, critical security measures are restricting access to cardholder data and encrypting its transmission.
Create a well-defined incident response process that outlines the steps for detecting, mitigating, and recovering from security incidents. Having a well-prepared and efficient response plan is essential in addressing potential breaches promptly and effectively.
Implement best practices for securing data, similar to how you protect your devices. This includes using strong passwords, keeping software updated (especially for point-of-sale terminals), and avoiding unnecessary storage of physical copies of receipts. Additionally, educate your employees on the importance of safeguarding cardholder data and being cautious with suspicious links.
Conclusion
Ensuring compliance with PCI standards is not only a legal obligation but a crucial aspect of protecting your organization from severe penalties and potential business loss.
Achieving PCI DSS compliance is undoubtedly challenging and requires continuous effort and assessment. While the validation process usually occurs annually, businesses must understand that compliance is an ongoing journey.
As companies evolve and expand their operations, compliance requirements evolve as well. For example, expanding into new markets, opening physical stores, or launching customer support centers may introduce new aspects related to payment card data, necessitating proactive re-validation of PCI compliance.
Identifying the gaps in your current compliance status is just the beginning. To bridge these gaps effectively, consider partnering with experienced PCI compliance specialists. These professionals can provide valuable insights and guidance on FinTech software development services to ensure that your organization meets the requirements of PCI DSS v4.0 and PCI DSS v4.0.1.

FAQ

How can I get a PCI compliance certificate?
To get started, you need to assess your organization's security measures and ensure they align with the PCI DSS requirements. This involves identifying cardholder data, evaluating vulnerabilities, and implementing security controls. Next, you must validate your compliance status. Depending on the volume of credit card transactions your business processes, you may be required to complete a Self-Assessment Questionnaire (SAQ) or undergo an onsite audit by a Qualified Security Assessor (QSA). Once you have completed the assessment and validation process, you can obtain your PCI compliance certificate.
How much does PCI compliance cost?
The cost of achieving and maintaining PCI compliance can vary based on several factors, including the size and complexity of your business, the number of credit card transactions you process, and the scope of your cardholder data environment.
Is PCI compliance required by law?
PCI compliance is not mandated by law or enforced by the government. Instead, it is driven by contractual agreements between businesses and their merchant service providers or payment service providers, as well as the card networks (such as Visa, Mastercard, etc.).

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy