Passkey vs. Password: Understanding the Future of Digital Security
Last updated:14 January 2025
About ten years ago, passwords were almost the only way to log in. Users just had to create and remember a word, and the magic happened. However, with the development of cyber threats, traditional means of authentication have clearly lost their power.
In our new article, we will talk about passkey technology as one of the methods of passwordless access. We will consider its main advantages, pitfalls, and nuances. We'll also look at what authentication tools will be relevant in the future and how they can be used today.
What is a Password?
A password is a string of characters used in conjunction with a username to log into online accounts, composing your login credentials. You probably know that strong passwords are long and complex, combining upper- and lowercase letters, numbers, and symbols. Obviously, the more complex a password is, the better it protects your online account with.
This is the simplest and most widespread method of authentication, posing a serious threat to cyber security though. Many users do not follow best practices either in the workplace or in accessing bank accounts.
Why does this happen? Creating a complex password and remembering it is trivially inconvenient. And from our experience, the modern user is ready to ignore security if it requires inconvenience. It turns out that a high-quality user experience is also part of security.
Admit it: you also often choose weak passwords or reuse the same one for multiple accounts. This is dangerous because weak passwords are easier for cybercriminals to crack, and the same password you reuse means multiple accounts can be compromised if a single password is revealed in a data breach. Don't even get me started on phishing and fake websites.
Some stats
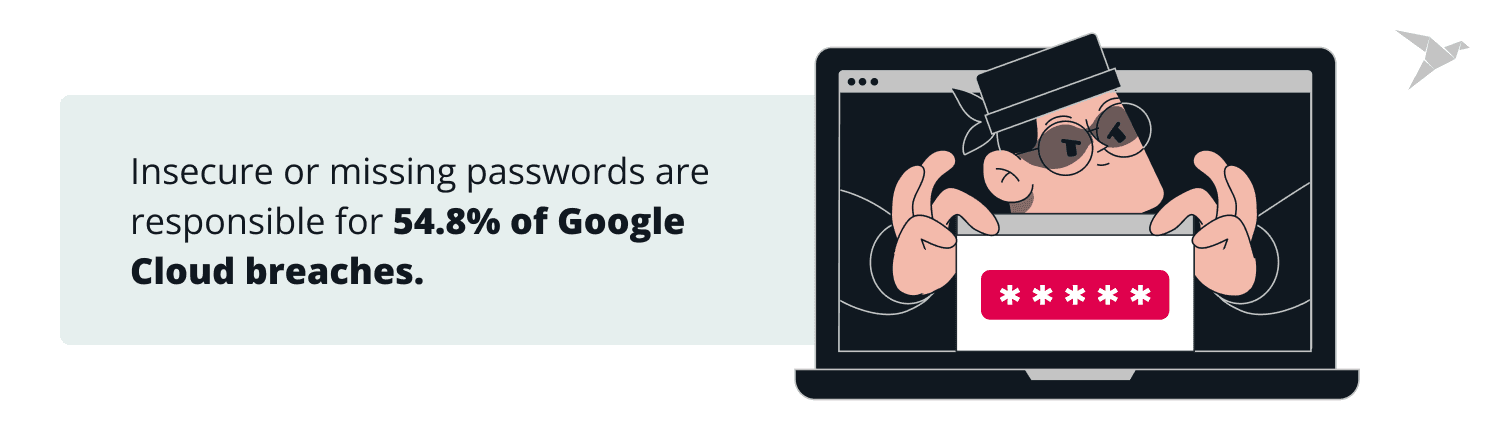
- Insecure or missing passwords are responsible for 54.8% of Google Cloud breaches.
- Bitwarden World Password Day Survey revealed that 69% of respondents report that their most frequently used password is at least a year old.
- 68% of respondents in this survey manage passwords for more than 10 sites or apps, and 84% of them reuse passwords.
- A study by Keeper Security found that 40% of users don't even know if their passwords have ever been compromised due to a data breach.
- Over 80% of companies worldwide have experienced a cyber breach due to an authentication vulnerability.
What Alternative Do We Have? Passkey
As passwords become a less secure method of authentication, passkeys are actively replacing them. This is especially relevant for financial and banking services, where the threat of access to sensitive data is critical.
Statista's 2023 study shows that 41% of respondents in the retail industry and 39% in the financial services industry are most likely to implement passwordless authentication in the next one to three years. Overall, more than one-third of respondents in industries worldwide plan to implement passwordless authentication in the near future.
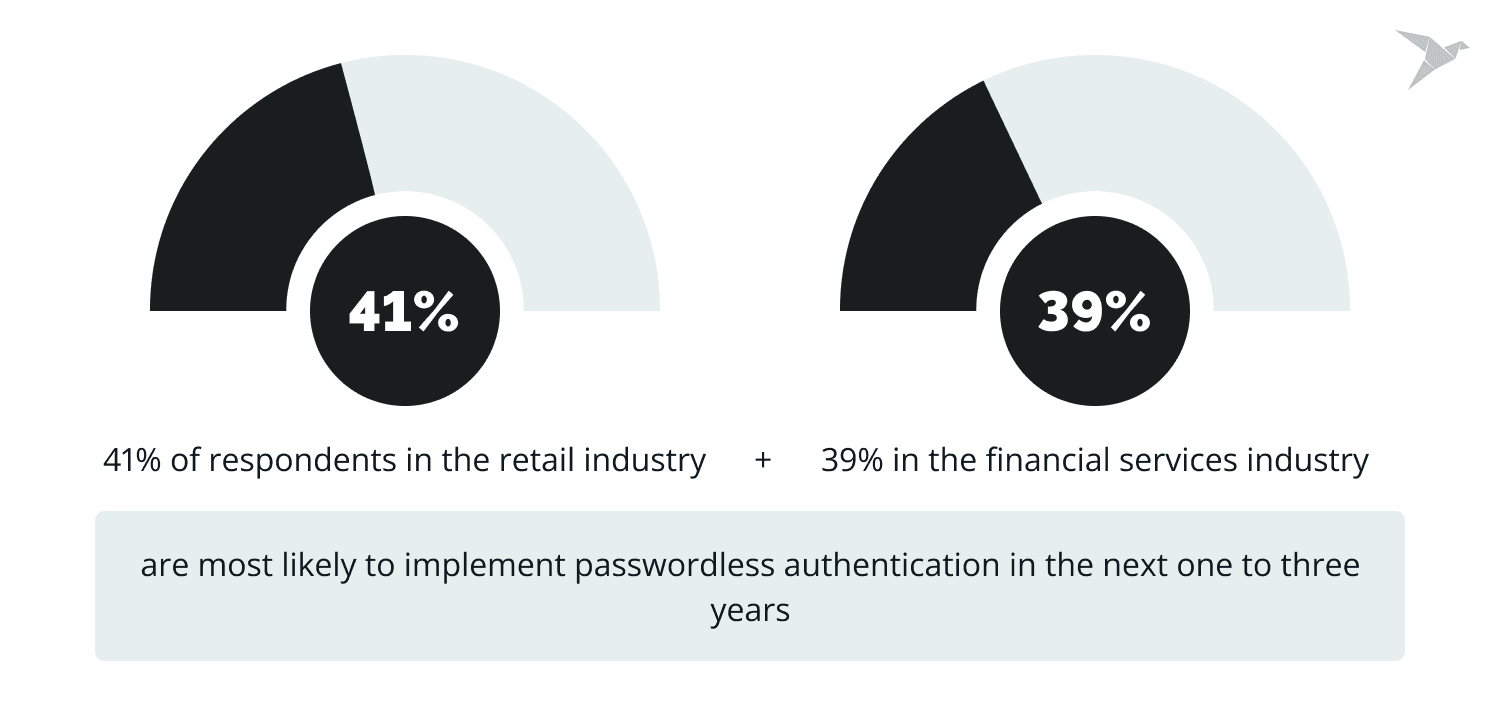
In the same year, 2023, almost 60% of respondents among IT and cybersecurity executives in the United States emphasized that they plan to replace passwords in the workplace with a passwordless means of authentication using biometric data such as facial recognition, fingerprint scanning, iris scanning, or voice verification.
In addition, about 46% of respondents said that their company has replaced or plans to replace work passwords with multi-factor authentication. More than a third of respondents singled out passkeys as an alternative.
Everything is simple here: passkeys are a safer and simpler alternative to passwords.
What are these passkeys? These are digital credentials linked with a user account and a website or application. If you use them, you can authenticate without having to enter a username or password or provide any additional authentication factor to the malicious site. This technology was created specifically to replace outdated authentication mechanisms, including passwords.
We are happy to assist you

How does it work?
Passkeys use public key encryption for security. In simple terms, one of your keys can be stored on your device, and the other key can be stored on the service where encrypted data for your account is stored. You can also sync them to the cloud and copy them from one device to another.
Since this method should be more secure than a password, you must go through some form of authentication to use the passkey option. From our experience, the most effective method is biometric authentication, such as a face scan, scanning, retina, or fingerprint. Such biometric data is saved locally on your own device and is not shared with the platforms you use.
Passkeys prevent you from accidentally sharing your credentials with malicious sites or losing them to phishing. If you lose the device where you store them, you can also revoke the passkey for your Google Account in your password settings or from your Mac and iCloud.
What else?
The concept of passkeys is inextricably linked to the FIDO (Fast IDentity Online) Alliance, which aims to reduce reliance on passwords by promoting advanced authentication standards. The alliance supports various technologies, including biometrics and USB security tokens, using public-key cryptography for authentication.
To confirm its reliability, you can simply look at the alliance's members, which include technological giants such as Apple, Samsung, Microsoft, and Intel. All the top financial app development companies try to follow its guidelines.
Passkeys comply with FIDO standards, and support from Google, Apple, and Microsoft makes them cross-device compatible. Also, since passkeys are created based on FIDO standards, all browsers can use them.
Key Differences Between Passkeys and Passwords
Let's be honest: from our experience, both developers and users alike hate passwords. They significantly worsen the interaction with the user. They are difficult, long, and confusing. At the same time, this is a security threat again for both users and developers.
Nevertheless, let's put emotions aside and take a closer look at the difference.
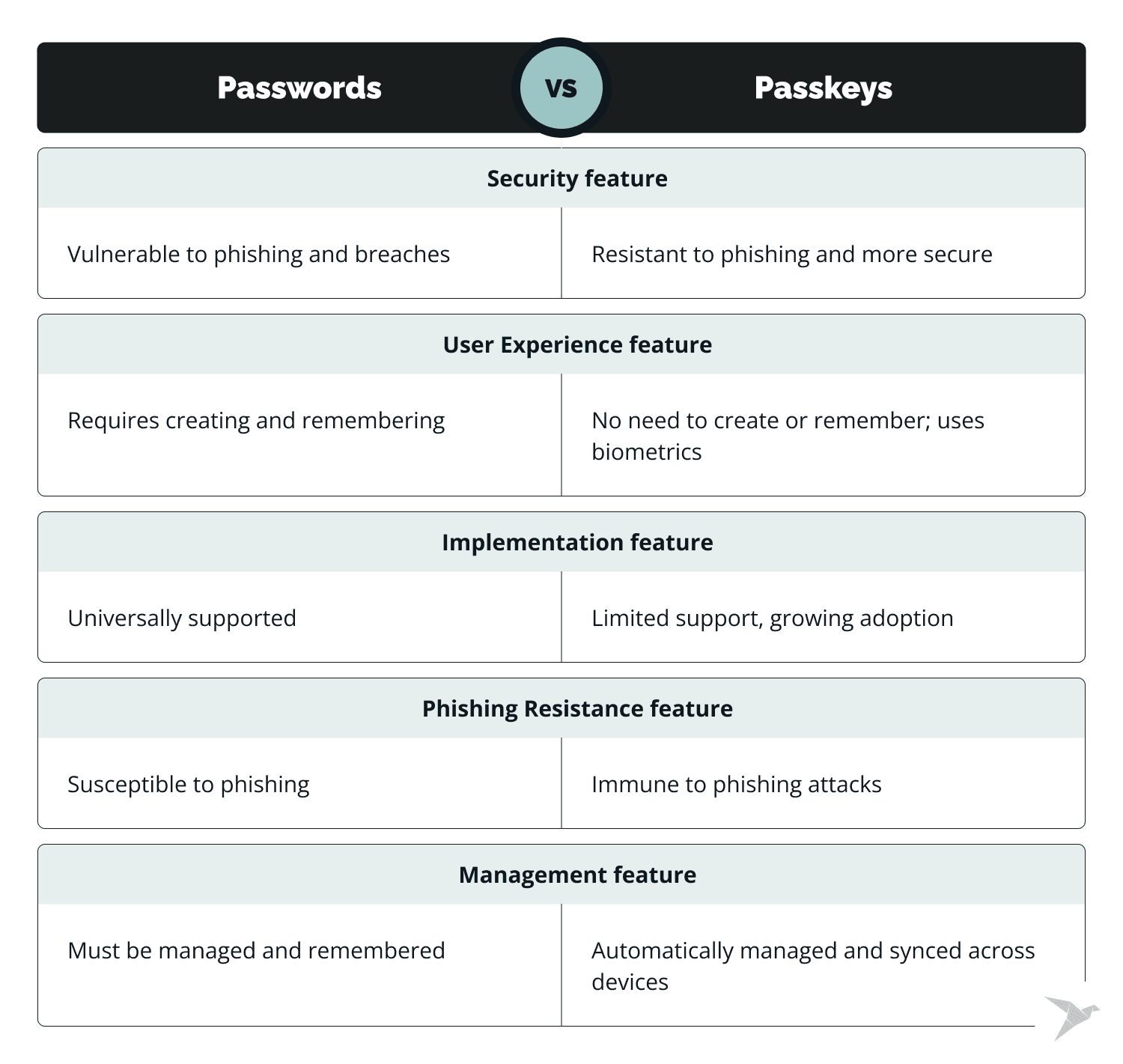
Security
Passwords are 100% dependent on you creating strong, unique combinations of characters. And even if all the rules are followed, they can often be guessed or hacked by cybercriminals.
It's been said above, but we have to stress it: passwords are susceptible to phishing attacks. Users with different levels of digital awareness and comfort are being tricked by attackers into entering credentials on fake websites.
Passkeys use public key cryptography, and this is what makes them resistant to phishing and generally more secure. Since they do not require you to enter anything manually, the risk of credential theft is much lower.
In addition, this type of authentication prevents attackers from accessing accounts. Even if the service database is compromised, only the public key is stored on the server side.
User Experience
Again, using passwords requires you to create, remember, and manage multiple unique credentials. It's not just inconvenient, it's error-prone.
Passkeys simplify this process by generating a pair of keys on the user's device. You don't need to memorize or enter anything manually.
More importantly, passkey authentication is seamless. It often includes biometric verification or device-specific PINs, which greatly improve the user experience. It is familiar to all of us, much simpler and faster. Syncing between multiple devices, in turn, gives you uninterrupted access without having to remember complex passwords.
Implementation
Here, the argument is more in favor of passwords because they are universally supported on all websites and programs, widespread, and easier to implement.
Although passkeys are more secure, they are still in the process of being integrated into systems and are currently supported by a limited number of platforms.
On the other hand, security experts and large technology companies such as Google, Apple, and Microsoft are actively promoting their adoption. It is expected that this method of authentication will become more widespread as the technology develops.
Also, what is an advantage in terms of security is a disadvantage in terms of implementation. Using passkeys requires websites and applications to adopt new authentication standards. For many, this is a difficult and expensive path, but it promises long-term security benefits.

Pros and Cons of Password vs. Passkey
Let’s take a deeper look at password vs. passkey pros and cons.
Why passkeys are superior
Passkeys are a significant leap forward in security and convenience. As we’ve already mentioned, this technology uses advanced public key cryptography. What does it mean?
It means that each passkey consists of a public and a private key pair. The public key is stored by the app or website, while the private key remains securely on your device.
This setup makes it nearly impossible for hackers to guess or steal your login information. And, of course, eliminates the risk of phishing since the private key never leaves your device, providing a seamless and secure sign-in process.
Here are some other passkey’s advantages.
- It is easy to use with biometrics or device passwords and offers a quick and seamless sign-in process.
- You can integrate it with MFA (multi-factor authentication).
- It needs minimal management once set up, as you don’t have to remember or update passkeys frequently.
- This technology helps achieve regulatory compliance. Many regulations, such as GDPR and CCPA, emphasize strong authentication methods to protect user data, and passkeys can be an effective solution.
The strengths of passwords
Despite their limitations, passwords still hold some advantages. Let’s take a closer look at them.
- Passwords are widely supported across all websites and applications.
- They are familiar to most users, which makes them a universal method for securing accounts.
- Their recovery processes are well-established.
Learn how we built macro-investing app with its own token and reward system
What is a passkey vs. password: drawbacks
Talking about what is a passkey vs. password, we can’t forget that each of these authentication methods has its own drawbacks. Let’s start with passkeys.
- Despite being very promising, this method is not yet widely supported and has limited adoption.
- The previous challenge led to the next one: because of limited adoption, users may need time to understand and set up passkeys, which could be difficult for people with less level of digital comfort.
- If the device with the private key is lost or damaged, recovery may need some effort.
- Some older devices or systems may not support passkey technology, limiting its usage.
What about passwords? Here is everything more complex. The main and most dangerous disadvantage of this technology are numerous security vulnerabilities and risks. Password is prone to being weak, easily guessed, or reused across multiple sites. It is also susceptible to phishing attacks and interception during transmission.
Also, password requires regular creation, remembering, and updating, which is not good for safety and user experience. Password managers and MFA may help this, but they add another layer of complexity.
Transitioning to Passkeys: Steps and Considerations
Considerations behind passkeys
Let’s start with some things you should consider before moving to passkeys’ implementation.
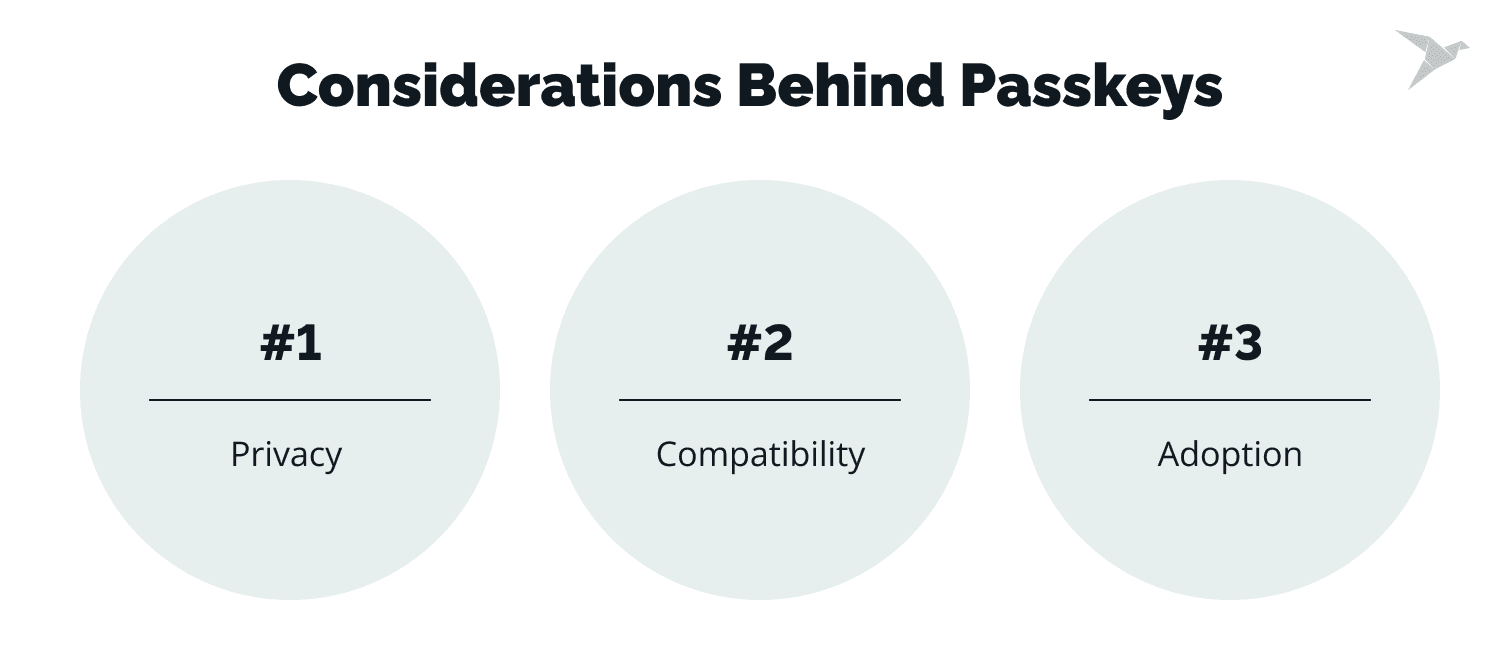
Privacy considerations
Passkey technology is designed with user privacy in mind. The logic behind using biometric data to log in is not always clear to those who are not involved in software development. Very often, this gives users the impression that when using passkeys, their confidential data is sent to the server.
This impression is wrong. In fact, the biometric material never leaves your personal device. By themselves, passkeys do not allow you to track your activities or devices between websites or apps. Also, the same passkey is never used for a login credential on multiple sites.
Sometimes, developers of digital banking products or financial applications need to remind their users about this. Because of this false impression, you have to put some effort into communicating with users and onboarding them.

Compatibility considerations
When switching to passkeys, it is important to consider compatibility aspects. From our experience, it is worth paying attention to the following points.
- Current support. Passwords are universally supported across all websites and apps, but passkeys are much newer technology. Although major technology companies are promoting their implementation, not all platforms currently support them. Before making the full transition, check if your main apps and websites support this technology.
- Operating systems. The passkey function is built into the latest versions of the main operating systems – Android, iOS, Windows, and macOS. Make sure your devices are running the latest OS versions.
- Browsers. Modern browsers increasingly support access protocols, but there is also a nuance here. The browsers that your users usually use (Chrome, Safari, Edge) should be updated to the latest versions because they contain the necessary support for passkey authentication.
- Cross-platform use. This is one of the key advantages, but it also has certain nuances. The passkey generated on the smartphone can be used to log in to the laptop, but both devices must support the necessary protocols and be nearby. This cross-platform capability increases convenience for users, though it requires compatible hardware and software on all involved devices.
- Third-party services. Note that quite a few third-party authentication services and password managers are starting to support passkey technology. For example, Google Password Manager and iCloud Keychain. Make sure the third-party services you choose are compatible with your access keys to make the transition easier.
Also, note that older systems and programs may not support this authentication technology. You'll need to think about potential upgrades or replacements for legacy systems to fully utilize access technology in the future.
Short implementation guide
Here's a quick guide to the simplest use case for passkeys.
Please note that the implementation of this technology to more complex systems, including banking ones, is a much more complex process. This is only a simple example of how users can use passkeys without assistance.
1. Check device compatibility
To begin with, you should make sure that the operating system on your device supports passkey technology. For Google Accounts, you need an Android device or a computer running Windows 10 or later. Apple users need devices running iOS 16, macOS Ventura, or later.
2. Enable passkeys
To start using Google Passkey, you should go to the access keys setup page. Here are clear and detailed instructions on how passkeys work and how to create and activate them. Make sure your browser supports the technology, or switch to one that does.
In the case of an Apple device, you need an initial login with a traditional password. After logging in to your new device, you can create a passkey through settings. This key can be used on all your Apple devices if iCloud Keychain is enabled.
3. Secure exchange of passkeys
Sharing passkeys is pretty easy. Apple lets you share them via AirDrop with people nearby. Google provides a one-time QR code that can be scanned for temporary access without storing the passkey on the borrowed user's device.
Also, note that this technology is not yet supported in all countries. You may still need traditional passwords for some devices and browsers. Keep track of where passkeys are accepted and use a password managers.
Future Trends in Digital Authentication
The world of digital authentication is set to undergo significant transformations in the coming years. Here are some key trends to watch.
Passwordless Authentication
As you can already understand, in the future, the transition to passwordless security systems will become nearly a necessity for different industries, but especially for banking. These do not necessarily have to be passkeys (we will talk about other options later). However, passwords are becoming a thing of the past. Therefore, if you are thinking about starting a FinTech company, it is worth considering this.
Here are two main options of passwordless authentication that can be used independently or together with passkeys.
- Biometric authentication. The use of biometric data (fingerprints, facial recognition, voice recognition) is highly widespread. This method is smooth and fast, and most importantly – it is a secure authentication process, which has definitely greatly improved the user experience in many applications. This is an especially important trend for financial and banking systems that deal with sensitive data. As technology improves, biometric systems are becoming more reliable and more common.
- Behavioral biometrics. A clear example of this is behavioral biometrics. This technology uses AI and ML to analyze user behavior patterns, such as typing speed, mouse movements, and navigation habits, and thus confirm their identity. Behavioral biometrics provide continuous authentication, adding an extra layer of security and anticipating fraudulent activity without interrupting app usage.
Multi-Factor Authentication Integration
Multi-factor authentication, or MFA, has evolved into a streamlined and user-centric authentication system. This method requires users to provide two or more forms of verification to gain access to an account or system access. It is usually something your user knows (like a password that will soon be replaced with a passkey), something they have (like a smartphone), and something they are (like a fingerprint). MFA significantly reduces the risk of unauthorized access, even if one of the authentication factors is compromised.
Banks use this method to secure online accounts and mobile apps by requiring customers to provide multiple forms of verification. For instance, clients may need to enter a one-time code sent to their mobile phone or use a fingerprint scanner after entering a password. This extra layer of security helps protect sensitive financial information and prevents unauthorized access to accounts.
The future of multi-factor authentication is likely to focus on more user-friendly methods, such as biometric authentication and behavioral biometrics, mentioned above.
There is also a trend toward integrating MFA with adaptive authentication systems that adjust security measures based on context, such as the device's location and risk.
Decentralized Identity Systems
Decentralized identity systems use blockchain technology to create digital identities that users can manage themselves without relying on central authorities or databases for sensitive information. In other words, you can choose which service providers you are ready to share your data with.
This approach improves digital privacy, reduces the risk of identity theft, and gives the user more control over how their data is used. In the future, DIS will most likely develop in two main directions.
- Interoperability direction. Developers of such authentication systems plan to strengthen efforts to standardize protocols. In this way, different DIS platforms will work seamlessly together, improving user interaction and expanding their applications.
- Advanced privacy features direction. In the future, improvements in zero-knowledge proofs and encryption should further enhance privacy and security. In this way, users will be able to share only certain parts of information without revealing their identity.
Of course, Artificial Intelligence and Machine Learning remain the main forces behind the detection and prevention of fraudulent activities. These technologies already can analyze vast amounts of data to identify suspicious behavior and potential security threats in real-time, so they will be an integral part of authentication systems.
Wrapping Up
So, passkey is a technology that can simultaneously improve security posture and user experience. This reduces the need to remember and enter complex passwords while eliminating the risk of phishing and data breaches.
When should you go to them? It all depends on your readiness. Your technology stack and user devices must support modern authentication methods. In addition, you need to be prepared to deal with user education and onboarding.
It is also worth considering the possibility of introducing biometrics because it is inextricably linked with new passkey technology. It is equally important to prepare new enhanced security protocols.
Of course, it's up to you. However, over time, passwords will become a thing of the past, and you will have to look for an alternative. Therefore, the earlier you prepare for this, the less traumatic and expensive this transition will be.
At TechMagiс, we have extensive fintech expertise and a team of specialists who will be happy to answer your questions.
FAQ

What is the difference between passkeys and passwords?
Passkeys are typically longer and more complex than passwords, often generated by software, and easier to remember. Passwords are manually chosen by users and can vary in complexity.
Are passkeys more secure than passwords?
Passkeys generally offer higher security due to their complexity and variability, even if comparing password manager vs. passkey. They can be harder to crack through brute-force attacks compared to passwords.
How can businesses transition from passwords to passkeys?
Businesses can transition by implementing passkey-generating software, educating employees on passkey usage, and gradually phasing out passwords with proper training and support.
What are the challenges of switching to passkeys?
Challenges include resistance to change, compatibility issues with existing systems, and potential user training requirements. Overcoming these challenges requires careful planning and implementation.
Should individuals consider switching from passwords to passkeys?
Yes, especially for individuals concerned about online security. When comparing passkey vs. password manager, the first option provides an additional layer of protection against cyber threats, making them a worthwhile consideration.
What are the future trends in digital authentication methods?
Future trends suggest a shift towards more sophisticated biometric authentication, multi-factor authentication (MFA), and continued evolution in passkey technologies for enhanced security and usability.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy