NIST Compliance Checklist: Key Standards for Ensuring Security
Last updated:11 January 2025
Cyber threats are lurking around every corner. Did that scare you? Frightening, isn't it? In reality, security has always been a pressing issue, but today it has taken on even greater significance.
Our technological advancements make us both stronger and more vulnerable as they open the door to sophisticated new threats.
However, there's no need to panic. The key is to approach the creation of a security posture and defense system with a calm, structured mindset. Regulatory requirements play a crucial role in this process. That’s where NIST comes into play.
The National Institute of Standards and Technology (NIST) offers a set of guidelines that help organizations protect their digital assets. But where do you begin?
In our new article, we’ll share our expertise in working with security requirements for regulatory compliance and provide you with a detailed checklist. It’s your roadmap to not only achieving compliance with NIST but also maintaining a strong security posture that can withstand the test of time.
Key Takeaways
- What is NIST? Discover how the NIST sets the benchmark for cybersecurity best practices and guidelines across industries.
- NIST 800-53 framework. Learn how NIST 800-53 helps organizations secure their IT systems with flexible controls tailored to low, moderate, and high-risk environments.
- Why NIST 800-171 matters? Find out why NIST 800-171 is crucial for protecting Controlled Unclassified Information (CUI) and what it means for contractors working with government data.
- Compliance is a must. Understand how NIST compliance reduces cybersecurity risks, ensures regulatory alignment, and builds customer trust, avoiding hefty penalties.
- Security best practices. Get top tips on using tools like SIEM, vulnerability scanners, and regular penetration testing to stay compliant and strengthen your security posture.
- Real-world solutions. See how companies overcome common NIST compliance challenges, like resource limitations and complex controls, with the right strategies and expert help.
What is NIST?
The National Institute of Standards and Technology (NIST) is one of the U.S. government agencies that creates guidelines and standards aimed at improving security across various industries.
Think of it as the gold standard for cybersecurity – if you’re following NIST, you’re in good company. These guidelines are designed to help organizations manage and mitigate cybersecurity risks by providing a structured approach.
Ok, but why is compliance with NIST so important?
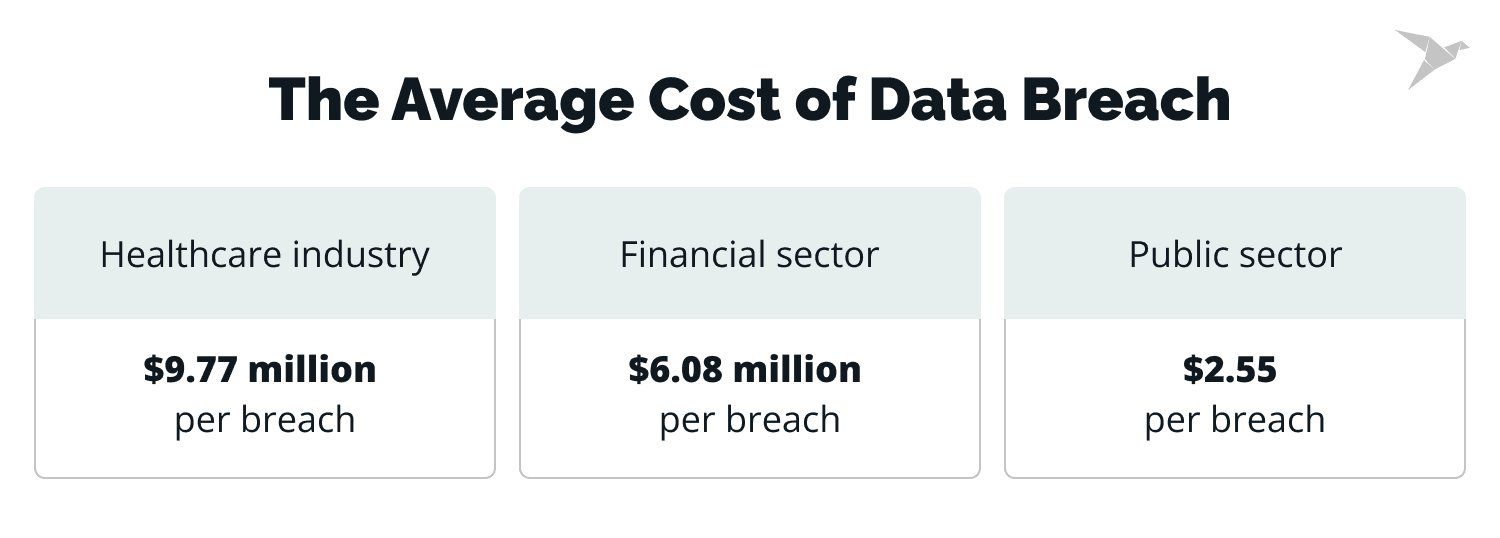
IBM Security and the Ponemon Institute report shows that the costs of data breaches are the highest in the U.S. If a security incident occurs, it comes with a price tag of $7.91 million. People assume that such leaks are always caused by criminal activity. Although 25%of the cases were caused by human error.
Between March 2022 and February 2024, the highest average cost of a data breach was detected in the healthcare industry – nearly $9.77 million. The financial sector is in second place, with $6.08 million on average per breach. And the third place belongs to the public sector and federal information systems.
Complying with NIST is like having a trusted guide in a dense jungle of data security threats. It’s not just about ticking off boxes – it’s about protecting your organization from real-world dangers through establishing proper security protocols. And it makes the possibility of data breach much, much lower.
For businesses, it means fewer risks, reduced vulnerabilities, and a more secure environment. Compliance with NIST is a badge of honor that reassures customers, partners, and regulators that you’re taking cybersecurity seriously.

Key NIST standards and frameworks include:
- NIST 800 53 compliance checklist,
- NIST SP 800-171 compliance checklist,
- NIST 800-160,
- NIST 800-37,
- NIST 800-39,
- NIST Cybersecurity Framework (NIST CSF compliance checklist).
Today we will take a closer look at them from the most essential to additional.
The NIST Special Publication 800-53/NIST 800-53
What is NIST 800-53?
NIST 800-53 is a must-know cybersecurity framework that provides a detailed catalog of controls for protecting information systems and personnel security. Originally designed for federal agencies, it's become a go-to resource for private companies wanting to level up their security game.
This framework lays out effective strategies for dealing with risks, configuration management, and adapting security measures based on the organization’s specific needs and impact levels.
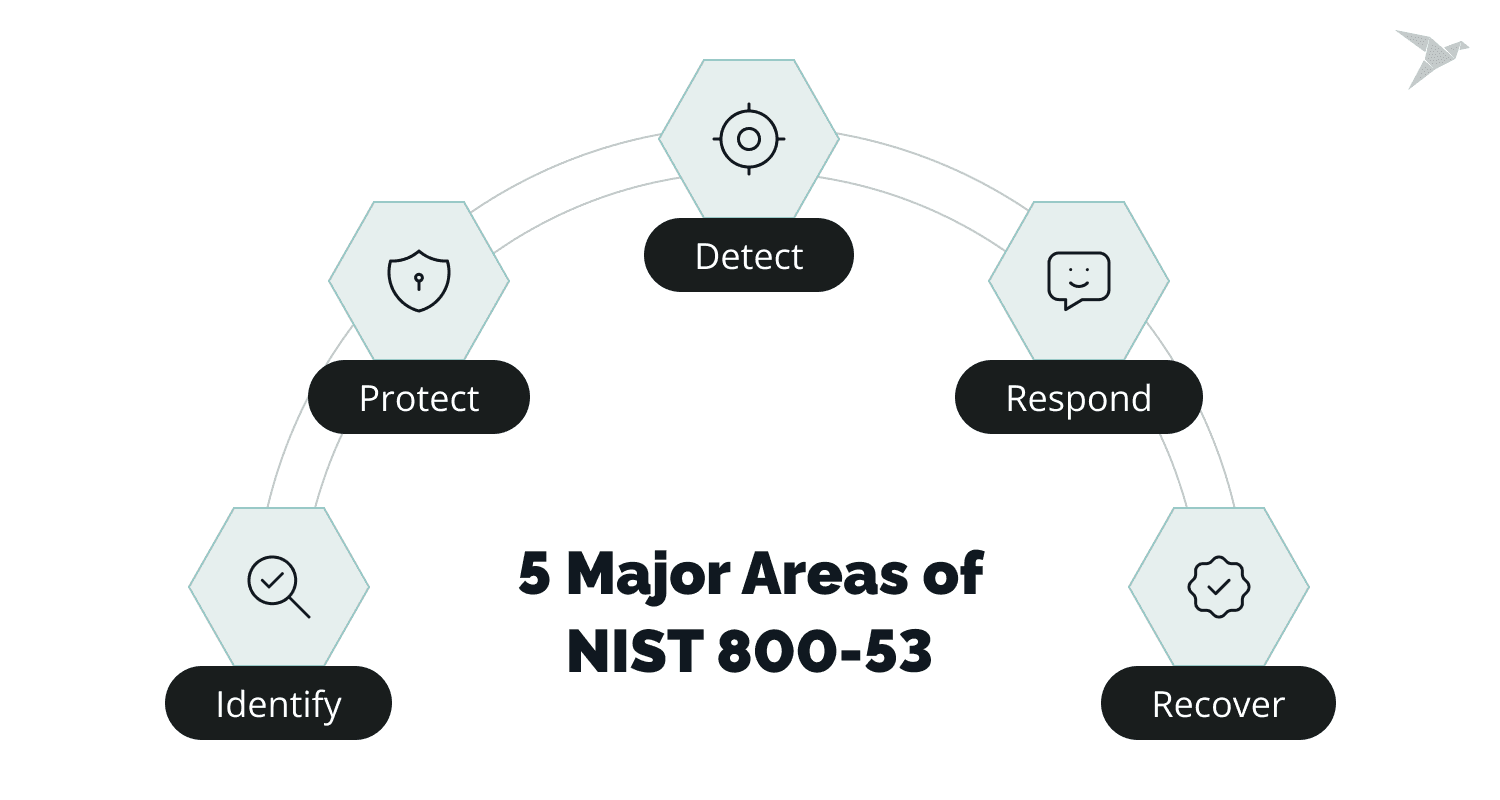
Five major areas and control families of NIST 800-53
One of the standout features of NIST 800-53 is its flexibility. The framework is broken down into five major areas:
- Identify,
- Protect,
- Detect,
- Respond,
- Recover.
These areas cover everything from asset management to continuous threat monitoring and incident response.
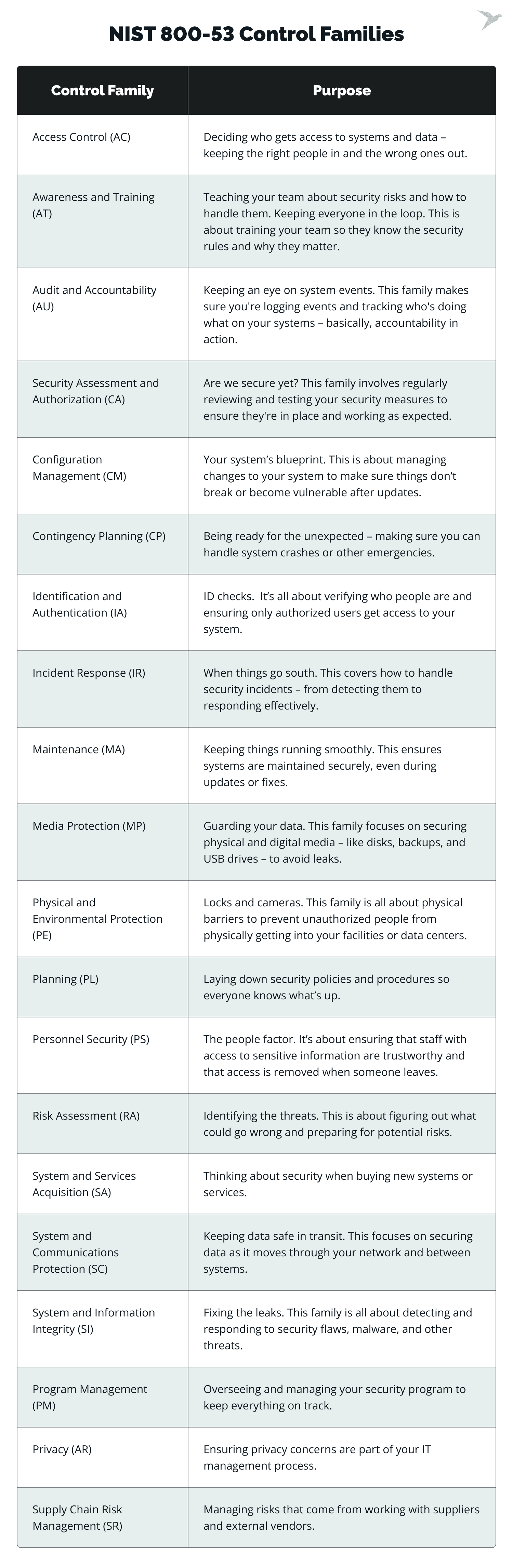
Also, the NIST 800-53 compliance checklist includes 20 families packed with over 1,000 individual security and privacy controls. All of them are designed to help organizations secure their IT environments, especially those handling sensitive or regulated data.
NIST 800-53 control families

NIST 800-53 risk levels
The controls are categorized into three risk levels – low, moderate, and high – depending on the impact they have on the organization’s operations. Businesses can implement each control at all these levels.
- Low impact. Here, you’ll find risks with minimal harm to operations if breached. At this level, you require basic security controls (like simple password policies, for instance).
- Moderate impact. Such risks can have serious adverse effects but are not catastrophic. Moderate controls may include enhanced logging, multi-factor authentication, and more comprehensive incident response.
- High impact. This list includes severe or catastrophic consequences, such as national security risks or major business disruption. High-impact controls often include advanced encryption, continuous monitoring, and detailed contingency plans.
We know that getting compliant with NIST 800-53 can be a bit of a process. It often requires new policies, reconfigured systems, and possibly new tech investments.
The good news is that once set up, it helps ensure that an organization is well-prepared to handle evolving cyber threats. Plus, assigning a dedicated team to manage and update these controls is key to maintaining compliance in the long run.
The NIST Special Publication 800-171/ NIST 800-171
What is NIST 800-171?
NIST 800-171 is all about protecting Controlled Unclassified Information (CUI) in non-federal systems. If you’re a contractor or organization working with federal agencies, especially the Department of Defense (DoD), this standard is your roadmap for keeping sensitive information secure.
In simple words, the goal of NIST 800-171 is to make sure that even though the data isn’t classified, it’s still handled with care – whether it’s being accessed, stored, or shared. NIST 800 171 compliance checklist outlines 17 control families.
Although all 17 families can be found in NIST 800-53, t not all baseline controls from NIST 800-53 are part of NIST 800-171. You can find more details in our downloadable NIST compliance checklist.
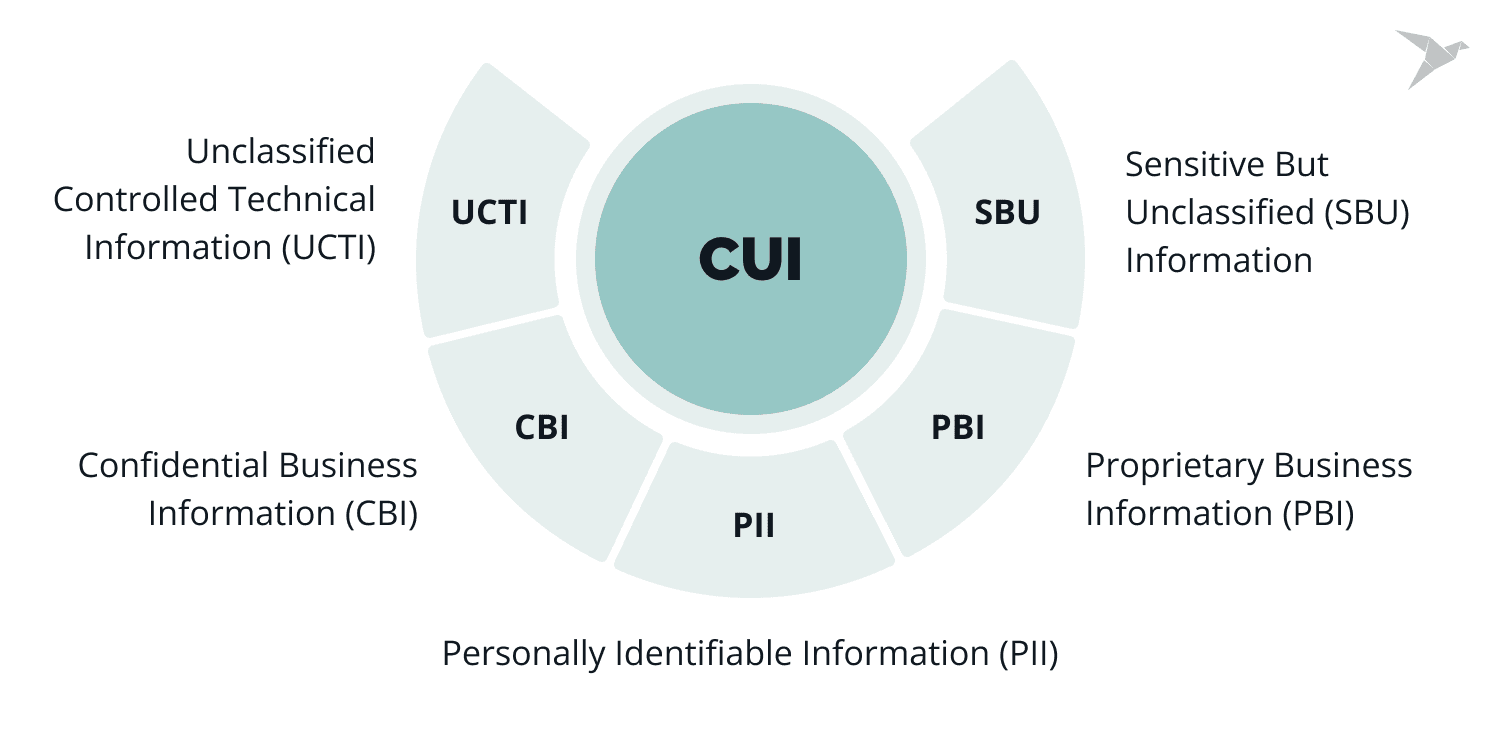
Controlled Unclassified Information
So, what exactly is CUI? Think of it as a catch-all term for sensitive info that isn’t top secret but still needs protection. This could include things like
- Personally Identifiable Information (PII),
- Proprietary Business Information (PBI),
- Unclassified Controlled Technical Information (UCTI),
- Confidential Business Information (CBI),
- Sensitive But Unclassified (SBU) Information.
Basically, if a law or government policy says it needs safeguarding, it falls under CUI.
Who needs to follow NIST 800-171?
If you’re a contractor, subcontractor, vendor, or any company working with government data, especially for defense contracts, the NIST 800171 compliance checklist is likely required.
It’s crucial for anyone handling CUI on behalf of a federal agency to follow these guidelines to keep that data secure. The Department of Defense (DoD) even includes this requirement in its contracts through the DFARS clause 252.204-7012.
Whether you’re a defense contractor or a manufacturer in the supply chain for the DoD, NASA, or other federal agencies, following NIST 800-171 is essential for doing business and safeguarding sensitive information.
Other Relevant NIST Standards
Besides the big hitters like NIST 800-53 and 800-171, there are a few other important NIST standards and frameworks you should know about.
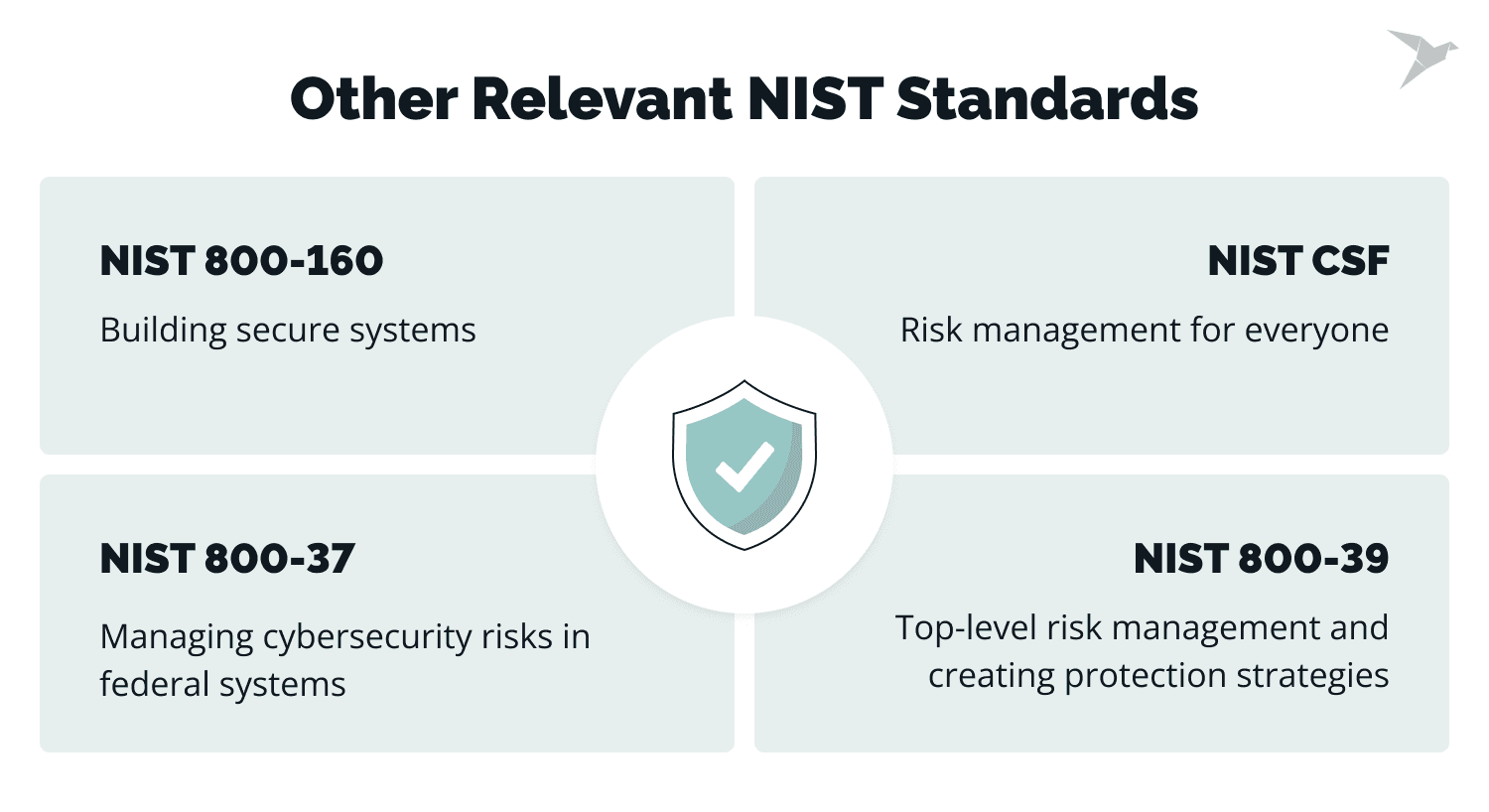
NIST 800-160
This one’s for those who are into systems engineering. NIST 800-160 focuses on building secure systems from the ground up.
It’s packed with practical advice on how to integrate security into every stage of system design and development. Whether you’re designing software, hardware, or networks, this publication helps make sure security is baked into the final product.
NIST Cybersecurity Framework (CSF)
The CSF is super flexible and widely adopted across industries. It’s more like a guide than a strict rulebook. It helps organizations of all sizes manage and reduce their cybersecurity risks by offering a structure that’s easy to customize based on your specific needs.
In essence, the CSF is all about identifying risks, protecting assets, detecting threats, responding quickly, and recovering quickly if something goes wrong.
NIST 800-37
This is the go-to for risk management. NIST 800-37 provides a step-by-step process for managing cybersecurity risks in federal systems. It’s all about continuous monitoring and assessment to make sure systems stay secure over time, not just during their initial setup.
NIST 800-39
If you want to take a broader look at risk, NIST 800-39 is your guide. This one steps back and helps organizations look at risk management from a higher level. It’s about creating an overall data protection strategy for dealing with risk across the entire organization instead of just focusing on specific systems or departments.
Benefits of NIST Compliance
There are a lot of benefits of being compliant with NIST. Let’s take a look at the most significant of them.
Enhanced security: fortifying your digital castle
Think of your organization as a digital fortress. Compliance with regulatory requirements, and NIST especially, acts like solid walls, watchtowers, and drawbridges that keep unwanted intruders at bay.
Following NIST guidelines isn’t just locking the door. It’s setting up an entire defense system that anticipates threats before they even reach your gates. It also provides a clear framework for identifying vulnerabilities and strengthening weak points, ensuring your data stays safe and sound.
Regulatory compliance: keeping the red tape in check
Navigating regulatory requirements can sometimes feel like walking through a minefield – one wrong step, and you're hit with fines or legal headaches. NIST acts as your map, guiding you safely through this complex terrain.
Adhering to NIST standards, you're not only meeting many of the industry's regulatory obligations but also staying ahead of the curve. It’s a surefire way to check off those compliance boxes with confidence, avoiding costly penalties and ensuring peace of mind.
Customer trust – your badge of honor
Trust has always been and is everything. It is really hard to earn but so easy to lose. When you achieve compliance with NIST, you’re basically wearing a badge that says, "We take your security seriously."
When customers see that you're NIST compliant, they're more likely to trust you with their sensitive information. It’s the equivalent of shaking hands with your clients and saying, "We've got this covered," which helps build long-term relationships and boosts your reputation in the marketplace.
Tools and Resources for NIST Compliance
- SIEM (Security Information and Event Management) tools. These tools keep an eye on your system, tracking and logging security events. They make it a lot easier to meet NIST’s requirements for logging and auditing – basically, they do the heavy lifting for you.
- Vulnerability scanners. They’ll help you scan your systems for weak spots and fix them so you're always on top of NIST compliance. Pay attention that the scanners are fully automated, and they can miss some vulnerabilities. That’s why it is essential to get penetration testing services.
- EDR (Endpoint Detection and Response). These platforms provide advanced threat detection at the endpoint level (your devices and systems). They’re key for handling incidents under NIST’s incident response requirements.
- Access Control Solutions. These are identity and access management (IAM) tools that can help you control who gets into your systems. These are super handy for meeting NIST’s access control guidelines.
- Audit and Compliance Management Platforms. With these solutions, you can keep track of your compliance efforts, generate reports, and stay on top of NIST’s requirements. These tools make managing it all much simpler.
- Data Encryption Tools. They encrypt your sensitive info, ensuring that your data protection measures line up with NIST’s standards.
- Policy and Procedure Management. Such platforms can assist you in managing your internal policies and documents, keeping everything in line with NIST’s planning and governance requirements.
You don’t have to apply all these tools in practice – just choose some of them that can make your security management easier. In most cases, the best way to find suitable applications is to ask experts who provide security testing services. They’ll perform your system audit and choose tools in accordance with your requirements, budget, and specific requirements.
Penetration testing for Coach Solutions web application

NIST resources
- NIST Computer Security Resource Center (CSRC)
The go-to site for publications, standards, and guidelines, including NIST SP 800-171 and other key documents for cybersecurity compliance. - NIST Special Publications (SP) Series
A repository of NIST’s special publications, which cover various topics in information security, including compliance guides and best practices. - NIST Cybersecurity Framework
A resource for organizations to manage and reduce cybersecurity risks, often used in conjunction with NIST compliance efforts.
Common Challenges and Solutions
From our experience, achieving NIST compliance isn’t always a smooth ride. Most organizations, especially when just starting, run into a few common hurdles. But don’t worry – we’ve also seen how companies successfully overcome these challenges).
So, here’s what we’ve learned.
What doesn’t kill you makes you stronger: challenges in achieving NIST compliance
Complex requirements
One of the biggest headaches is just how detailed and complex NIST requirements can be. It can feel overwhelming trying to break down the hundreds of controls and figure out where to even start.
Limited resources
We’ve noticed that many organizations, especially smaller ones, struggle with having enough resources – whether it’s budget, staff, or expertise. It’s tough to allocate the right amount of time and people to focus on compliance.
Lack of awareness and training
A lot of companies underestimate how important it is to have everyone on the same page when it comes to security. Without proper training, even the best policies won’t work if employees don’t understand them.
Keeping up with changes
NIST guidelines aren’t static. They get updated to reflect new security threats and tech advancements. It can be challenging to stay current and continuously adapt your compliance program.
What to do? Solutions and best practices
From our experience, the best way to overcome even the most complex challenge is to break it down into manageable pieces.
So, start by prioritizing the controls that make the most sense for your organization. In most cases we’ve managed, focusing on key areas like access control, incident response, and data encryption first made the process much more manageable. You don’t have to tackle everything at once.
Once the foundation is built, you can move to other best practices.
- Use automation tools
When resources are tight, automation is your best friend. Tools like SIEM systems, vulnerability scanners, and access management platforms can handle a lot of the grunt work for you, helping you stay compliant without burning out your team.
- Train your team (continuously)
Compliance isn’t just an IT problem. Everyone from top-level management to everyday staff should understand the security policies in place. Regular, engaging training sessions can go a long way. In our experience, a well-trained team is the backbone of strong security practices.
- Create a plan for continuous monitoring
Staying compliant means you can’t just “set it and forget it.” Set up a system for regularly reviewing and updating your security controls to keep up with NIST changes and evolving threats. It’s an ongoing process, but having a solid monitoring plan makes it easier.
- Regular penetration security testing
We are living in the future, and process automation is a must. However, nothing can beat human expertise (not yet).
One of the best ways to ensure you’re meeting NIST requirements is by testing your defenses. From our experience, regular penetration testing and security assessments are essential. These tests simulate real-world attacks on your systems to identify vulnerabilities before the bad guys do. Hiring ethical hackers can be super effective in uncovering weak spots.
Combined with vulnerability assessments, pen tests can help to identify and address all the potential flaws in your environment. It will keep your security posture strong and help you stay ahead of potential threats.
So, you can check the list of the top penetration testing companies and choose the one.
- Social engineering services
Another key area we’ve seen organizations overlook is the human factor. Social engineering tests are critical to evaluating how your team reacts to phishing attempts, fake calls, and other manipulative tactics. From our experience, using social engineering services helps you identify weak points in employee behavior and security awareness.
Services like simulated phishing campaigns and impersonation tests can train your staff to recognize and avoid potential scams. These assessments not only test your technical defenses but also help strengthen your overall security culture, aligning with NIST’s emphasis on awareness and training.
- Get expert help if needed
Sometimes, bringing in outside expertise can save a lot of headaches (in most cases, to be honest). Whether it’s hiring a consultant or using managed services, this can ensure you’re covering all your bases, especially for the more technical aspects of compliance.
When it comes to NIST compliance, you can choose someone with broader expertise (in ISO 27001 consulting services, for instance). From our own experience, seeing the full regulatory picture helps to find connections between different requirements and ensure full compliance.
As you can see, with proper help and a well-suited strategy, achieving NIST compliance becomes a much more realistic goal. Incorporating regular penetration testing, social engineering services, and automated tools into your security program ensures both your systems and your people are prepared for potential threats.
Final Thoughts
As you can see now, NIST compliance isn't just a checkbox but a strategic move to safeguard your organization's digital assets. We've covered a lot of ground in this article, from understanding the basics of NIST and diving into frameworks like 800-53 and 800-171 to practical tips on overcoming compliance challenges. With the right tools, training, and continuous monitoring, you can build a security posture that keeps you compliant and resilient against future threats.
Achieving NIST compliance may seem overwhelming, but breaking it down into manageable steps makes it much more possible. And don't forget – tools like SIEM systems and vulnerability scanners are your best friends when resources are limited. However, nothing beats human expertise, especially when it comes to regular penetration testing and social engineering assessments.
If you're feeling uncertain about where to start or how to maintain compliance, don't hesitate to reach out to us. We're here to provide expert guidance in preparing your security system. We can navigate this cybersecurity maze together to make this journey less daunting and expensive for you.

FAQ

Which NIST standards are most relevant for organizations?
The most relevant NIST standards for organizations include NIST 800-53 and NIST 800-171, which provide comprehensive guidelines for securing information systems and protecting sensitive data.
How can my organization get started with NIST compliance?
Start by identifying and classifying sensitive data, implementing access control measures, developing an incident response plan, conducting security training, performing risk assessments, and continuously monitoring and improving security measures.
What are some common challenges in achieving NIST compliance?
Common challenges include resource constraints, complexity of the standards, lack of expertise, and resistance to change. Solutions include leveraging compliance tools, seeking expert guidance, and adopting best practices.
What tools can help with NIST compliance?
Various compliance tools, such as risk assessment software, access control systems, and incident response platforms, can aid in achieving NIST compliance. Additionally, resources from the NIST National Checklist Program can be helpful.
What are the benefits of NIST compliance?
Benefits of NIST compliance include enhanced security, meeting regulatory requirements, and building customer trust by demonstrating a commitment to protecting sensitive information.
Where can I find more information about NIST compliance?
More information can be found on the NIST website, as well as through resources like the NIST National Checklist Program, compliance blogs, and industry publications.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy