Cost-effective AWS Security Best Practices: Our Experience and Tips
Last updated:18 January 2025
It's time to bust the myth: robust security doesn't have to be expensive.
For businesses operating on Amazon Web Services (AWS), cloud security is a top priority. However, maintaining your AWS infrastructure secure while keeping costs in check can be hard.
This article explores AWS security best practices with a focus on cost-effective methods. We share not just general solutions, but our valuable experience over the years of practice in the field.
The article is rich with insights from experts who contributed to it, they are:
- Victoria Shutenko, security engineer and penetration tester at TechMagic
- Rotem Levi, cloud security architect at CloudZone
- Victor Grenu, cloud security consultant at zoph.io
AWS WAF: A Robust Protection Against Attacks
AWS Web Application Firewall (WAF) is a managed web application firewall service that helps you protect your web applications at the application layer from common web exploits that may affect application availability, compromise security, or consume excessive resources.
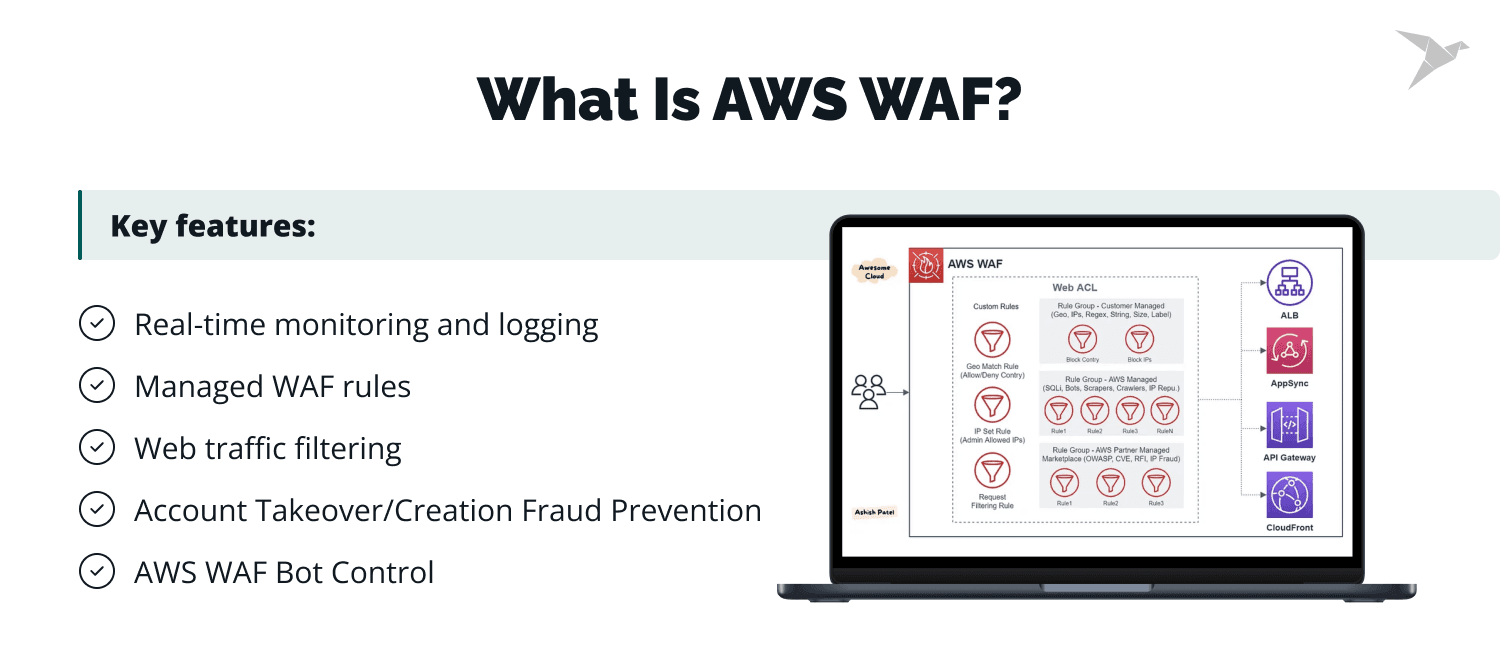
AWS WAF provides robust protection against web application attacks such as:
- SQL injections
- Cross-site scripting (XSS)
- Bot attacks
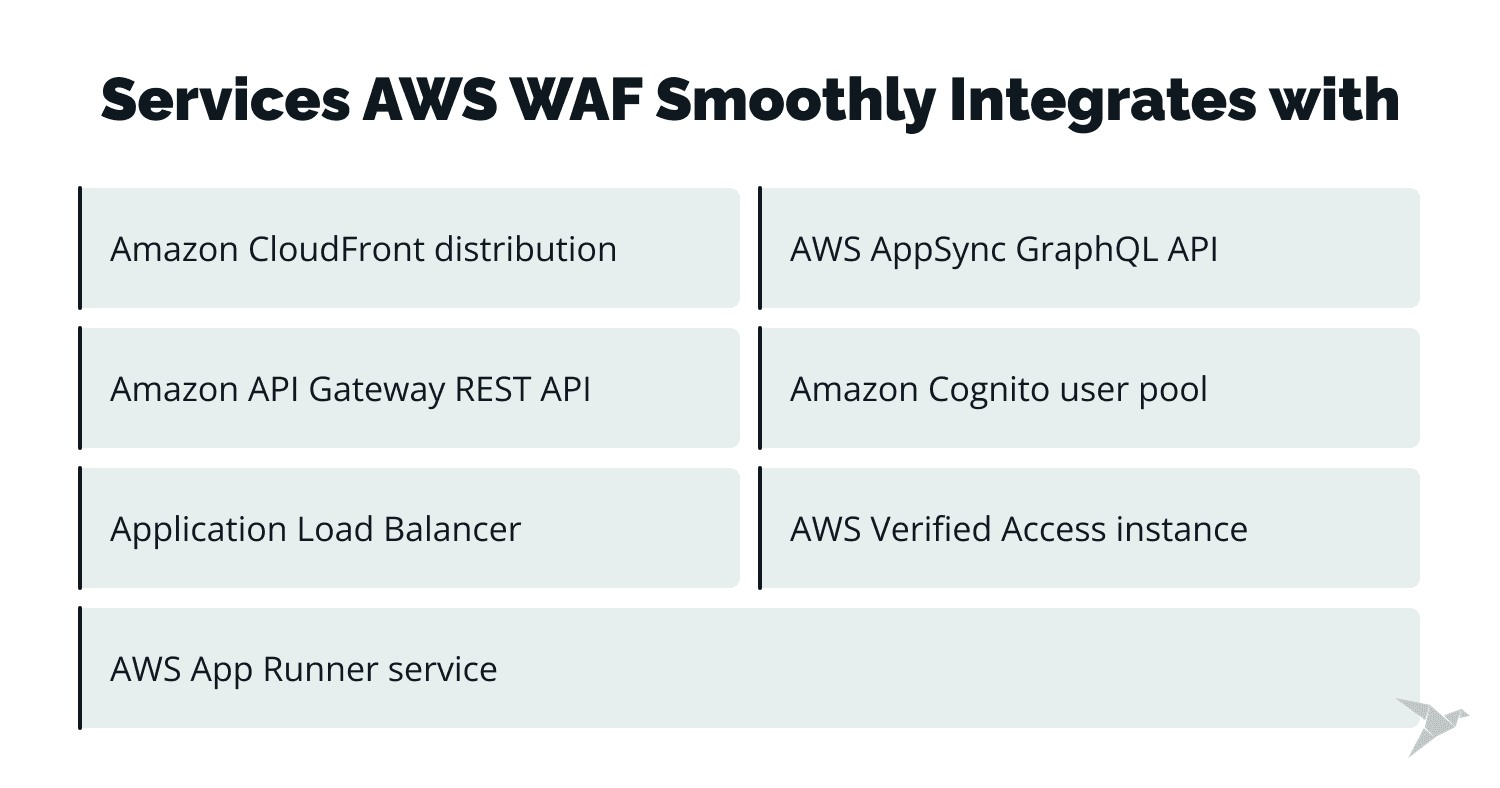
A great benefit is that AWS WAF smoothly integrates with services like Application Load Balancer, Amazon API Gateway (REST APIs), Amazon CloudFront, AWS AppSync (GraphQL APIs), Amazon Cognito User Pool, AWS Verified Access, and AWS App Runner to enhance the security of your application and infrastructure.
AWS WAF deployment options
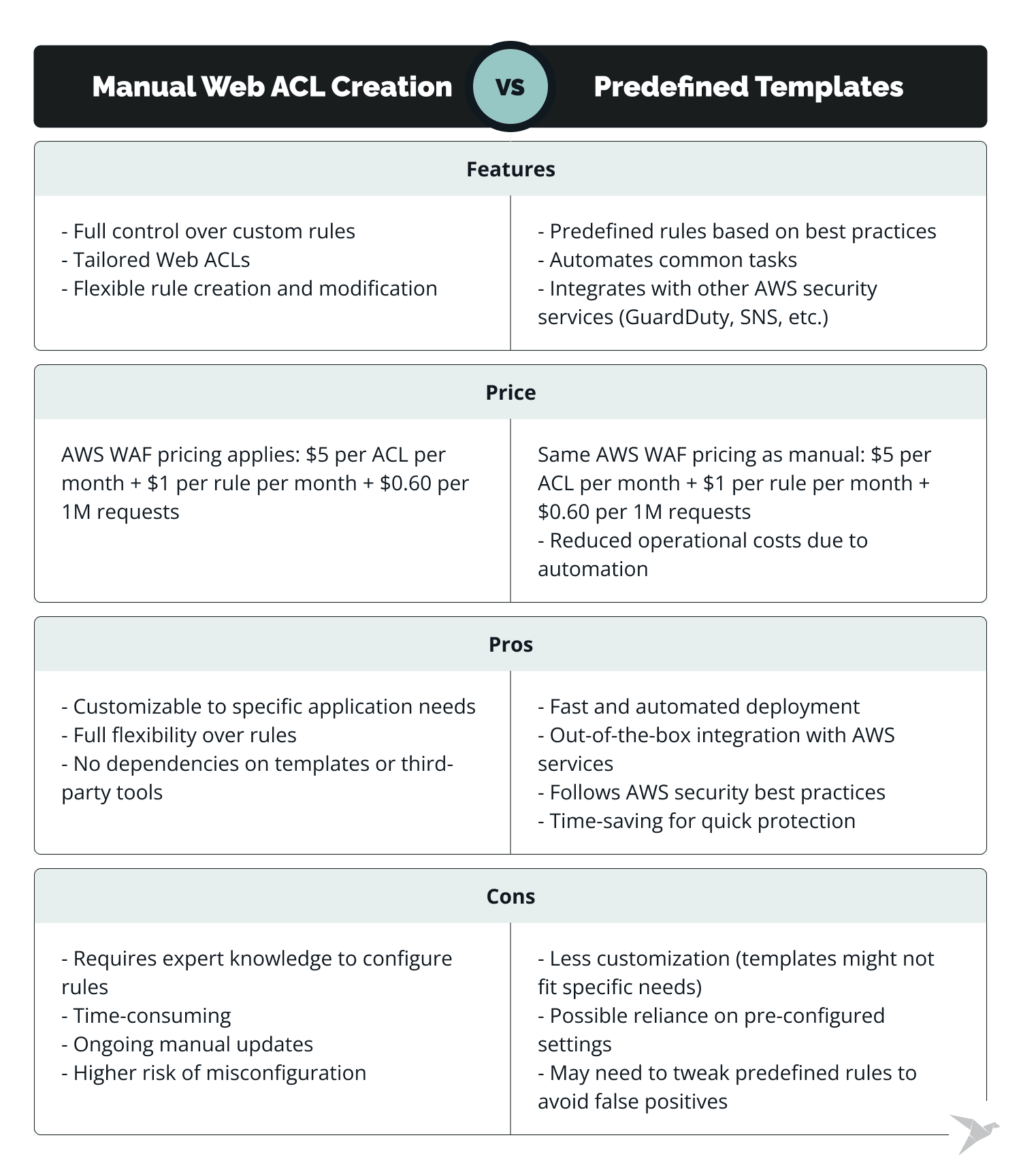
AWS WAF can be deployed in several ways, each with its own cost considerations. The two most common approaches are manually creating a Web ACL (Access Control List) from scratch or using predefined templates, for example, a solution called Security Automations for AWS WAF, delivered as a CloudFormation template.
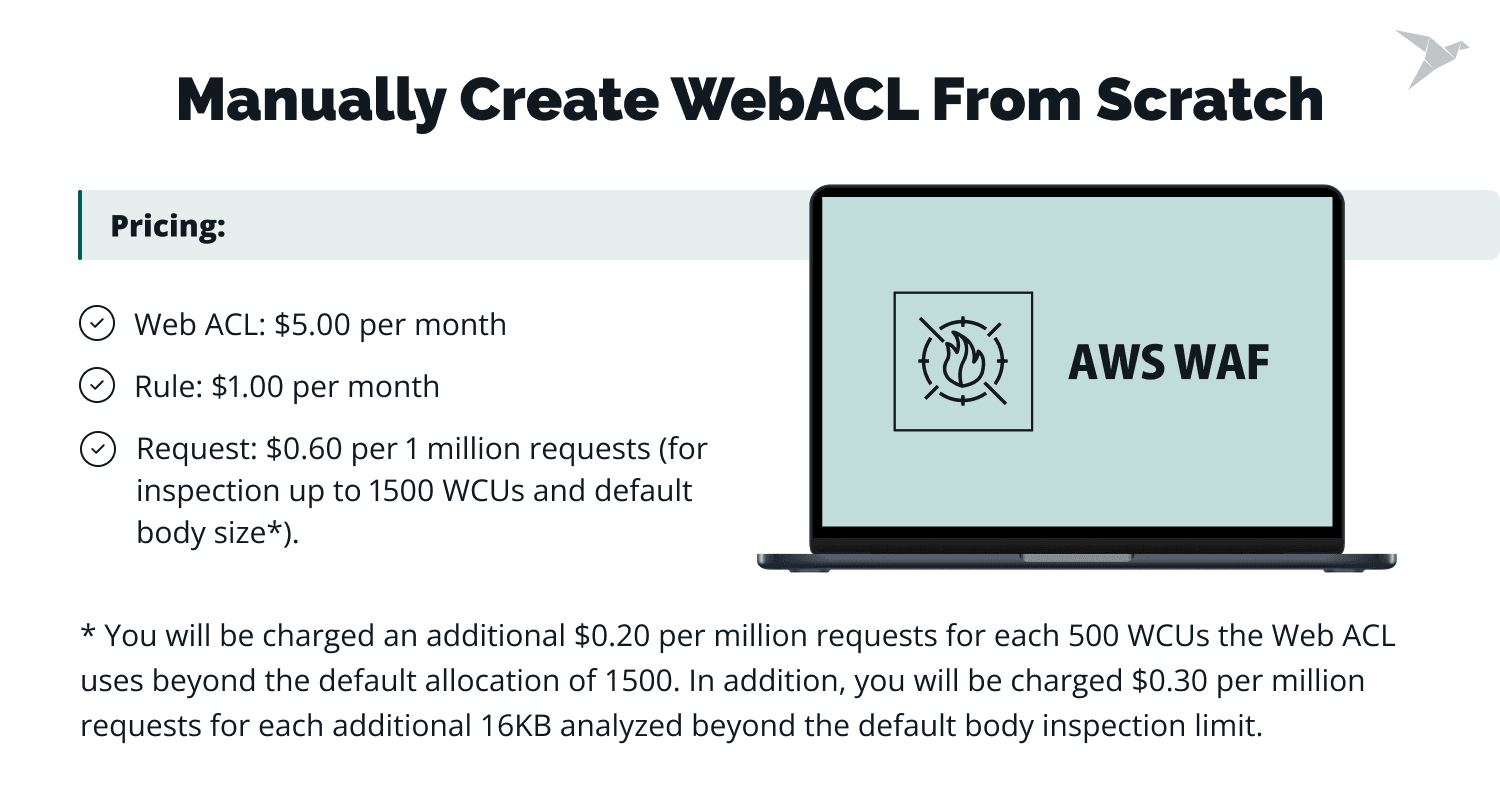
The Web ACL is a core component of your AWS WAF instance that holds all your rules and is used to track and inspect requests, blocking them if necessary. The manual approach offers flexibility but requires more effort and expertise. A Web ACL costs $5 per month, with additional costs of $1 per rule and a fee for processing requests: $0.60 per 1 million requests.
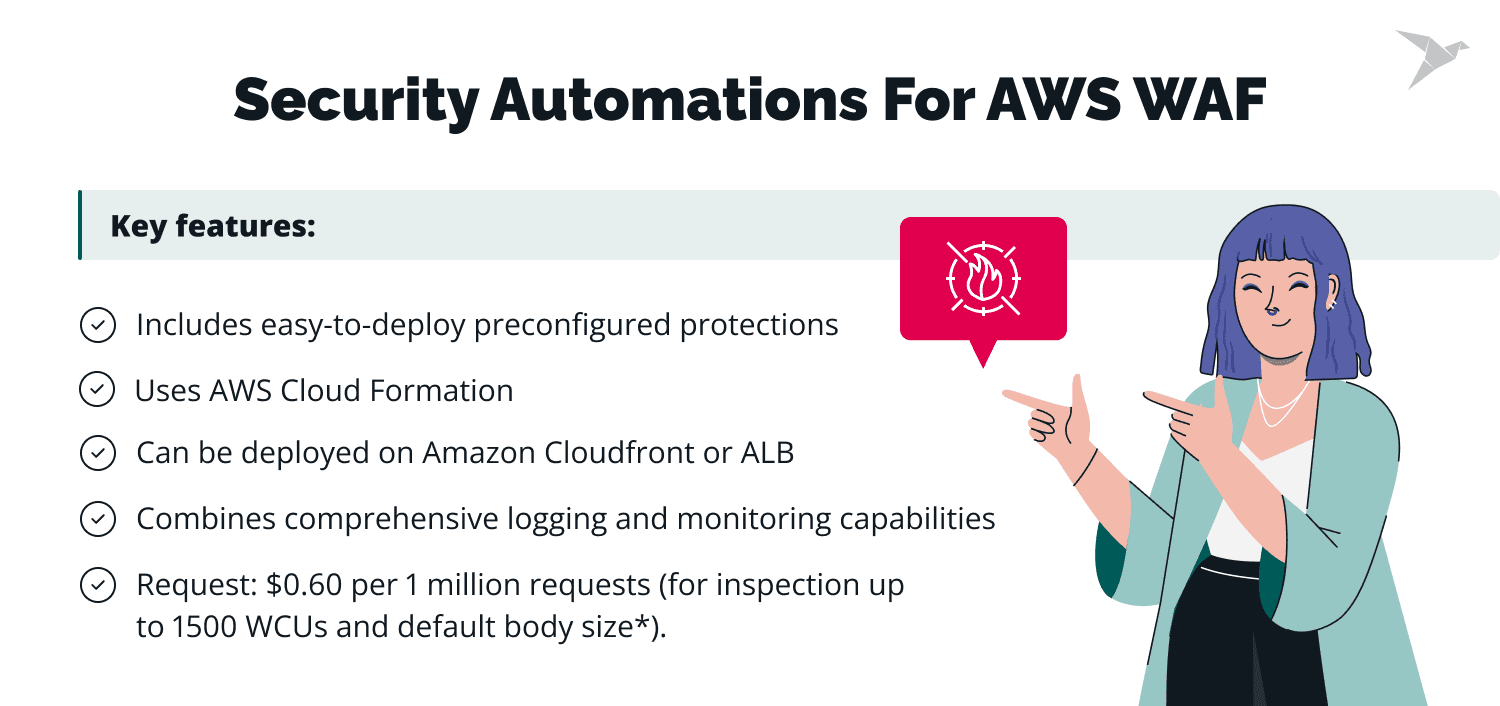
The automated approach minimizes the effort required for updates and helps you track changes to your Web ACL rules. This solution helps automatically deploy all required components and analyze processed requests to prevent common attacks such as SQL injections and XSS. It utilizes third-party threat intelligence to stay updated on the latest threats and malicious IPs, effectively blocking them.
Learn how threat modeling and attack emulation can protect your AWS environment

AWS WAF pricing and cost optimization
Let’s now have a look at the pricing example of Security Automations for AWS WAF:
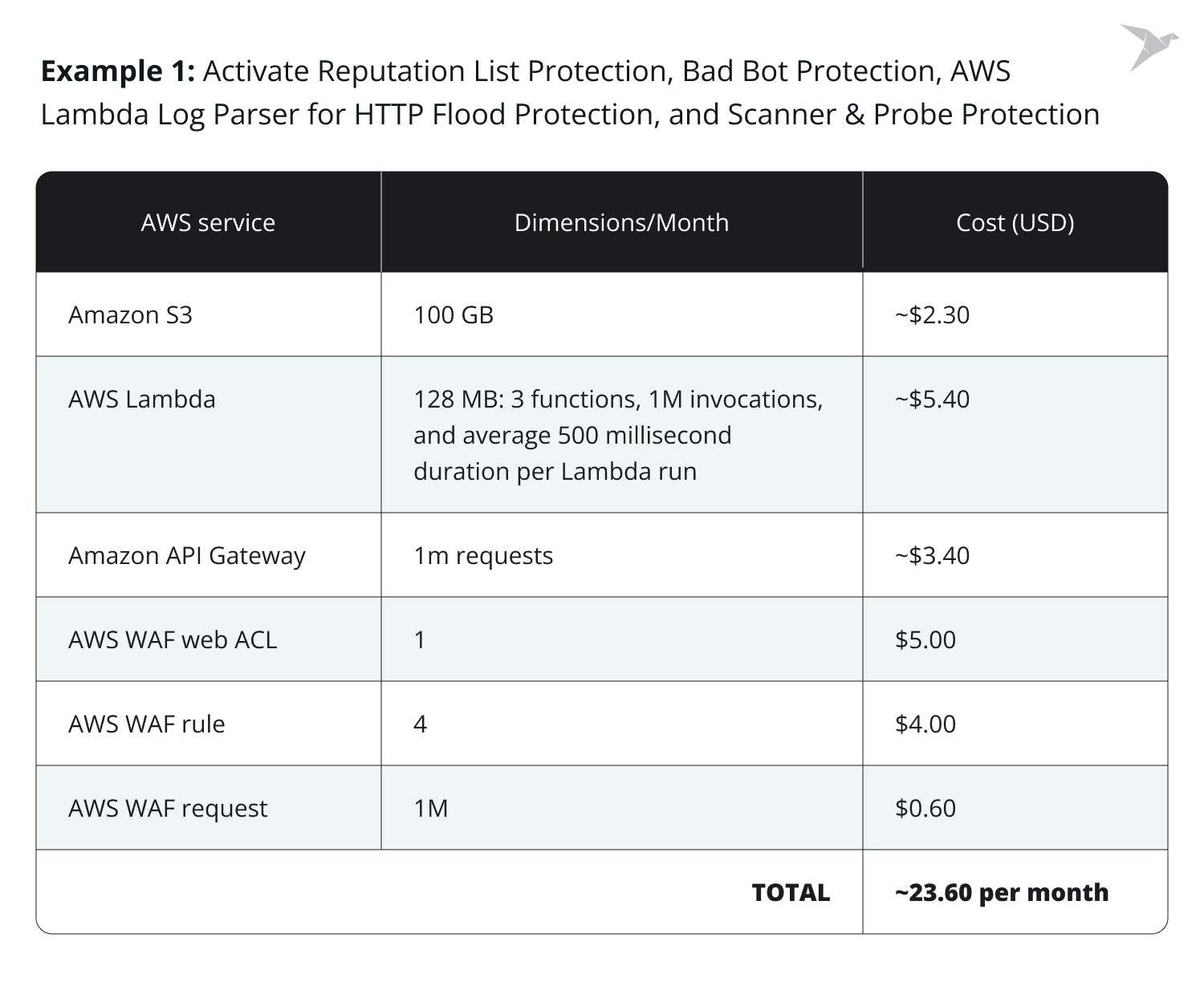
Overall, the final costs you spend depend on the selected configuration. There is a basic CloudFormation template and various available options to choose from, which will affect the total costs. For example, if you use Amazon S3 for log storage, 100 GB will cost around $2 per month.
Lambda functions used for various tasks, including syncing malicious IP addresses from third-party services, could cost around $5.40 per month if you average 1 million invocations at 500 milliseconds per run. Additionally, for Amazon API Gateway, processing 1 million requests would cost nearly $4.
As for the Web ACL, costs reach around $5 per month. For every AWS WAF rule, let's say you have four rules, each will cost an additional $1 per month. In total, that’s $9. Additionally, for each million analyzed requests, you'll pay $0.60. So, for this specific configuration, you would pay approximately $23.60 per month.
You may read the article AWS WAF Pricing explained for more pricing examples.
Based on our experience, regardless of the deployment method you choose, we recommend automating deployment using CloudFormation templates for cost optimization, faster speed, and consistency.
In case something goes wrong, you can easily revert to a previous version that worked well. This is particularly important for large applications, where distinguishing between valid and invalid traffic is crucial. Version control and the ability to quickly deploy a new AWS WAF instance in any of your accounts are essential.
You can also use the AWS WAF Role Manager to manage AWS WAF across different accounts. However, maintaining one policy will cost about $400 per month, and if you need several policies for production and test workloads, the costs can add up significantly. This is why using CloudFormation for deployment and connecting it to your GitHub account can save you a lot of costs.
If you consider third-party solutions like Security Automations, make sure to:
- Review the solution architecture beforehand to ensure you are using the right components to avoid creating unnecessary infrastructure and extra costs.
- Analyze your current needs and existing expertise to determine the best deployment approach for your situation.
- Track the total number of Web ACL capacity units. Once you exceed 1,500, you'll incur extra costs. Therefore, it's crucial to monitor your rules for efficiency and optimize them to meet security needs without exceeding limits.
AWS WAF rules: effective practices and cost management
AWS WAF rules are the building blocks for protecting your web applications from threats. It is important to understand how to create, manage, and prioritize these rules to protect against a wide range of web threats and ensure your application remains secure.
There are two types of rules: custom rules (which you set up according to your project requirements) and managed rules (predefined and maintained by AWS or third-party providers).
- Custom rules allow for greater control and customization based on specific use cases but require deep knowledge of web application security.
- Managed rules offer a quick-start solution, protecting your applications from common threats without the need for in-depth expertise. However, they can be slightly more expensive depending on the vendor.
Some of the rules are free, while others are paid and developed by recognized companies with expertise in AWS WAF security. You can implement these rule sets to deploy basic protection tailored to your needs. For example, base rule sets can be used to deploy protection for a LAMP stack, providing you with a ready-to-use AWS WAF instance with all rules managed by AWS.
We’ve prepared some tips on managing AWS WAF rules. Here they are:
Optimize web ACL capacity units
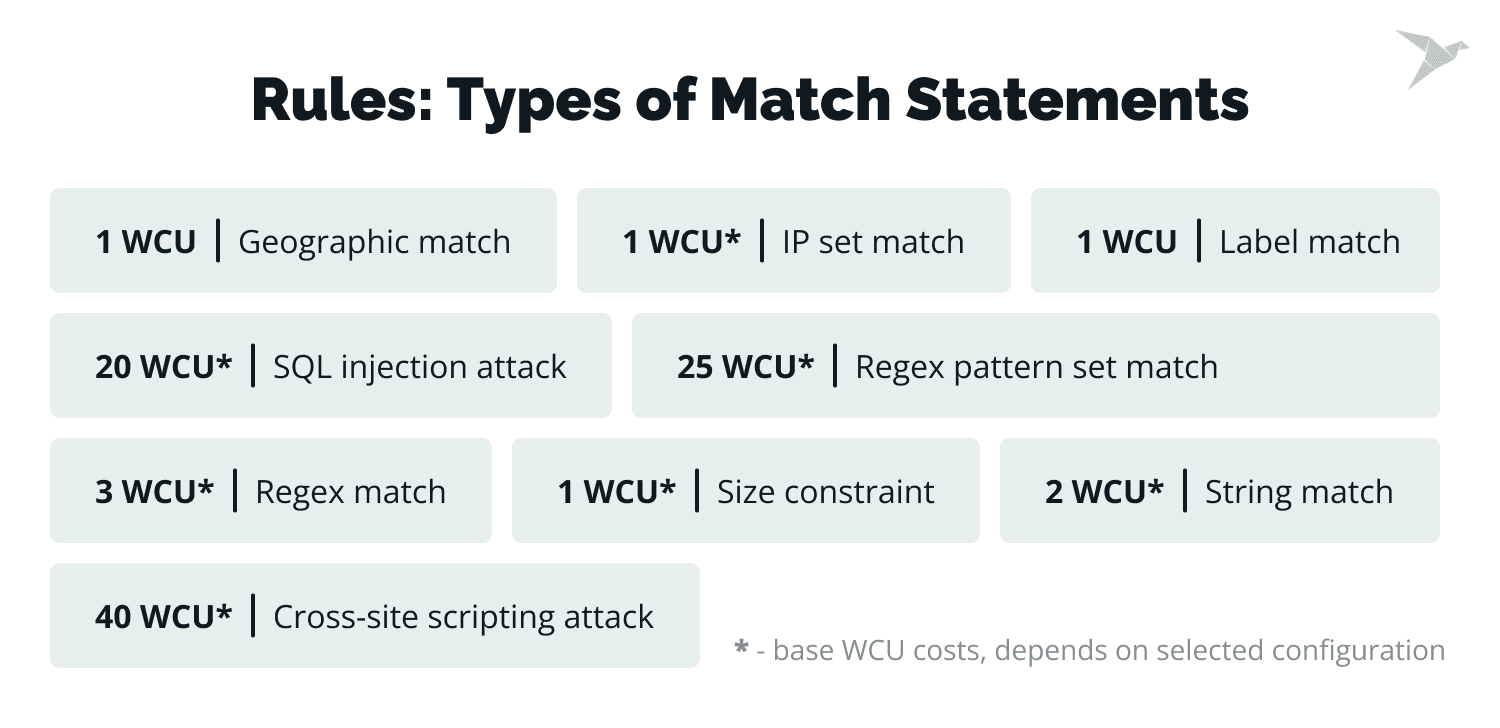
Note that AWS WAF rules have a capacity unit limit of 1,500 Web ACL units. Pay attention to how match statements (e.g., string match or IP set match) affect this limit. For endpoints with minor differences, use regex statements instead of multiple string match statements. This reduces the number of capacity units consumed.
Use match statements efficiently
Pay attention to the fact that string match is commonly used for detecting SQL injections, cross-site scripting, and more. As for regex match, it is Ideal for similar endpoints to prevent multiple string matches, helping you stay within your capacity limits. There is also IP set match – another common match type, particularly for restricting or allowing traffic based on specific IPs.
Use combine and nest statements for cost optimization
You can use nested statements and combine checks to inspect requests thoroughly while reducing false positives. Where possible, rely on regex matches instead of string matches for cost efficiency, especially when many requests are alike.
Adjust sensitivity levels
For match statements like XSS or SQL injection, set the sensitivity level to low at first to avoid false positives and to conserve capacity units. High sensitivity can increase capacity usage and potentially lead to overuse of your Web ACL limit.
Start with a basic setup
Begin with a baseline of essential rules to cover critical security needs, then gradually add new rules as needed. This approach helps to save costs and ensures your WAF focuses on real threats. Avoid deploying all rules at once – extend your setup in stages to monitor performance and maintain a balance between security and cost.
Use IP reputation lists
Connect external threat intelligence services to leverage up-to-date IP reputation lists. This helps you stay informed about current threats without manually inspecting each request or URL. These lists reduce the need for in-depth analysis of URL query parameters and request bodies, freeing up resources and improving efficiency.
These effective practices will help you optimize your AWS WAF setup, balancing protection, cost, and performance while maintaining flexibility for future rule extensions.

AWS WAF logging and monitoring: practical tips
Once AWS WAF is deployed, it's critical to implement proper logging and monitoring to ensure real-time insights into your infrastructure. Let’s consider the key points!
Choose the right log destination
Select the most appropriate log destination for your AWS WAF logs. You can use Amazon S3, CloudWatch Logs, or Kinesis Data Firehose. For long-term storage and cost-efficiency, S3 is a great option, especially since you can apply lifecycle policies to automatically manage and reduce storage costs over time.
Establish a log format
Define a clear log format to ensure your logs are structured for easy processing and analysis later on. This step is crucial for efficient log management and troubleshooting.
Implement log filtering
Set up log filters based on rule actions or labels. This reduces the volume of logs you store by keeping only the most relevant logs. Ensure you define default behavior for logs that don’t match the filters – typically, dropping them helps minimize unnecessary storage.
Use rule actions for filtering
Initially, filter logs based on all rule actions. As you refine your setup, switch to filtering based on “block” and “count” actions to focus on essential data without overloading your storage.
Leverage rule labels for complex setups
When managing more than ten rules, use rule labels to enhance your filtering system. Simple filters may not be enough for larger rule sets, and labels offer more granular control over the data you retain.
Minimize log storage by dropping irrelevant data
By default, drop logs that don’t meet your filtering criteria. This practice is particularly effective in reducing the number of stored logs during automated attacks, helping to keep costs low while maintaining necessary logging for analysis.
AWS WAF Monitoring Lambda: Efficient Security Analytics for Retrospective Analysis
One of the challenges with AWS WAF is the limited retention period for reviewing recorded requests by default. Only the last three hours of logs are available. This limitation hinders the ability to perform retrospective analyses on potential threats.
To solve this, TechMagic’s security team developed AWS WAF Monitoring Lambda, a custom solution that enhances your AWS WAF by providing daily analytics based on WAF logs. This solution allows your security team to identify ongoing attacks and take proactive measures.
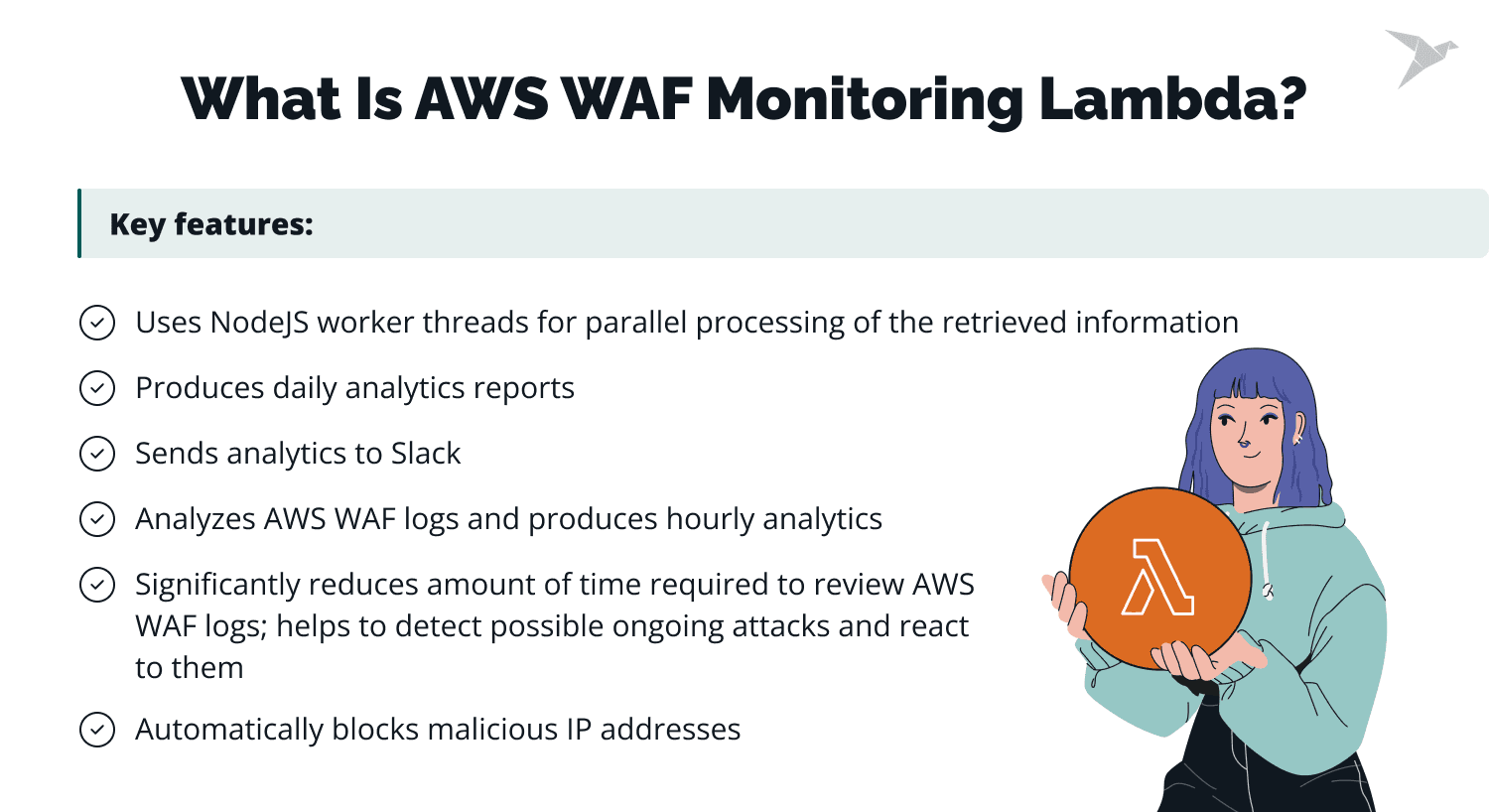
AWS WAF Monitoring Lambda operates around the clock, continuously analyzing WAF logs and generating valuable insights into blocked IP addresses and potential attacks. With its parallel processing capabilities, this tool efficiently handles multiple AWS WAF instances simultaneously, speeding up log analysis. Notably, it can also automatically block malicious IP addresses according to your pre-defined security criteria, helping to mitigate threats before they escalate.
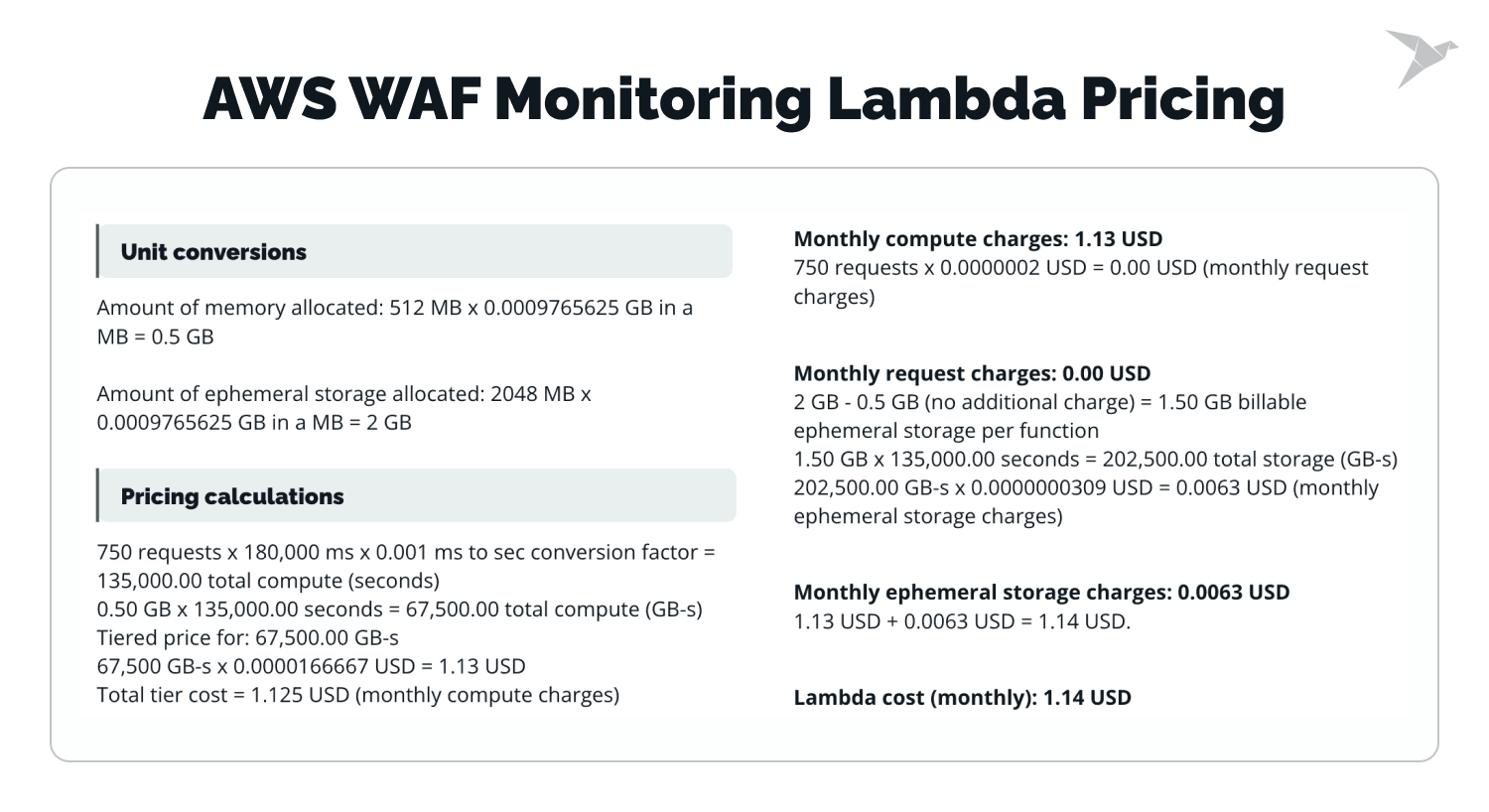
Let’s have a look at the key features of AWS WAF Monitoring Lambda:
Automated analytics production
Lambda functions are launched on an hourly and daily basis, interacting with the S3 bucket that stores your AWS WAF logs. These functions produce detailed statistics on IP blocks, attack patterns, and trends.
Customizable notifications
The analytics generated can be sent to any platform your team uses for monitoring, such as Slack. This allows your security team to receive real-time alerts and quickly respond to emerging trends.
Cost-effective monitoring
Although the solution incurs a modest monthly cost, the time and effort saved are substantial. With automating log analysis and reporting, your team can focus on improving security measures rather than manually sifting through data.
Additionally, AWS WAF Monitoring Lambda is open-source, making it accessible for you to test and integrate into your environment. You’ll also receive resources such as AWS WAF pricing guides and strategies for optimizing bot control, which can help keep costs in check while maintaining strong security practices.
For more details on this solution and additional cloud security tips, visit our blog, which offers a range of articles on cost-effective security measures for AWS environments.
Finally, here are some useful additional resources:
- AWS WAF Monitoring Lambda
- AWS WAF Monitoring Lambda Overview
- AWS WAF Pricing explained
- Optimizing costs for your bot control strategy
AWS Security Survival Kit: Proactive AWS Cloud Security
Victor Grenu has kindly shared his knowledge with us. So, let's get started!

When managing AWS environments, especially for development or training purposes, maintaining a strong security posture can be challenging. That's why the AWS Security Survival Kit was created.
AWS Security Survival Kit is an open-source solution containing AWS resources designed to provide minimal yet essential security alerting for your AWS account. Whether you are just getting started with AWS or need a lightweight security solution, this kit offers an easy-to-implement, cost-effective way to stay alerted to potential threats and misconfigurations.
So, what are the key features of the AWS Security Survival Kit? The AWS Security Survival Kit is equipped with twelve basic alerts that monitor common and potentially dangerous activities within your AWS account. These include:
- Root user activity. Alerts when your root user is used, which is not recommended for regular operations.
- CloudTrail modifications. Keeps track of any changes to your CloudTrail, which logs AWS account activity.
- IAM user actions. Monitors actions related to your Identity and Access Management (IAM) configurations.
- Container security issues. Detects vulnerabilities or security risks associated with AWS container services.
- Cloud shared exfiltration. Identifies suspicious network connections to your cloud shared resources, a recent addition to the toolset.
With AWS's shared responsibility model, many critical security settings are not enabled by default. The AWS Security Survival Kit comes with built-in security configurations to help you avoid common security pitfalls, such as:
- EBS volume default encryption. Ensures all Elastic Block Store volumes are encrypted by default. Encrypting data is a foundational AWS security practice.
- S3 block public access. Prevents your S3 buckets from being inadvertently exposed to the public.
- IAM public access alerts. Flags any cases where your identity and access management configuration could allow public access, which is often a security oversight.
These foundational security features provide a robust starting point for a secure AWS environment.
How AWS Security Survival Kit works
Deploying the AWS Security Survival Kit is straightforward, relying on two CloudFormation templates: one for global services and another for your chosen operating region. The templates configure CloudWatch rules that trigger alerts for suspicious activities. Notifications are sent through Amazon SNS (Simple Notification Service) to your communication platform of choice, enabling real-time alerts.
To get started, you’ll need to configure parameters like your email address, project name, operating region, and CloudTrail settings. Once set, deploying the kit is as simple as running a CLI command, with no further manual configuration required. The setup process takes just a few minutes, making it an efficient way to enhance your AWS cloud security.
One of the biggest advantages of the AWS Security Survival Kit is its cost-effectiveness. Running the system in a single AWS region costs less than $5 per month, and for accounts with low activity – such as training or development environments – the cost could be even lower. This affordability makes it an ideal solution for anyone seeking basic security alerting without breaking the bank.
Setting up the AWS Security Survival Kit
To set up the solution:
- Configure basic parameters. Provide your email, project name, AWS operating region, and enable CloudTrail.
- Deploy CloudFormation templates. Deploy two templates (one for global services, one for your region).
- Monitor alerts. Receive notifications through Slack, Microsoft Teams, or email.
- Explore documentation. Check the repository documentation for instructions on creating new features or submitting improvements.
The open-source nature of the kit allows for community contributions. You can check out the GitHub repository and even contribute by adding features or fixing bugs. Whether you’re an experienced developer or just starting out, this project offers a hands-on approach to improving your AWS security posture.
Sample alerts and notifications
There are alerts designed to notify you immediately through your preferred communication platform (email, Slack, or Microsoft Teams) via an integrated chatbot. The solution provides detailed notifications for each alert, containing information such as:
- Event time
- Event name
- Source IP
- IAM role used
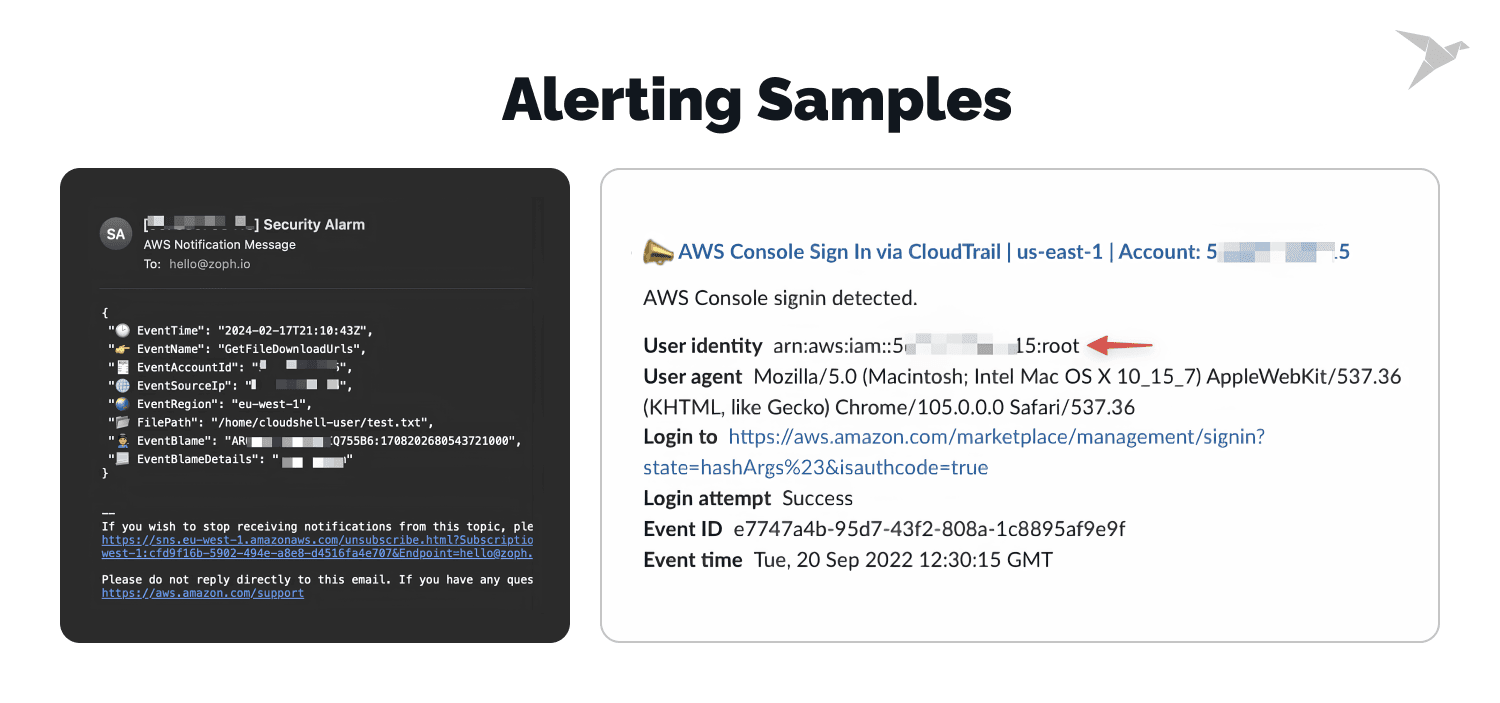
In addition to email alerts, you can view notifications directly in Slack, showing critical events like root account sign-ins or access denied messages. For a visual overview, the CloudWatch dashboard gives you real-time insight into detected events.
If you follow these simple steps, you can ensure that your AWS environment has a baseline level of security, which makes it easier to detect and respond to potential threats before they become costly problems.
Efficient AWS Compliance Tracking: Best Practices
In this section, Victoria Shutenko shares her valuable experience over the years of practice. Let’s start!

Ensuring compliance and security in AWS cloud environments is critical not only for building trust and reliability but also for avoiding regulatory penalties. Below are key tips and best practices for tracking compliance cost-effectively, using AWS-native tools alongside open-source solutions like Prowler.
Let’s look at some examples of compliance standards. They are:
- PCI DSS. Widely used in payment systems, it enforces network security, data protection, and vulnerability management to safeguard payment environments.
- NIST 800-53. Provides guidelines for managing access control, incident response, risk assessments, and continuous monitoring in critical infrastructures.
- CIS benchmarks. These benchmarks ensure best practices around identity management, logging, monitoring, and network security, particularly in AWS environments.
How AWS native tools help with compliance
AWS native tools can assist in staying compliant. Let’s see the most prominent ones!
AWS Security Hub
This centralized service integrates with both native and third-party tools, offering automated security checks and remediation options. It gives a comprehensive view of security findings and ensures your environment aligns with compliance frameworks.
AWS Config
A continuous monitoring tool that tracks changes in your AWS environment. It can be used to audit configurations and resource relationships, ensuring they comply with set policies and frameworks like CIS and NIST.
AWS Config pricing can vary based on the number of rules and configuration items. Optimize your AWS Config usage by reducing unnecessary configurations, prioritizing high-risk resources, and using managed rules.
Cost-saving tips
Let’s start with looking at AWS Config pricing:
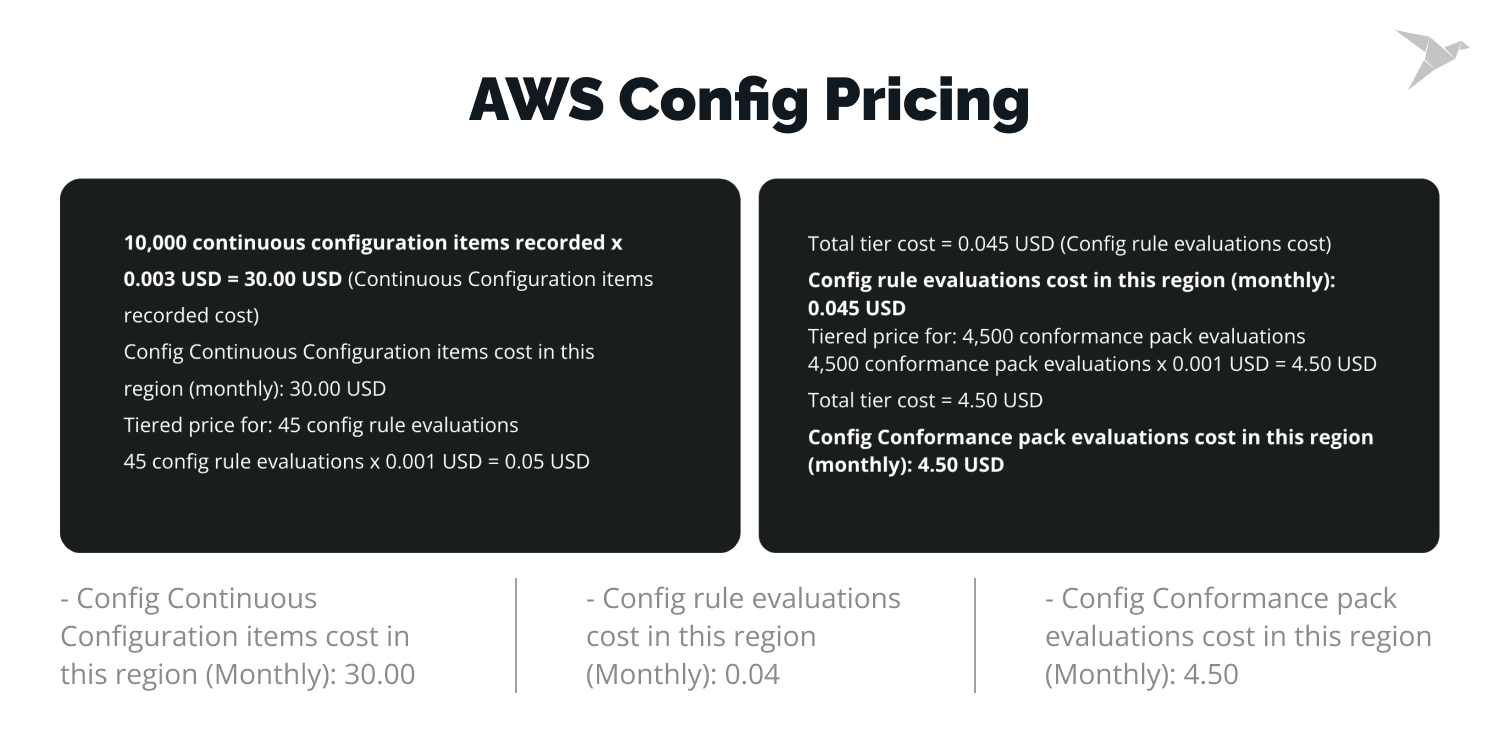
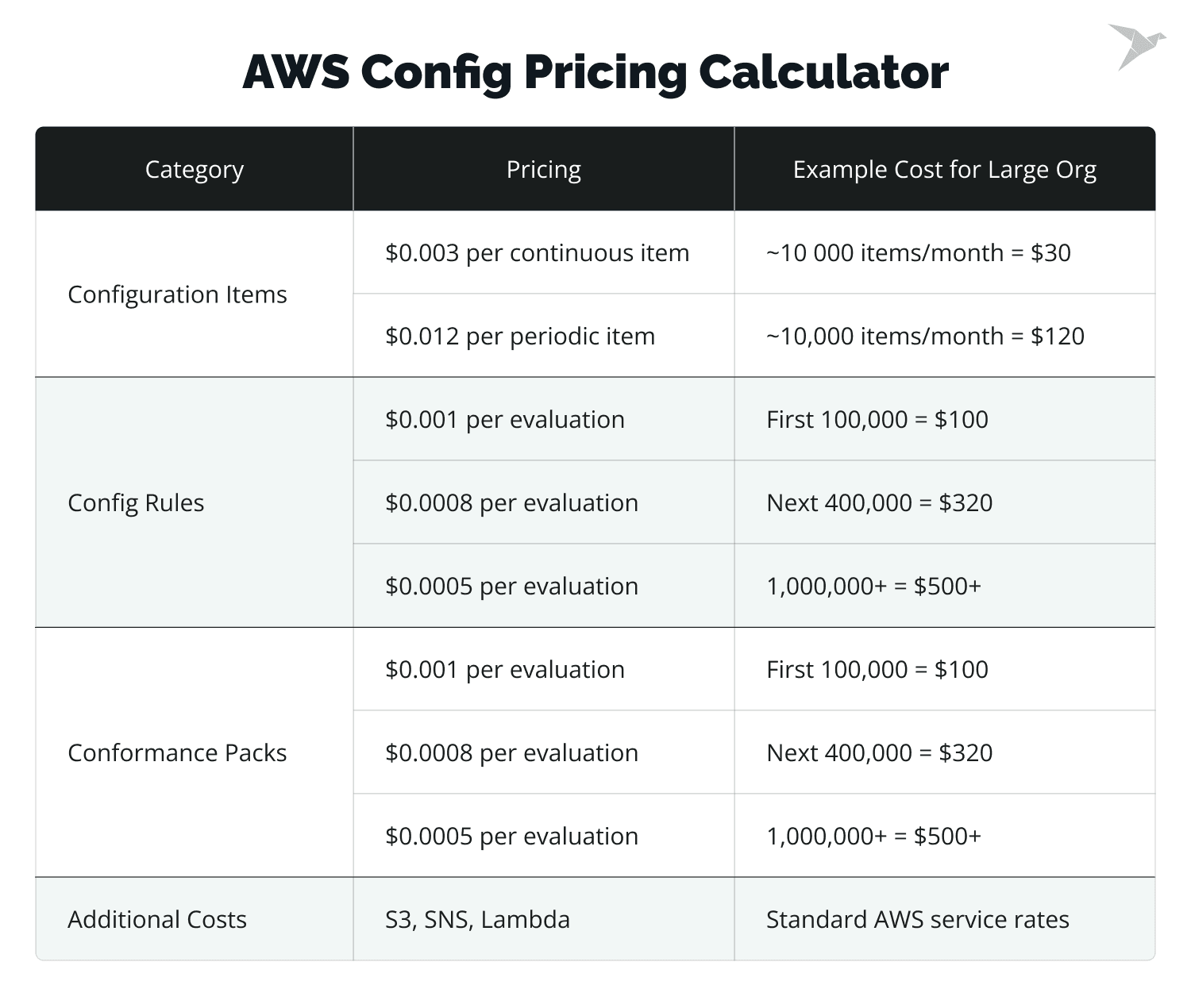
So, how can we save costs in AWS? Here are some recommendations:
Optimize rule evaluations
Consolidate rules and use AWS-managed rules to reduce configuration checks. Adjust the frequency of evaluations and use priority-based recordings to lower costs.
Use conformance packs efficiently
Customize and narrow down the scope of conformance packs to only include essential checks, reducing overall evaluations.
Consolidate billing and usage tracking
Leverage AWS’s consolidated billing to benefit from tiered pricing. Monitor usage regularly and set budget alerts to control spending.
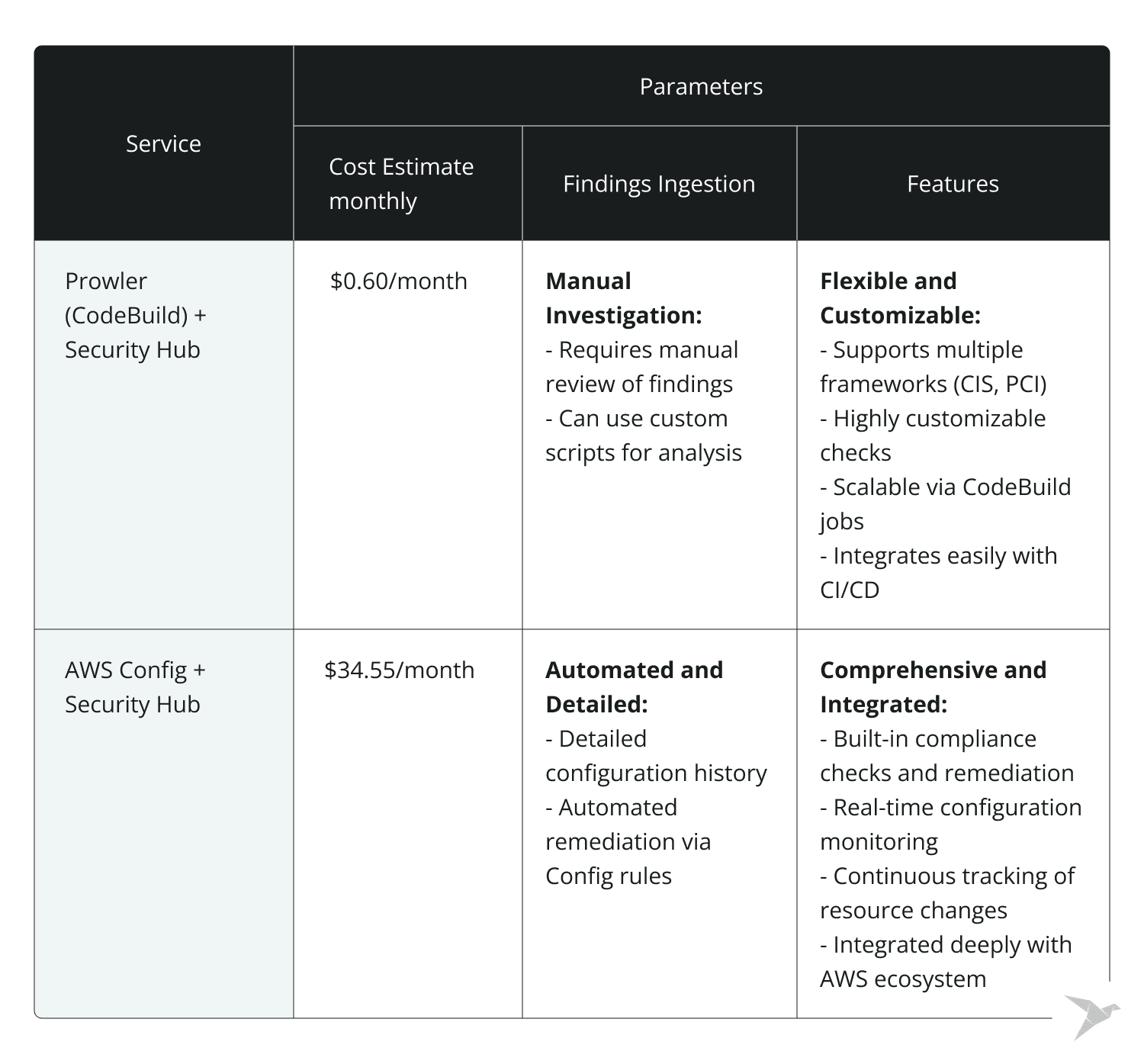
Prowler: A cost-effective compliance solution
Prowler is an open-source tool that runs AWS security assessments, focusing on cloud security best practices and compliance checks. It supports frameworks like PCI DSS, HIPAA, and GDPR, and integrates with AWS Security Hub.
Prowler’s continuous monitoring ensures that you stay compliant with evolving frameworks and can quickly adapt to security incidents. You can run Prowler from various environments like EC2 or CodeBuild to automate your scans and receive reports.
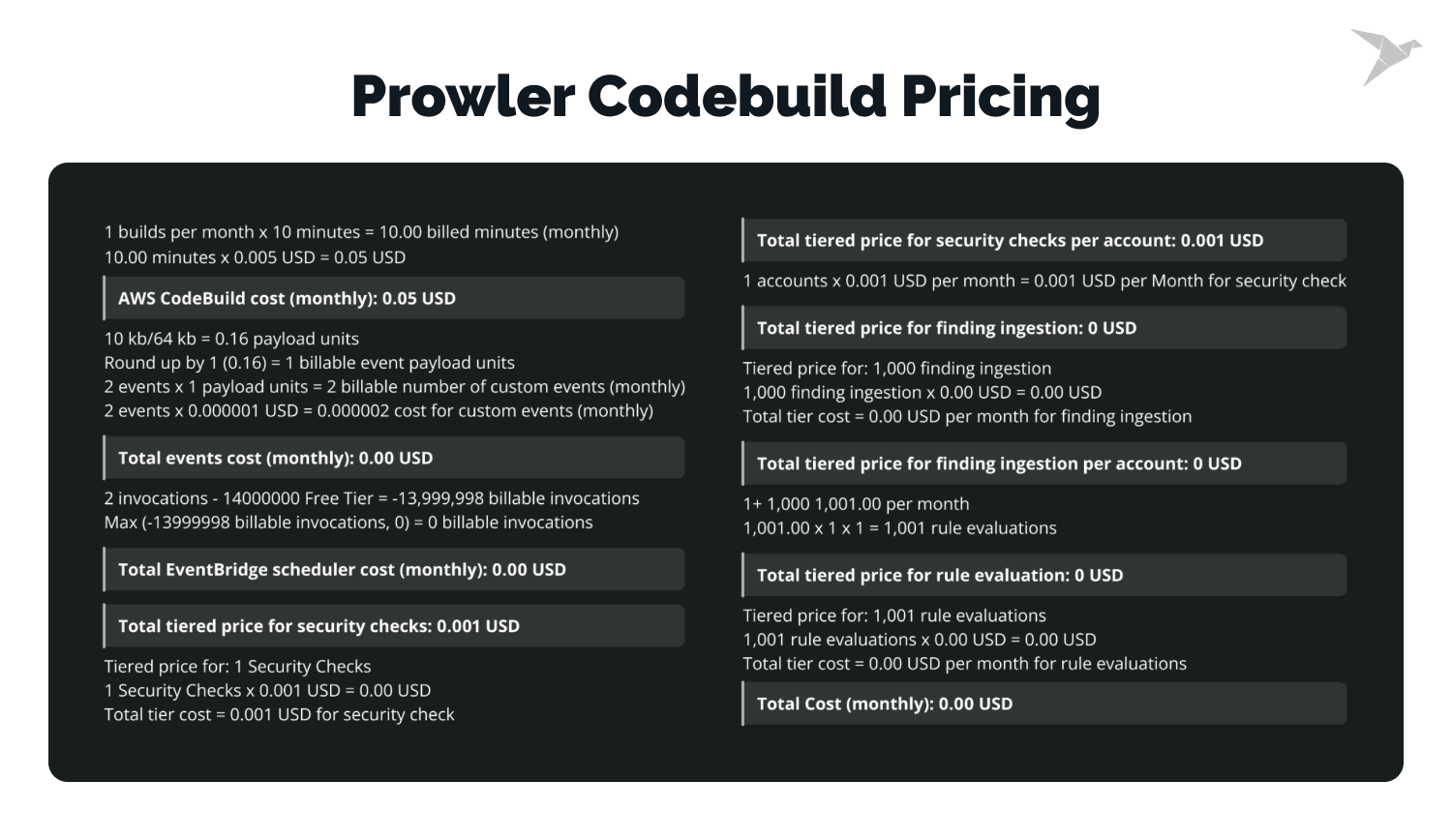
Prowler is a cost-effective solution, as running Prowler costs significantly less than AWS Config. For example, using AWS CodeBuild and EventBridge for monthly scans costs only around $0.60 a month in small environments. This makes Prowler a perfect solution for organizations on a tight budget that still need to maintain security compliance.
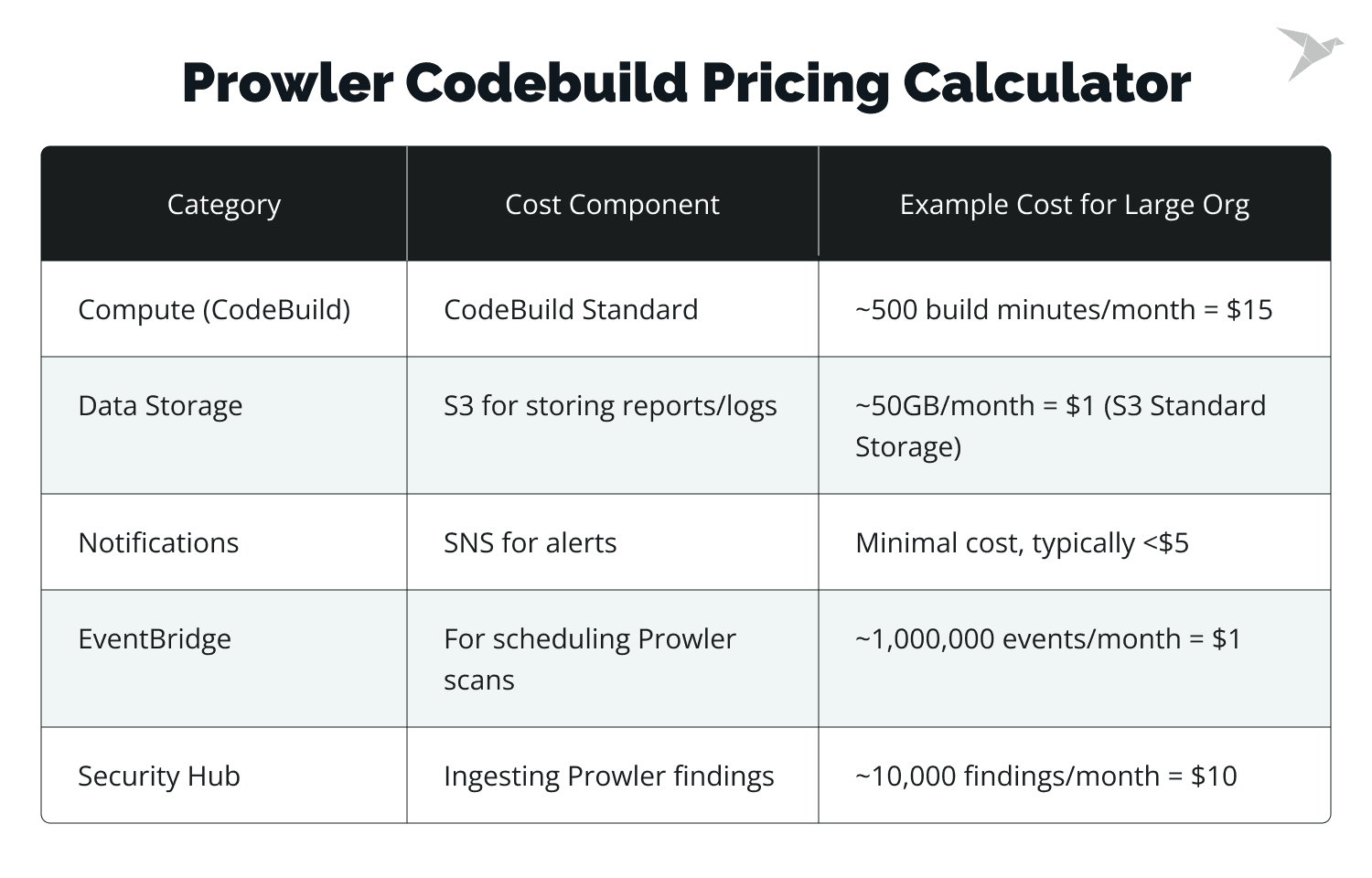
Let’s compare Prowler vs AWS Config according to key characteristics:
Customization and flexibility
Prowler is more flexible and customizable than AWS Config, allowing you to write custom checks and mute irrelevant findings. It’s highly recommended for organizations with a DevOps team that can handle custom setups.
Real-time tracking
While AWS Config offers near real-time configuration tracking and deeper integration with AWS cloud services, Prowler provides on-demand scanning, making it ideal for organizations that need periodic compliance checks without continuous overhead.
Integration with CI/CD pipelines
Prowler easily integrates with CI/CD pipelines, allowing security assessments during development cycles. AWS Config, on the other hand, offers automated real-time monitoring, making it a great solution for organizations seeking a managed, hands-off approach.
Cost comparison
Prowler offers a low-cost, customizable solution with minimal infrastructure overhead, ideal for small to mid-sized organizations. AWS Config, while slightly more expensive, provides fully managed services with automated configuration tracking and deeper AWS integration.
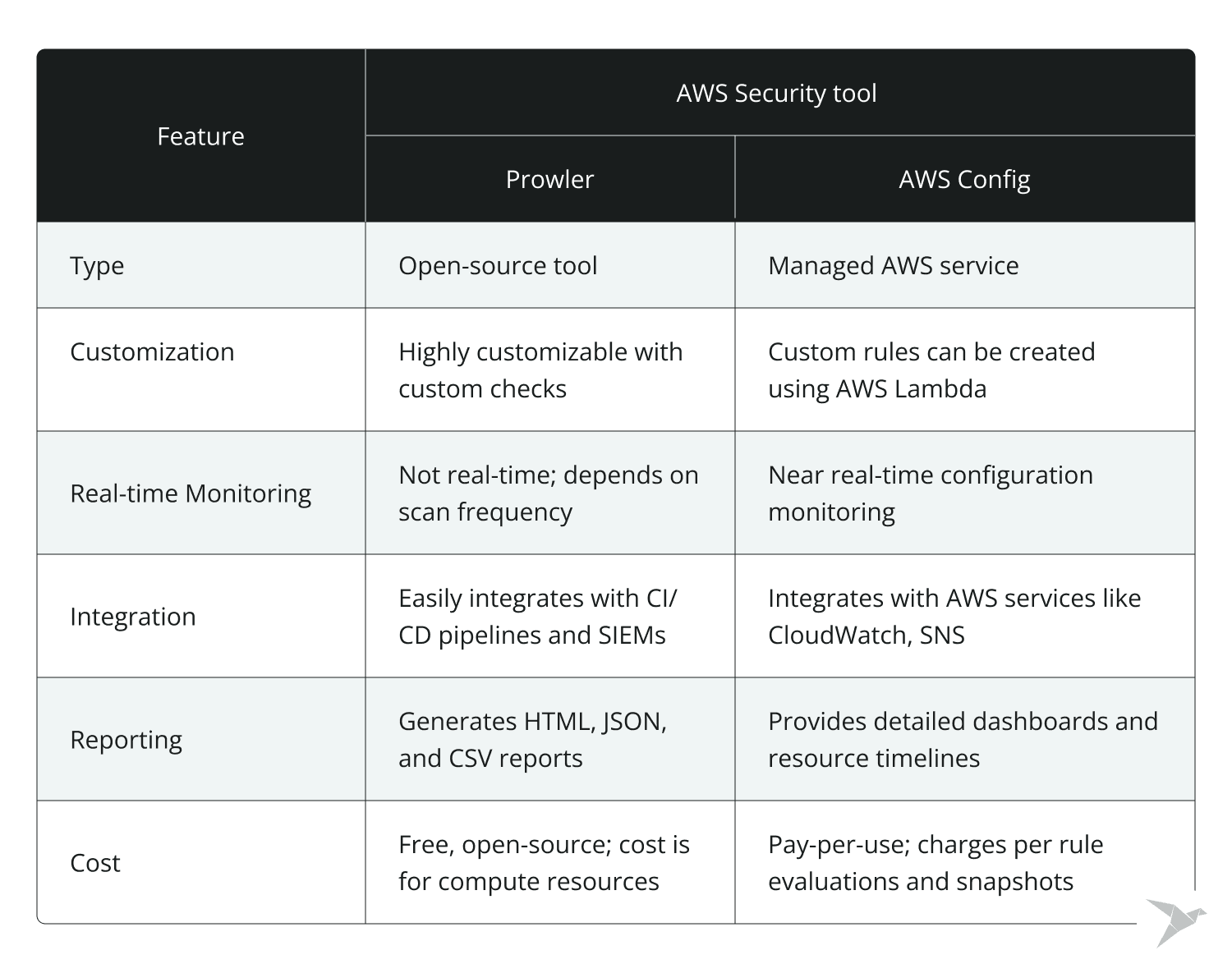
So, what to choose? A hybrid approach!
For optimal cost savings and security coverage, consider combining AWS Config for real-time monitoring with Prowler for customizable, detailed assessments. This hybrid approach gives you the best of both worlds – continuous oversight from AWS Config and the flexibility of Prowler for in-depth, framework-specific compliance checks.
Here are some useful additional resources:
AWS Security Tips and Tools From Cloud Security Architect
In this section, Rotem Levi, a cloud security architect, shares useful tips and insights on cost-effective AWS practices. Let’s dive in!

AWS WAF configuration: prioritizing rule order to optimize costs
When it comes to AWS WAF, setting up the rule order is critical. The right rule prioritization can significantly reduce unnecessary data flow through more expensive rules, effectively optimizing your costs. AWS WAF evaluates rules in the order they are listed, so carefully considering the sequence could result in substantial savings. This might seem minor, but rule order in AWS WAF can be the difference between an efficient, cost-effective security solution and an expensive one.
Budget alerts: harnessing cost insights to stay on track
Budget alerts can be a game-changer for cost management. They help monitor expenses in real time, flagging unusual spikes so adjustments can be made before costs get out of control. By setting budget thresholds, you maintain a proactive approach to cost control across your AWS resources.
Optimizing backup strategies with thoughtful governance
Creating a smart backup strategy is essential for both production and development environments. For example, production databases should be backed up at regular intervals, stored for a specified time, and adjusted based on business needs. In production, this might mean backing up every X interval with a retention period of Y, while in development or testing, you could back up every Z interval and store for a shorter period of M.
Services like RDS ChargedBackup, DynamoDB Backups, and Amazon DocumentDB can be costly if misconfigured, so establishing clear governance around backup frequency and retention time is vital to avoid unnecessary expenses.
Pre-configuration governance: essential steps to avoid misconfigurations and extra costs
A governance layer before configuring backup or storage policies is crucial. For example, if you set a retention policy of one week, you might store backups in Glacier or Deep Archive, but it’s essential to understand the minimum storage commitments. Missteps here can lead to wasted resources and higher costs. Knowing default settings for different AWS services – like CloudWatch Logs, which default to ‘never expire,’ or AWS Config, which records every activity by default – is critical for budget control.
To manage these costs effectively, always define your policy first, then determine the configuration that aligns with your objectives. For instance, if your policy is to retain backups for one year, Glacier might be your best choice. Each choice should align with your retention needs and budget constraints, helping to ensure cost-efficiency across your AWS environment.
The power of automation in cloud security
Automation is transforming cloud security, allowing organizations to manage threats more intelligently and reduce operational costs. If your team implements AI-powered automated security systems, it enables you to detect anomalies in real time, reducing the need for manual threat response. Thus, you concentrate on strategic tasks while the system continually monitors and mitigates potential issues, ultimately helping to prevent costly failures.
Optimizing cloud resources for security and savings
Effective management of cloud resources minimizes both costs and security risks. Many organizations unknowingly pay for unused services or duplicate security tools, which not only drives up expenses but also increases the exposure to cyber threats. Ensuring that each service is fully utilized and eliminating redundancies can save costs and reduce attack surfaces.
Leveraging AWS tools for cost-effective security and encryption
AWS offers a range of options that make security cost-effective, starting with encryption in S3. For example, if you need to encrypt S3 bucket files, using AWS Key Management Service (KMS) with S3-managed keys reduces encryption costs compared to custom KMS keys. It’s a practical choice that enables encryption without the steep price tag of fully customized solutions.
Beyond encryption, consider using cost-efficient tools for monitoring, observability, and security: Amazon CloudWatch, AWS CloudTrail, and AWS Config. In terms of security, resources like AWS CloudHSM, AWS KMS, AWS WAF, and Amazon GuardDuty offer scalable, cost-efficient security without overshooting your budget.
The AWS CUDOS Dashboard is invaluable for gaining insight into cloud usage and detecting irregular patterns. Features such as the Security Dashboard and Cost Anomaly Detection allow organizations to monitor security metrics and identify unusual spending patterns early, preventing unnecessary costs.
Implementing Service Control Policies (SCPs) helps block unused services, regions, and resource types, enhancing security by reducing the areas exposed to potential threats. A cost-effective approach to AWS security management starts with Service Control SCPs.
Blocking unnecessary services and regions not only strengthens your security posture by reducing attack surfaces but also lowers costs by eliminating avoidable spending on these services. It’s a straightforward and highly effective step in budget management.
Amazon CloudWatch efficiently manages logs but requires configuration to avoid excessive costs. Make sure to:
- Use Infrequent Access (IA) log storage for less critical logs.
- Automate log retention with S3 lifecycle policies to archive or delete older logs.
AWS CloudTrail provides visibility into user activity but can be costly if mismanaged. Use Organization Trails to consolidate logs across accounts, capturing a single free copy of management events.
CloudHSM offers high security for compliance, such as FIPS 140-2 Level 3, but should be used selectively. Make sure to limit CloudHSM usage to critical production environments to avoid high availability costs.
Methodology for cost-effective cloud security
Phase 1: Prioritize security tools based on needs
Identify the right tools for your specific workloads and compliance requirements. Start with tools like CloudTrail for tracking API calls and Config for monitoring compliance while only enabling critical services in essential regions.
Phase 2: Configure tools for security and efficiency
Optimize logging and compliance data across multiple accounts to reduce duplication costs. For example, CloudTrail organization-level trails and Config Aggregators can be used for multi-region data collection.
Phase 3: Continuous cost monitoring and optimization
Set budget limits with AWS Budgets and Cost Explorer, use tagging to track expenses by department or project, and apply data retention policies to manage costs effectively.
Phase 4: Automate security to reduce overhead
Integrate Config Rules and Security Hub to detect and respond to configuration drifts automatically. Connect GuardDuty with EventBridge to trigger automatic responses, reducing the need for manual monitoring and response.
All in all, adopting automation and cost-efficient practices in AWS security can enhance protection while maintaining financial sustainability. With structured methodologies and strategic use of AWS tools, organizations can achieve robust security aligned with their budget constraints.
Conclusion
Incorporating AWS security best practices is essential for protecting your cloud infrastructure without overspending. If businesses use AWS WAF, deploy automation through CloudFormation templates, and implement cost-effective tools like Prowler, they can achieve robust protection at no extra cost.
Focusing on smart rule management, logging, and compliance monitoring ensures both security and budget efficiency. Our hands-on experience with these practices has allowed us to streamline AWS security for a wide range of clients, optimizing their defenses while controlling costs.
If you're looking for professional help with your AWS security setup, TechMagic is here to assist. Contact us to discuss how we can enhance your cybersecurity strategy.

FAQ

What is AWS WAF, and why is it important?
AWS Web Application Firewall (WAF) is a managed service that protects web applications from exploits like SQL injection and XSS, helping to ensure the security and availability of sensitive data.
What are the main AWS WAF deployment options?
AWS WAF can be deployed manually, offering flexibility but requiring expertise, or through predefined templates like Security Automations, which simplifies setup and management.
How can I optimize AWS WAF costs?
Use CloudFormation templates for automated deployment, track Web ACL capacity units, and use efficient match statements (like regex) to reduce costs while maintaining security.
What’s the difference between custom and managed AWS WAF rules?
Custom rules offer flexibility but need expertise, while managed rules provide quick, out-of-the-box protection for common threats.
Why should IAM roles with temporary credentials be used instead of long-term access keys for programmatic access to AWS services?
For programmatic access to AWS services, it's recommended to use IAM roles with temporary credentials instead of relying on long-term access keys. Another step to securing your AWS environment is avoiding the use of root user credentials for daily operations.
How can I manage AWS WAF logs cost-effectively?
Use Amazon S3 or CloudWatch for logging, filter logs based on rule actions, and consider AWS WAF Monitoring Lambda for automated analysis and cost-effective security management.

 Software Development
Software Development Security Services
Security Services Cloud Services
Cloud Services Other Services
Other Services















 TechMagic Academy
TechMagic Academy